News
VMware Details Malware Threats in Linux Multi-Cloud Implementations
While Windows is generally seen as the most malware-vulnerable OS, cloud computing is mostly done on Linux, so VMware has published a threat report about malware in Linux-based multi-cloud environments.
Titled "Exposing Malware in Linux-Based Multi-Cloud Environments," the new technical threat report details unique characteristics of the top threats: ransomware, cryptominers and remote access tools (RATs). It's purpose is to guide organizations about:
- Existing characterization techniques and how to protect against more sophisticated malware
- Ransomware and cryptominer families that target Linux-based systems following their evolution and cross-pollination
- How to fight back against these threats with a combination of approaches, policies, and mechanisms
VMware said that while 90 percent of cloud runs on Linux servers, most countermeasures are for Windows, which leaves multi-cloud implementations vulnerable to malware attacks.
"Threat actors know that current malware countermeasures are mostly focused on addressing Windows-based threats, leaving many public and private cloud deployments vulnerable to Linux-based attacks," the report says. "These public and private clouds are high-value targets for cybercriminals, providing access to critical infrastructure services and substantial computational resources."
While the dense, data-laden technical threat report is heavy on nitty-gritty details (including downloadable datasets) and light on highlight takeaways and generalizations, VMware does offer some recommendations at the end, including adopting Zero Trust security model principles.
Zero Trust is emerging along with best practice techniques like regular system backups and using Multi-factor Authentication (MFA) in the fight against ransomware and other attacks that are regularly making headline news.
 [Click on image for larger view.] Zero Trust Principles (source: Microsoft).
[Click on image for larger view.] Zero Trust Principles (source: Microsoft).
The Zero Trust model eschews the standard security approach of walling off networks and systems behind a secure perimeter. It's one of the latest security darlings in an industry that has seen the advent of hybrid work models, the proliferation of endpoints and bring-your-own devices, disparate and interconnected systems spanning clouds and enterprise datacenters, and just general complexity all around. Instead of trying to secure perimeters, Zero Trust assumes that such fortress security approaches are destined to fail and that systems have already been penetrated, seeking to lessen the damage that can be caused.
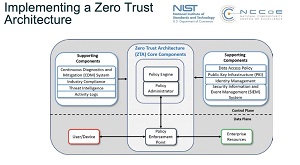 [Click on image for larger view.] Zero Trust Architecture (source: NIST).
[Click on image for larger view.] Zero Trust Architecture (source: NIST).
"A Zero Trust strategy can help organizations embed security throughout their infrastructure," the report says. "Zero Trust offers a connected approach -- joining users, devices, workloads and networks -- to help organizations systematically address the threat vectors that make up their attack surface. Organizations can ensure they are implementing control points and distributing security across the infrastructure to better protect data and operations. With visibility, context, actionable insights, and control points embedded throughout the environment, organizations can start to spot and stop many of today's threats before they can even get started."
The report also advocates for endpoint detection and response (EDR) solutions to monitor actions performed by processes on cloud workloads and implement segmentation to contain risks, along with a network detection and response (NDR) system that can recognize network-based evidence of attacks and malicious lateral movements, which ideally could block the malware before it effectively takes hold.
"Organizations need to think of security as an inherent and distributed part of the modern enterprise, which must be incorporated into all aspects of the environment," VMware said in its recommendations section. "Protecting multi-cloud environments starts with complete visibility into all workloads with detailed system context that makes it easier to understand and prioritize mitigation efforts. Information from all sources must be combined in an intelligent fashion that adds value, while enabling the sharing of this contextual data across teams to reduce silos."
About the Author
David Ramel is an editor and writer at Converge 360.