News
Microsoft Wages Nation-State Cyberwar, Deleting 600 Domains
Microsoft has been busy removing internet domains identified as being criminally used by bad actors, including those sponsored by nations.
That's one takeaway from the company's sprawling Microsoft Digital Defense Report 2022, which devotes one of its sections to nation-state threats that reached a new level with the advent of the war in Ukraine.
"On February 23, 2022, the cybersecurity world entered a new age, the age of the hybrid war, as Russia launched both physical and digital attacks against Ukraine," the company said in a blog post about the report that was published earlier this month. "This year's Microsoft Digital Defense Report provides new detail on these attacks and on increasing cyber aggression coming from authoritarian leaders around the world.
"During the past year, cyberattacks targeting critical infrastructure jumped from comprising 20 percent of all nation-state attacks Microsoft detected to 40 percent. This spike was due, in large part, to Russia's goal of damaging Ukrainian infrastructure, and aggressive espionage targeting of Ukraine's allies, including the United States. Russia also accelerated its attempts to compromise IT firms as a way to disrupt or gain intelligence from those firms' government agency customers in NATO member countries. 90 percent of Russian attacks we detected over the past year targeted NATO member states, and 48 percent of these attacks targeted IT firms based in NATO countries."
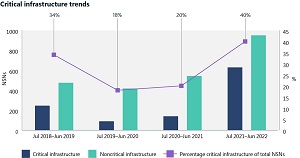 [Click on image for larger view.] Critical Infrastructure Trends (source: Microsoft).
[Click on image for larger view.] Critical Infrastructure Trends (source: Microsoft).
As part of its wide-ranging efforts in "dismantling cybercrime," Microsoft removes domains under its control (sometimes seeking temporary custody) that are identified with attacks, including those used by state-sponsored groups.
"To date, Microsoft removed more than 10,000 domains used by cybercriminals and 600 used by nation state actors," the report said.
For one example, Microsoft deleted U.S. domains associated with the China-backed group called NICKEL. Here's the synopsis:
In December 2021, the Microsoft Digital Crimes Unit (DCU) filed pleadings with the US District Court for the Eastern District of Virginia seeking authority to seize 42 command and control (C2) domains controlled by NICKEL. These C2 domains were used in operations against governments, diplomatic entities, and NGOs across Central and South America, the Caribbean, Europe, and North America since September 2019.24 Through these operations, NICKEL achieved long-term access to several entities and consistently exfiltrated data from some victims since late 2019. As China continues to establish bilateral economic relations with more countries -- often in agreements associated with BRI -- China's global influence will continue to grow. We assess Chinese state and state-affiliated threat actors will pursue targets in their government, diplomatic, and NGO sectors to gain new insights, likely in pursuit of economic espionage or traditional intelligence collection objectives. Since Microsoft's disruption, NICKEL has targeted several government agencies, likely trying to regain lost access. Between late March and May 2022, NICKEL re-compromised at least five government agencies across the globe. This suggests the group had additional entry points to those entities or regained access through new C2 domains. NICKEL's persistence in repeatedly compromising the same government agencies globally indicates the importance of the task at a high level.
The company also dealt with the Waledac botnet:
- Description: A complex spam botnet with US domains that collected email addresses and distributed spam that infected up to 90,000 computers across the world.
- Collaboration: Creation of another consortium, the Microsoft Malware Protection Center (MMPC) with a focus on close collaboration with academics.
- Microsoft response: Microsoft used tiered disruption approach of C2 [command and control] and surprised bad actors by seizing US-based domains without notice. Microsoft granted temporary ownership of nearly 280 domains used by Waledac's servers.
Along with the increased nation-state actor threat, the huge report delves into areas including: the state of cybercrime; devices and infrastructure; cyber influence operations; and cyber resilience.
