In-Depth
In Depth: The Defender Family Is Growing
Two proud parents, Microsoft & Security, present the newest additions to their growing family: Microsoft Defender Threat Intelligence and Microsoft Defender External Attack Surface Management.
In this article, I'll go deep on what these two services offer, how they fit into the overall family of Defender products and why you should consider if they might be a good fit for your organization.
Knowing Your Enemy
"If you know the enemy and know yourself, you need not fear the result of a hundred battles. If you know yourself but not the enemy, for every victory gained you will also suffer a defeat. If you know neither the enemy nor yourself, you will succumb in every battle." -- Sun Tzu, "The Art of War."
I remember being on stage in New Zealand some years ago delivering training and predicting that the strength of a security service in the future would depend largely on the volume of signals gathered by an organization and their ability to synthesize insight from them. Microsoft's latest number is that they analyze 43 trillion signals daily (up from 24 trillion in February 2022).
Understanding the attack landscape, why criminals (and occasionally, nation states) are going after your business takes different shapes for different sizes of organizations. For an SMB, it's enough to know that criminals are after your users' identity and access, probably to ransomware your organization or to steal your data for extortion. But for larger enterprises, understanding the bigger picture and most importantly the daily changes is important. To me, there are two different types of Threat Intelligence (TI). The first is a feed of malicious IP addresses, domains/URLs and file hashes that can be feed into endpoint/firewall and cloud protection services to catch known bad stuff. The other is articles and deep information on different threat actors (Advanced Persistent Threat, APT, groups) and their changing tactics and techniques, which may feed in the first type of TI after being analyzed. Microsoft Defender 365, the umbrella term for Defender for Office, Defender for Identity, Defender for Endpoint and Defender for Cloud Apps has offered this for some years, both as a "behind the scenes" service to flag known bad files, sites and so on, and up-to-date information on new threats in the Threat Analytics Dashboard.
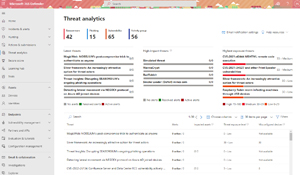 [Click on image for larger view.] Defender 365 Threat Analytics Dashboard
[Click on image for larger view.] Defender 365 Threat Analytics Dashboard
The challenge with the first type is that it's very time sensitive. The IP address that was OK yesterday might be malicious today (and OK again in a few days), and if you're not careful it might result in a lot of false positive alerts, wasting analysts' time. The difficulty with the second type is that it's very time consuming to really make sense of the data, analyze how it's relevant to your particular business and build detections based on it. For large, cybersecurity-mature organizations, it makes perfect sense to have one or more high-quality feeds to really "know the enemy" as Sun Tzu said. But for the rest of us, it tends to be an overwhelming fire hose of information that doesn't really give us actionable insights.
Meet Microsoft Defender Threat Intelligence
Can the new Microsoft Defender Threat Intelligence (MDTI?) service, based on Microsoft's acquisition of Risk IQ, make both these challenges a better experience?
MDTI will be integrated behind the scenes into Defender 365, Microsoft Sentinel and Microsoft Defender for Cloud, surfacing relevant TI and insights throughout those services. Risk IQ was known for "scanning the entire internet" to gather signals, so one way this will improve investigations is through linking external TI data to an incident to give analysts more context around a potential attack. Tying back malicious IP, domains and entities to an attacker allows you to block them quicker during incident response. The data sets on offer in MDTI are listed here, for example providing current and historical WHOIS information, certificate information or cookie information for crawled web sites. Surfacing this contextual information during an investigation of an incident is going to be very useful.
The dashboard allows you to work as a team on investigations. You can take it for a spin today. Just log in with an Azure AD or personal Microsoft account to https://ti.defender.microsoft.com/. Currently there are 1,807 different articles on offer.
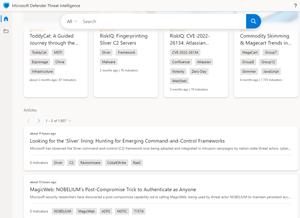 [Click on image for larger view.] Defender for Threat Intelligence Dashboard
[Click on image for larger view.] Defender for Threat Intelligence Dashboard
There are two versions of MDTI: the free community edition and Premium. The latter comes with a 30-day trial (for five users) and weighs in at AUD $5,720.80 per user per month (approximately $3,989 USD). This is not a cheap solution, and this pricing clearly aims this at the enterprise market. Premium unlocks projects, whereas analysts can work together on shared projects, the community version only lets you gather information and data in your own projects. Also, as mentioned, it really is only large and mature security teams that benefit from this type of TI.
Comparing the information you get with community vs. Premium, the latter adds a reputation score (1-100, higher means it's more suspicious) and cookie information, including showing other sites where that cookie is used. You also see more historical DNS data and WHOIS information is only shown with Premium. There are also more articles in Premium, as they're released to the community version after some time.
Each TI article comes with a description, public indicators and Defender TI indicators (if you have Premium licensing). You can download the indicators in a .csv file, as well as share the article via email or a link.
