News
Cloud Security Report: It's Still Misconfiguration, Misconfiguration ...
Misconfiguration was still the No. 1 cause of cloud security incidents last year, says a report from Check Point Software Technologies.
Check Point said the study "revealed that cloud security incidents were up 10 percent from the previous year with 27 percent of organizations now citing misconfiguration, way ahead of issues like exposed data or account compromise."
Misconfiguration mishaps have been a thorny security problem for years, with user settings often leaving data exposed to the world on cloud storage buckets, for just one example.
As we reported last year in the article "Misconfigurations Continue to Plague Cloud Security, New Reports Say", the problem was especially prevalent years ago when Amazon Web Services (AWS) was bedeviled by a series of high-profile and highly publicized data breaches due to user misconfigurations. Many misconfigurations allowed access to S3 buckets, while others had to do with firewall misconfigurations.
AWS and other cloud giants fought the problem with user education and guidance, publicity and what tweaks they could make to keep users from sabotaging themselves, but as this new report shows, mitigation efforts have been less than totally successful.
The misconfiguration issue was one of three main highlights of the report as called out by Check Point:
- Organizations are continuing to adopt the cloud, with over 25 percent of respondents reporting 50 percent of their workloads in the cloud.
- Surveyed companies are still struggling with the lack of expertise that bridges security and DevOps. Only 16 percent of respondents have comprehensive DevSecOps in place, with 37 percent starting to incorporate some aspect of DevSecOps within the organization.
- Managing multiple cloud vendors has created a greater complexity than first imagined with misconfiguration seen as the number one security related incident.
Furthermore, the Education/Research sector was hardest hit by cyberattacks in 2021, reveals the company's 2022 Cloud Security Report, based on a survey of 775 cybersecurity professionals.
"Cyberattacks are up by an average of 50 percent since we issued our last annual report, with the education and research sector suffering the biggest blow, averaging 1,605 attacks every single week throughout the year," the report says. "As predicted, the infamous SolarWinds breach appears to have kickstarted a trend of supply chain attacks that have persisted throughout the year, showing no signs of slowing down."
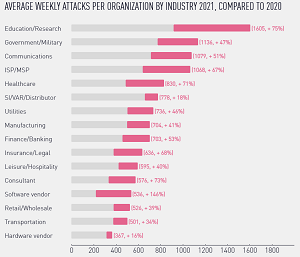 [Click on image for larger view.] Average Weekly Attacks Comparison (source: Check Point Software Technologies).
[Click on image for larger view.] Average Weekly Attacks Comparison (source: Check Point Software Technologies).
As the above graphic shows, the Software Vendor category shows the largest year-on-year growth, increasing 146 percent. "The rise in attacks against software vendors goes hand-in-hand with the ever-growing trend of software supply chain attacks observed during 2021," the company said.
Other findings show the top malicious file types in web and email, both vectors led by .exe, .pdf and .doc file types (discounting "other"):
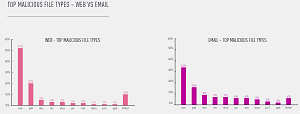 [Click on image for larger view.] Malicious File Types (source: Check Point Software Technologies).
[Click on image for larger view.] Malicious File Types (source: Check Point Software Technologies).
"The charts above indicate that the email attack vector has steadily established itself as a favorite, compared to slowly diminishing use of websites to distribute malware payloads since the beginning of 2020," the report says. "Whether used in a targeted attack, or as part of an opportunistic campaign by a novice attacker, email-based attacks allow for the easy distribution of malware to a wide array of targets and corporations.
"One of the reasons for this rise in email-based attacks is the massive number of high-profile campaigns sponsored and run by large crime groups, who distribute the most prominent malware families today, such as TrickBot, Dridex, Qbot, IcedID, or Emotet. Once these gangs realized the effectiveness of spam campaigns with malicious Office document attachments, they used it almost exclusively as their main infection vector into new networks."
Continuing the email vs. web comparison, this graphic shows comparative distribution protocols during 2019, 2020 and 2021:
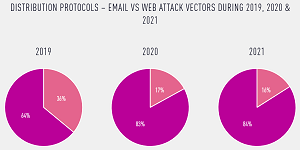 [Click on image for larger view.] Email vs. Web Distribution Protocols (source: Check Point Software Technologies).
[Click on image for larger view.] Email vs. Web Distribution Protocols (source: Check Point Software Technologies).
While all of the above came from just the Global Statistics segment of the comprehensive report, other chapters focused on major events and trends in 2021, an exploration of the revival of Emotet malware, high-profile global vulnerabilities, advice for achieving better security and a description of malware families.
"As organizations continue to adopt the cloud, with 35 percent running more than 50 percent of their workloads on the likes of Azure, AWS, and GCP, they struggle to manage the complexity of securing their cloud infrastructures across multiple cloud platforms, while also suffering a cyber-skills and knowledge shortage," Check Point said in a March 2 news release.
Furthermore: "Organizations are struggling to bring security into the DevOps cycle, compounded by a skills shortage witnessed by 45 percent of companies. Only 16 percent of respondents said they had comprehensive DevSecOps in place and 37 percent were just starting to implement DevSecOps into their cloud application development process.
"Further adding to the complexity of multi-cloud security, respondents ranked ensuring data protection and privacy for each environment at 57 percent, having the right skills to deploy and manage a complete solution across all cloud environments at 56 percent, and understanding service integration options at 50 percent.
"There is also an increasing need to deploy application protection in the cloud with this capability going up by 11 percent in the last year to become the 3rd highest area of focus, quoted by 53 percent of the survey sample. According to the report, 57 percent of respondents say that they expect to run more than half their workloads in the cloud within the next 12 to 18 months and, of those, some 76 percent were using two or more cloud providers."
About the Author
David Ramel is an editor and writer at Converge 360.