News
For Cloud Cybersecurity, You Can Pick 2 of 3: Easy, Cheap or Secure
IT pros responsible for enterprise cybersecurity shouldn't take the easy way out, like just clicking Next, Next ... Finish in a setup/configuration workflow process.
Instead, they need to take the extra, post-configuration steps to ensure a secure cloud environment, but while doing that, they might have to choose two of three security posture characteristics: easy, cheap or secure.
While that extra hardening may be more difficult, nobody ever said enterprise security was supposed to be easy.
In fact, someone told Dave Kawula the exact opposite.
"A good friend of mine told me this week -- and I absolutely love this statement -- he tells me, 'Dave, security was never meant to be convenient. It's not a matter of convenience.'
 "Security is supposed to be tough, because if it's not tough, it's going to be easy for the bad guys."
"Security is supposed to be tough, because if it's not tough, it's going to be easy for the bad guys."
Dave Kawula, managing principal consultant, TriCon Elite Consulting
"Security is supposed to be tough, because if it's not tough, it's going to be easy for the bad guys."
Kawula, managing principal consultant at TriCon Elite Consulting, was speaking to his presentation partner, John O'Neill Sr., chief technologist at AWS Solutions, in a recent, half-day, online summit hosted by Virtualization & Cloud Review.
Titled "Top Cloud Backup & Recovery Best Practices," the three-session summit held earlier this week is now available for free on-demand viewing.
O'Neill Sr. reinforced Kawula's assertion with an example that borrows from the old adage often associated with IT and software development stating that, for a new app or project, tech pros can choose two of three options presented in what has been called an iron triangle: good, fast or cheap. One has to settle for just two of those three characteristics, the adage states, because no project can come in with all three.
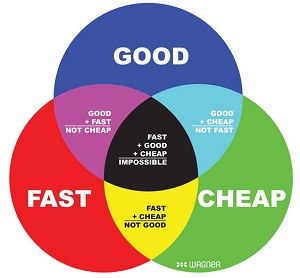 [Click on image for larger view.] Fast, Good or Cheap? You Can't Have All Three (source: Wagner Companies on Pinterest).
[Click on image for larger view.] Fast, Good or Cheap? You Can't Have All Three (source: Wagner Companies on Pinterest).
For his cybersecurity example, O'Neill Sr. used the terms cheap, secure and easy.
"When I talk to the C suite, the executives in an organization, and we talk about security, the way that I present it to them is I say, 'You have a triangle. And one point of that triangle is cheap, one point of that triangle is secure and one point of that triangle is easy.' And if you can think of a triangle in your mind, a line goes between two points. So you can pick two points. You can have cheap and easy, but it won't be secure. You can actually have easy and secure, but be ready to break out the pocketbook, because it costs a lot of money. And the easier you want it, the more you have to spend. And you can have secure and cheap, but it isn't going to be easy. It's going to be complicated."
For the online audience of hundreds, O'Neill Sr. fleshed out his example.
"So usually when we have that discussion, and then I tell people, I'm like, 'Well, you know what, instead of thinking about this as a line, let's pick a dot inside the triangle.' So we're going to come up with some balance of secure, cheap and easy. So it's not going to be as easy as your users want it. It's not going to be as cheap as the finance folks want it. But it should be close to as secure as you need it.
 "It probably won't be as secure as the security team wants it, because ultimately, if the system no longer services the organization and the customer, it doesn't really matter how secure we make it, we're out of business."
"It probably won't be as secure as the security team wants it, because ultimately, if the system no longer services the organization and the customer, it doesn't really matter how secure we make it, we're out of business."
John O'Neill Sr., chief technologist, AWS Solutions
"It probably won't be as secure as the security team wants it, because ultimately, if the system no longer services the organization and the customer, it doesn't really matter how secure we make it, we're out of business. And I often have that discussion, or debate if you will, with some security teams. Because it's like, 'Oh, we have to do this.' And I'm like, 'Well, okay, but then not just us, but everybody here is unemployed, because we lose our customer base.' At some point, you have to find a balance, and you can't do that in the vacuum of IT."
O'Neill Sr. also emphasized the need to harden things after Next, Next, Finish configuration processes.
 [Click on image for larger view.] Harden your Cloud Infrastructure
[Click on image for larger view.] Harden your Cloud Infrastructure
"The good news is, as Dave, you and I have relied on many times, is there are a number of very easy-to-deploy resources that are that are going to harden that cloud infrastructure. And one of our favorites is the second bullet point here. And that is the Center for Internet Security, or CIS hardened templates, where we can take these things that have been developed, tested, validated and are constantly being evolved. And with just a few clicks and without having to be Azure certified or anything else, we can deploy those and significantly improve the security, the posture of our operations.
"Now, of course, when we do these things, we have to engage with our customers, our operational folks. So whether it be the marketing group or the warehouse group, or whatever it may be, we need to tell them, 'Hey, we're going to make some changes. So if you notice something odd going on, please let us know' and that kind of thing. And, you know, they might not like the fact that, 'Hey, we're gonna take some downtime,' or whatever. But I guarantee you, though, by taking a few minutes of scheduled downtime to work with you is much better than hours or days of downtime because your cloud was compromised. Or even worse, an attacker compromised your cloud and then use that to backdoor themselves into your on-prem architecture."
Indeed, the CIS site offers "CIS Hardened Images" that are virtual machine (VM) images hardened in accordance with the CIS benchmarks, which is a set of vendor-agnostic, internationally recognized secure configuration guidelines. CIS Hardened Images provide users with a secure, on-demand, and scalable computing environment, and are available from major cloud computing platform marketplaces like AWS, Azure, Google Cloud Platform and Oracle Cloud.
In their two presentations in the three-part summit, our dynamic duo touched on many other aspects of cybersecurity, discussing their top 10 cloud infrastructure best practices for storage, backup & recovery in one session and, in the other, discussing "What You're Probably Doing Wrong (and Right) When it Comes To Cloud Backup & Recovery."
While the summit is now available for on-demand viewing, attending such presentations live brings benefits such as the opportunity to ask questions of our experienced, expert presenters (not to mention the chance to win cool prizes bestowed on attendees).
With that in mind, here are some related online summits coming up soon.
About the Author
David Ramel is an editor and writer at Converge 360.