It's early days for MDTI as Microsoft integrates RiskIQ's PassiveTotal product into the Defender portal. At this stage, there's no API available, which means there's no easy way to feed the indicators from MDTI into Sentinel (doing it manually with the CSV export option would be very time consuming) and this to me is the biggest blocker. I have Sentinel deployed for several SMB clients, and the other worry would be if Microsoft only opens this integration for Premium subscribers.
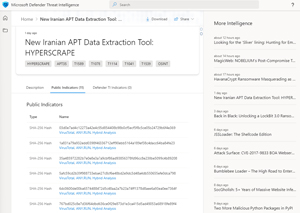 [Click on image for larger view.] Defender for Threat Intelligence Article
[Click on image for larger view.] Defender for Threat Intelligence Article
Say Hello to Microsoft Defender External Attack Surface Management
The second new service also ties directly into the Sun Tzu quote. If MDTI is about knowing the enemy, Defender External Attack Surface Management (MDEASM?) is all about knowing about your organization's assets -- from an attackers perspective. Also built on a RiskIQ product, this service is available in Azure; simply search for it in the portal and you can start a 30-day trial.
This is also (mostly) an enterprise-focused service. There have been many situations where a business has been compromised through a forgotten test server with an open port or a marketing web site for a long-since-forgotten campaign that no one remembered to delete. As an enterprise grows, this attack surface likewise grows, and I've seen presentations by "white hat" hackers finding hosts or IP addresses of an organization that are less protected (generally because the IT/Security team didn't even know they existed) and penetrating the organization that way. Or this business that got "ransomwared" through a single server with RDP open to the internet.
MDEASM is about mitigating this problem. You give it some seed information for the organization and it'll gather data on its domains, hostnames, web sites, IP blocks/addresses, ASNs, TLS certificates and WHOIS information.
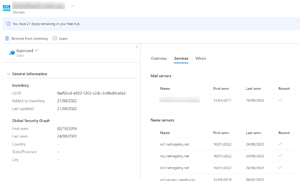 [Click on image for larger view.] External Attack Surface Management Domain Information
[Click on image for larger view.] External Attack Surface Management Domain Information
I particularly like the OWASP Top 10 inventory for web sites/applications. For those who aren't aware, this is a list (updated yearly) of the top types of vulnerabilities in web apps. Originally it was more tactical, and you could give it to a developer to work through and mitigate each one. Today it's a bit broader and more strategic, but it's still valuable to know, across your digital estate, what issues you have.
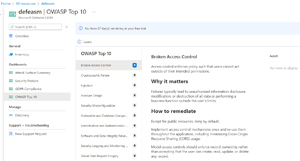 [Click on image for larger view.] External Attack Surface Management OWASP Top 10
[Click on image for larger view.] External Attack Surface Management OWASP Top 10
MDEASM also give you GDRP Compliance information and a Security Posture dashboard, along with an Attack Surface Summary dashboard.
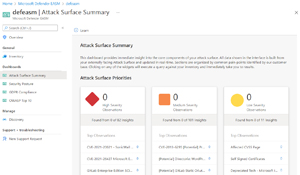 [Click on image for larger view.] External Attack Surface Management Attack Surface Summary
[Click on image for larger view.] External Attack Surface Management Attack Surface Summary
The Security Posture covers identified CVEs, domain names registrations across registrars, hosts, open ports, SSL certificates and how they're managed.
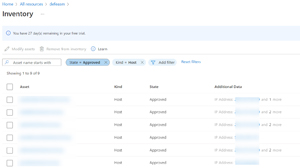 [Click on image for larger view.] External Attack Surface Management Host List
[Click on image for larger view.] External Attack Surface Management Host List
I think of MDEASM as an alternative to Shodan, with the capability of growing into something very useful, at least for large organizations. Pricing is based on assets (IP, Domains and Hosts) and is charged at 1.1 USD cent per day per asset. For a small business this probably won't be too expensive, but it's not hard to see how a large enterprise could end up with a "surprising" bill. It's a good idea to go through what it's found and exclude irrelevant assets to save some money.
Whether MDEASM is going to be useful to your business or not depends on how well you know your digital estate today. It's certainly worth trying it out for 30 days to see what it finds that you maybe weren't aware of. Note that discovery can take 2-3 days.
Conclusion
Microsoft is serious about security and this acquisition, and the resulting newborns makes perfect sense. I think these releases were a bit premature, though. The lack of integration into Sentinel and Defender 365 -- and the absence of APIs -- makes the "must have" case weaker. Once they are more integrated, I think the same reason that we no longer buy Microsoft Word and Excel separately will prevail. Yes, I'm so old that I remember a time before the Office Suite. The super strength of Defender 365 + Sentinel is the tight integration, giving you true eXtended Detection and Response (XDR) across email, identity, SaaS services and endpoints in one place -- MDTI and MDEASM aren't there yet, but when they get there, I can see many large businesses incorporating them in their overall security suite, as opposed to trying to integrate disparate third-party equivalents.