News
Threat Actors Organize: Welcome to Ransomware Inc.
"Many people still think of a ransomware actor as the proverbial 400-pound hacker in his mom's basement -- nothing could be further from the truth," says in-the-trenches security expert Allan Liska. "There are a number of cottage industries that have sprung up in support of ransomware."
In fact, the intelligence analyst at Recorded Future outlined a businesslike environment and workflow he has discerned from his more than 20 years in the IT security field, most recently focused on ransomware:
- Initial access brokers (IABs) gain the initial foothold into network
- "Customer service reps" man the negotiation chats for the ransomware groups
- Money launderers help hide the ransom payments through mixers and unscrupulous exchanges
-
Developers help build the whole Ransomware-as-a-Service (RaaS) ecosystem
"In fact, the leader of a ransomware group is often nothing more than a 'marketing' person whose sole purpose is to get more affiliates for the group," said Liska, who is known as the "Ransomware Sommelier."
He shared his thoughts with Virtualization & Cloud Review following his presentation in a recent multi-part online event titled "Modern Ransomware Defense & Remediation Summit," now available for on-demand viewing.
It's no surprise Liska started off discussing initial access brokers early on, as he has become somewhat of a specialist in that area. For example, last year he took to Twitter to lead a crowdsourcing effort to create a one-stop-shop for a list of initial access vulnerabilities used by ransomware attackers, as we explained in the article "'Ransomware Sommelier' Crowdsources Initial Access Vulnerability List."
Of course, organized ransomware has been a known thing for a while now, with even nation-state actors getting in on the action, but Liska and other security experts indicate the bad guys are getting more sophisticated.
"Outsourcing the initial access to an external entity lets attackers focus on the execution phase of an attack without having to worry about how to find entry points into the victim's network," said an article last summer in Infosecurity Magazine titled "The Rise of Initial Access Brokers," which noted the flourishing market often sees compromised VPN or RDP accounts as network inroads, along with other exposed remote services like SSH.
Digital Shadows also charted "The Rise of Initial Access Brokers" a year ago, complete with a chart showing popular access types and their average prices (note that prices have likely gone up with the recent inflation spike):
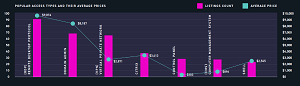 [Click on image for larger view.] Popular Access Types and Average Prices (source: Digital Shadows).
[Click on image for larger view.] Popular Access Types and Average Prices (source: Digital Shadows).
Liska detailed the initial access scene in his opening presentation, titled "The Current Ransomware Threat Landscape & What IT Pros Must Know."
"So one of the things that you have to understand with ransomware is it's generally not the ransomware actor that's gaining that initial access," he explained. "There are other criminals that are called initial access brokers, and they're the ones who generally gain that access. And then they turn around and they sell it to the ransomware actors themselves, whether it's to the operator of the ransomware-as-a-service offering, or whether it's one of their affiliates that people that sign up to be able to deploy their ransomware.
 "Think of it like flipping houses, except you're flipping networks. You're turning that network over to a ransomware actor who's then going to deploy the ransomware."
"Think of it like flipping houses, except you're flipping networks. You're turning that network over to a ransomware actor who's then going to deploy the ransomware."
Allan Liska, Intelligence Analyst, Recorded Future
"So when you're talking about an attack like this, you're generally talking about two different types of actors: one to get the initial access and one that turns around and sells it. Think of it like flipping houses, except you're flipping networks. You're turning that network over to a ransomware actor who's then going to deploy the ransomware. And they generally sell that initial access from anywhere from a couple thousand to 10, 15, even 100,000, depending on the type of access they're able to get -- so if you have administrator access -- and the size of the network. But you know, the thing is, if you're a ransomware actor, it's still a good investment. Because if you're confident you can deploy the ransomware you're gonna make way more than what you're paying for that initial access."
Liska explained he and other security experts are seeing four primary initial access vectors: credential stuffing/reuse; phishing; third-party; and exploitation, summarized in this graphic:
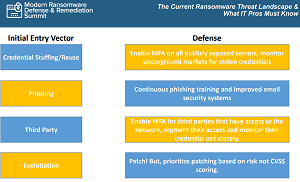 [Click on image for larger view.] Initial Entry Vectors
[Click on image for larger view.] Initial Entry Vectors
Phishing was the popular vector throughout 2019 and 2020, Liska said, but RDP (Remote Desktop Protocol) -- "low hanging fruit" -- is gaining traction. Here are Liska's thoughts on RDP, third-party attacks and exploitation:
RDP: "Ransomware Deployment Protocol"?
"What we're starting to see in 2021 -- and we expect this to continue into 2022 -- is that credential stuffing and credential reuse attacks are becoming much more common," Liska said. "In fact, we kind of have a joke in the industry that RDP actually stands for ransomware deployment protocol, instead of what it actually means, only because RDP is one of the most common entry methods. Because it's so easy for these initial access brokers to just fire up an old laptop and start scanning, looking for open RDP connections, and then trying credential stuffing/credential reuse attacks. You have to keep in mind, there are literally billions of credentials that are being sold on underground markets.
