News
Q: How Often Should SMBs Do Security Audits with Zero Trust? A: Constantly
John, an IT pro at a plastic fabrication company, had a question for our Zero Trust security experts: How often should a SMB (100-150 employees) do security audits? Dave, a front-line consulting veteran, had an answer: Constantly.
"I believe that traditionally we would do either annual or biannual security audits," replied Dave Kawula of TriCon Elite Consulting. "And that definitely is not good enough anymore. So I believe that for the security posture that we have, we need to have what I call real-time insight and visibility into those configurations in those settings."
That exchange took place during last week's Zero Trust 101 online summit put on by Virtualization & Cloud Review and RedmondMag.com, in which Kawula was joined by John O'Neill Sr., chief technologist at AWS Solutions, who helped answer audience questions during their session of the multi-part event, "Understanding Zero Trust & Why It's Key for Enterprises in 2022 (and Beyond)."
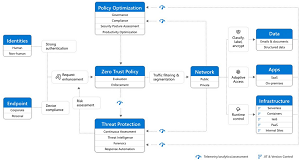 [Click on image for larger view.] Zero Trust
[Click on image for larger view.] Zero Trust
Kawula continued his reply: "So that if we get alerts coming out that there's a new zero day, we need to know what part of our landscape that that's impacting. So real-time vulnerability assessments and threat protection solutions are what you need. If it's something that's going to be done like once a month, or once every six weeks, or somebody comes in and runs a scan for you, that doesn't cut it anymore.
 "Because I tell you, the bad guys work 24 hours a day and 365 days a year. They don't stop, they don't sleep, they'll come at you at any hour."
"Because I tell you, the bad guys work 24 hours a day and 365 days a year. They don't stop, they don't sleep, they'll come at you at any hour."
Dave Kawula, managing principal consultant, TriCon Elite Consulting
"Because I tell you, the bad guys work 24 hours a day and 365 days a year. They don't stop, they don't sleep, they'll come at you at any hour. And so we need to make sure that we know what holes are in our infrastructure at any given point in time. So I would say that you need real time in today's world that we live in."
While the duo of Kawula and O'Neill Sr. shared their front-lines expertise in a slide-driven presentation in their one-hour segment, they emphasized the give-and-take interaction with the audience of hundreds, who submitted questions from their meeting consoles. The presenters like to take the questions as they come in. "So if you have any burning questions," Kawula said, "you don't have to wait until the end of the session. John and I'll try to take those kind of mid flight as we go."
O'Neill Sr. agreed. "Take questions and really have a conversation because, you know, we are a community and we are in a new era with the security events that are going on," he said. "And I feel like it's more important than ever that we share, we collaborate, we communicate with one another."
With that in mind, here are a couple more questions they handled.
Scott, from IT service management company: What are some questions that I should ask when I'm selecting vendors to implement the components of Zero Trust in my organization?
O'Neill Sr.: "This is huge. It's a great question, Scott, thank you, because every vendor, of course, they want sales. So they want to tell you they can do everything and deliver everything.
 "But you need to remember that in most cases, the vendor doesn't share the level of risk you do."
"But you need to remember that in most cases, the vendor doesn't share the level of risk you do."
John O'Neill Sr., chief technologist, AWS Solutions
"But you need to remember that in most cases, the vendor doesn't share the level of risk you do. They may lose you as a customer if something goes wrong, you may lose significant amounts of revenue, significant amount of capability, all that kind of thing. So it isn't really a shared responsibility model.
"So one of the things that I ask them, particularly when it comes to a security vendor, so say it's a firewalling, vendor, that kind of thing, and I ask them, 'How do you engage when we -- as your customer, your IT pro -- when we think we have a problem? And we don't know what's going on? Or whatever? How do you engage in that?' And so to give an example, with a firewall vendor, if their engagement is where 'you call tech support, and if it's a firewall issue, we're going to help you.' That's a non starter from what I want -- somebody who says, 'Hey, I'm your account executive. So yeah, open up that technical support case, but get with me and I will have it escalated. And you know, even if it isn't in the firewall we'll try and help you understand how to look at traffic in the firewall to see, or look at those logs. How did it get in? Which endpoints did it touch? Anything we can do to help you, we're willing to do it.'
And absolutely ask them, 'Are you willing? Do you have a history of working with other vendors?' Because when an event occurs, you may have to bring together members of your endpoint management team, your intrusion prevention team, your firewall team. They may not all be one provider. And in fact, I think sometimes you end up with the best situation when they aren't. So you know, ask them how they're going to be there for you, beyond just selling you that product, or that piece of the puzzle."
John from the plastics company again: Is there a specific RMM [remote monitoring and management] option you suggest? We currently have TeamViewer and I hear it is not as secure.
Kawula: "One of the things that I recommend with any of those RMM solutions, to help you lock them down, is to make sure that you are taking and setting up Single Sign On so that you can control those accounts. Because then your conditional access policies that you have are in play, trying to authenticate across to those partner solutions."
O'Neill Sr.: "John, another great question. Thank you so much. I'll kinda stick to some of the publicly available stuff. I agree with you that Team Viewer has some publicly disclosed history of security risks and that kind of thing. It was designed ... its original premise -- as many of the RMM solutions were -- was for convenience for IT pros. And unfortunately, the security parts of it haven't evolved. They have a history of some known attacks coming out of some of the areas of concern right now, with China and other state-sponsored things. So rather than mention a specific product that I like, because there's a number of them out there, I will, like Dave did, kind of give you a tip on something that I always look for in a solution I'm gonna use. It has to be an interactive exchange between the user and the IT pro, at least to initiate the contact.
"And I know that can be inconvenient. Sometimes IT people are like, 'Well, no, I need to remote into the machine' when people aren't as adept, and that kind of thing. You need to understand the risk you're putting yourself at when you choose that, because you are accountable for that risk. So in our situations, we always have an interaction with the client before we remote in. So even if it's a deferred, remote session, we make them kind of log in and acknowledge something and complete that handshake process before we can get in, and we really like that kind of solution."
Now available for on-demand viewing, their session also delves into exactly what Zero Trust is, what are its tenets, what are the real-world best practices (and gotchas) and what else do IT managers need to know. Specifically, they explain Multi-Factor Authentication (MFA), Privileged Identity Management, Just-in-Time Access, cloud concerns and much more. The summit also features a presentation by Ian Thornton-Trump, CISO at Cyjax, who addresses many other aspects of Zero Trust in his discussion of "Understanding Zero Trust & Why It's Key for Enterprises in 2022 (and Beyond)".
The live Q&A is invaluable, though (not to mention the chance to win a great prize), and more tech summits are coming up that will allow one-on-one interaction with well-known experts, including:
About the Author
David Ramel is an editor and writer at Converge 360.