Here are summaries and some salient data points for those other four areas:
-
The state of cybercrime: Cybercriminals continue to act as sophisticated profit enterprises. Attackers are adapting and finding new ways to implement their techniques, increasing the complexity of how and where they host campaign operation infrastructure. At the same time, cybercriminals are becoming more frugal. To lower their overhead and boost the appearance of legitimacy, attackers are compromising business networks and devices to host phishing campaigns, malware, or even use their computing power to mine cryptocurrency.
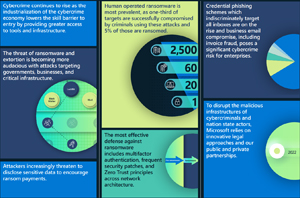 [Click on image for larger view.] The State of Cybercrime (source: Microsoft).
[Click on image for larger view.] The State of Cybercrime (source: Microsoft).
-
Devices and infrastructure: The pandemic, coupled with rapid adoption of internet-facing devices of all kinds as a component of accelerating digital transformation, has greatly increased the attack surface of our digital world. As a result, cybercriminals and nation states are quickly taking advantage. While the security of IT hardware and software has strengthened in recent years, the security of IoT and OT devices security has not kept pace. Threat actors are exploiting these devices to establish access on networks and enable lateral movement, to establish a foothold in a supply chain, or to disrupt the target organization's OT operations.
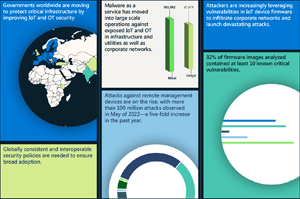 [Click on image for larger view.] Devices & Infrastructure (source: Microsoft).
[Click on image for larger view.] Devices & Infrastructure (source: Microsoft).
-
Cyber influence operations: Nation states are increasingly using sophisticated influence operations to distribute propaganda and impact public opinion both domestically and internationally. These campaigns erode trust, increase polarization, and threaten democratic processes. Skilled Advanced Persistent Manipulator actors are using traditional media together with internet and social media to vastly increase the scope, scale, and efficiency of their campaigns, and the outsized impact they are having in the global information ecosystem. In the past year, we have seen these operations used as part of Russia's hybrid war in Ukraine, but have also seen Russia and other nations, including China and Iran, increasingly deploy propaganda operations powered by social media to extend their global influence on a range of issues.
 [Click on image for larger view.] Cyber Influence (source: Microsoft).
[Click on image for larger view.] Cyber Influence (source: Microsoft).
-
Cyber resilience: Security is a key enabler of technological success. Innovation and enhanced productivity can only be achieved by introducing security measures that make organizations as resilient as possible against modern attacks. The pandemic has challenged us at Microsoft to pivot our security practices and technologies to protect our employees wherever they work. This past year, threat actors continued to take advantage of vulnerabilities exposed during the pandemic and the shift to a hybrid work environment. Since then, our principal challenge has been managing the prevalence and complexity of various attack methods and increased nation state activity. In this chapter, we detail the challenges we have faced, and the defenses we have mobilized in response with our more than 15,000 partners.
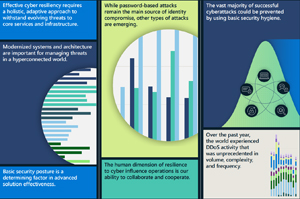 [Click on image for larger view.] Cyber Resilience (source: Microsoft).
[Click on image for larger view.] Cyber Resilience (source: Microsoft).
Along with the more than 10,000 domains that have been removed, Microsoft said it uses sophisticated data analytics and AI algorithms to better understand and protect against digital threats and cybercriminal activity, synthesizing some 43 trillion signals each day. What's more, it blocked more than 70 billion email and identity threat attacks just last year. Overall, the company fields more than 8,500 security and threat intelligence experts around the world, spreading engineers, researchers, data scientists, threat hunters, geopolitical analysts, investigators, frontline responders and cybersecurity experts across 77 countries.
So why does it do all that?
Microsoft security exec Tom Burt summed it up: "I believe Microsoft has a responsibility to protect the digital systems that underpin the social fabric of our society."
About the Author
David Ramel is an editor and writer at Converge 360.