"So while it seems like a credential use attack would be a challenge, it really isn't. You connect to the RDP server, you see what network it belongs to, you search on Genesis market or one of the other markets for usernames and passwords that match it. And then you try those -- you get 100 of them -- you try them and unfortunately, most the time, they will find a match, and they'll be able to gain access. That's why Multi-Factor Authentication is so important for any system that's exposed to the internet."
Third-Party Attacks
"These are increasingly common," Liska said. "We really saw this take off in 2021. So a ransomware actor, or the initial access broker, gains access to a managed service provider, or a vendor of some kind. And rather than [deploy] the ransomware on that vendor, what they do is they use that access to jump to those partners. They find it's really easy, because you get to start right in the gooey center, and work your way out. So we're seeing a big increase in that. And again, that goes with the sophistication and increasing sophistication of the ransomware access."
Exploitation
"And then exploitation is also growing in popularity," Liska continued. "So, you know, in the last year, we catalogued more than 40 different exploits that were used by ransomware groups or the initial access focus in order to gain that first access. So it's really, really important that you're patching. Again, anything that's public facing, especially anything that has proof of concept code, or anything like that release, has to be patched immediately."
RaaS: Ransomware-as-a-Service
One striking fact that speaks to the businesslike organization of ransomware are numerous RaaS operations that have sprung up around the globe, as Liska's chart below shows:
 [Click on image for larger view.] Ransomware Has Gone Global
[Click on image for larger view.] Ransomware Has Gone Global
Cybersecurity specialist Rubrik, in a ransomware compendium, says of RaaS: "Criminals don't have to create their viruses anymore. Developers will create ransomware for a fee or share of the profits, creating a whole new industry that caters to ransomware." Also, the company noted a growing ecosystem of dedicated infrastructure has formed to support ransomware, including "bulletproof" hosts who will refuse to take criminal users offline, along with dedicated networks to help criminals avoid anti-virus software and move and hide virtual currency payments.
Liska shed more light on RaaS. "These are just some of the known cases of where we saw arrests for ransomware-as-a-service operators," he said of his global chart above. "So the affiliates, not necessarily the operators, we saw several in Canada, we saw Red Swan as a service affiliate arrested down in Florida. There were like four arrests of Canadians involved in ransomware activity. And I'm pretty sure only six people live in Canada, so, you know, that's like three quarters of the country or something like that. [Editor's note: Liska's views on the population of Canada are in no way representative of our views on the population of Canada. 😊].
"Anyway, it's a whole lot of people coming out of Canada that seem to be involved in ransomware as a service, which is kind of surprising. We saw some activity out of Brazil, out of Ukraine, out of Romania, certainly out of Iran, out of China, out of South Korea. And there's always activity out of North Korea, and of course, Russia. So really, when we talk about ransomware being global, we really are saying that it's global. Again, the the main operators of the ransomware itself, and we'll talk about this in a minute, are primarily in Russia, China and Iran. But the affiliates, the ones that are carrying out the attacks day to day, they're really spread out all over the world. And that's what we're learning from these law enforcement actions that have happened."
The Last Word on Initial Access
"So you can see already the challenge that defenders have, right? You have 30 different ransomware groups that that are really active right now. And then hundreds of initial access brokers that are working for these ransomware groups, all going after initial access using these four different methods. And there you see where the problem is when you're trying to defend that initial access. So that's initial access. Once they get in the network, then they start moving, they start moving around, and we see these same tools being used over and over again, by these ransomware groups, once they're in the network to move around."
One of the popular tools to do that is Cobalt Strike, said Liska, who went on to talk about how that tool and many other specific tools are used in attacks on targets like Linux servers and ESXi servers, the latter of which he said "have become really popular with ransomware groups."
Liska also discussed how to detect activity in the reconnaissance, lateral movement and exfiltration stages of an attack, the importance of proactively hunting for new threats on the network, how to deal with partners after an attack (they may just cut you off from their systems right away) and much more in his one-hour presentation.
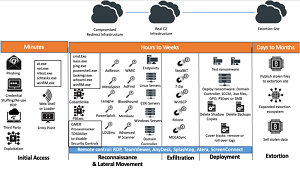 [Click on image for larger view.] Attack Stages
[Click on image for larger view.] Attack Stages
"So have a plan in place for how you're going to deal with this," he advised the hundreds of attendees in his conclusion. "Especially if you're not paying the ransom, what you're going to tell clients. In the case of schools, what you're going to tell parents, because we've been see parents getting emails from some of these attacks, and teachers and so on. So again, things to think about, things that are really, really important. And that has to be part of your ransomware incident response plan.
"So in summary, kind of where we are right now, ransomware attacks aren't slowing down in 2022, you've got to be prepared for changing tactics. So you have to keep updated on everything that's happening. Whatever you think you can detect, you want to test that; you want to make sure you can do that. And the best way to do that is to run tabletop exercises, to test both your detection and response. Know who and when you're going to call. Make sure that your PR team and your HR team are part of your incident response plan, so they know who's going to get called and when they're going to get called. What the messages -- you want to keep the whole company on the same message. And plan for the worst-case scenario and hope that it never comes to that. Hope that you're never a victim of ransomware, and that you're able to be successful, and your detections actually work as advertised."
As mentioned, while last week's summit is available for on-demand viewing, actually attending such events live brings many advantages, including the ability to engage in one-on-one discourse with front-line experts (not to mention the chance to win a cool tech prize). With that in mind, here are some summits coming up for the next month or so: