News
Ransomware Hits Unpatched VMware Systems: 'Send Money Within 3 Days'
Users who neglected to install security patches issued by VMware two years ago are now being hit by a big ransomware attack wave.
Today, (Feb. 6), VMware posted "VMware Security Response Center (vSRC) response to 'ESXiArgs 'ransomware attacks":
We wanted to address the recently reported 'ESXiArgs 'ransomware attacks as well as provide some guidance on actions concerned customers should take to protect themselves.
First, it should be noted that VMware has not found any evidence that would suggest an unknown vulnerability (0day) is being used to propagate the ransomware used in these recent attacks. Most reports state that End of General Support (EOGS) and/or significantly out of date products are being targeted with known vulnerabilities which were addressed and disclosed in VMware Security Advisories (VMSAs). You can sign up for email and RSS alerts when an advisory is published or significantly modified on our main VMSA page.
With this in mind, we are advising customers to upgrade to the latest available supported releases of vSphere components to address currently known vulnerabilities. In addition, VMware has recommended disabling the OpenSLP service in ESXi since 2021 when ESXi 7.0 U2c and ESXi 8.0GA began shipping with the service disabled by default.
Organizations in Europe are reportedly being hit hard.
A Feb. 4
alert from the National Cybersecurity Agency (CSIRT) in Italy said (translated from Italian) "
CVE-2021-21974 was recently detected to be massively exploited for ransomware release purposes."
It said affected systems included:
- VMware ESXi 6.5
- VMware ESXi 6.7
- VMware ESXi 7.0
- VMware Cloud Foundation (ESXi) 3.x
- VMware Cloud Foundation (ESXi) 4.x
The French computer emergency response team (CERT-FR) also issued an alert on Feb. 3, recommending (translated from French):
- Isolate the affected server.
- if possible, perform a system scan for signs of compromise [2], applying patches alone is not enough, an attacker has probably already dropped malicious code;
- Prefer to reinstall the hypervisor in a version supported by the publisher (ESXi 7.x or ESXi 8.x);
- Apply all security patches and follow future security advisories from the publisher.
- Disable unnecessary services on the hypervisor (such as the SLP service [3]);
- block access to the various administration services, either through a dedicated firewall or through the firewall integrated into the hypervisor and implement a local administration network and remote administration capability if required (via virtual private network, VPN, or, failing that, by filtering trusted IP addresses).
VMware addressed the vulnerability on Feb. 23, 2021, saying "Multiple vulnerabilities in VMware ESXi and vSphere Client (HTML5) were privately reported to VMware. Updates are available to remediate these vulnerabilities in affected VMware products."
A Feb. 3 tweet from DarkFeed includes a copy of the ransom note.
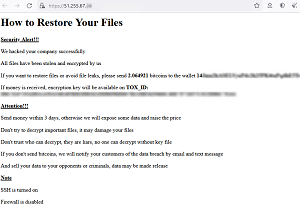 [Click on image for larger view.] Ransom Note (source: DarkFeed/Twitter).
[Click on image for larger view.] Ransom Note (source: DarkFeed/Twitter).
"What's interesting is that the bitcoin wallet is different in every ransom note," the tweet said. "No website for the group, only TOX id"
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) apparently hasn't issued any news alerts or blog posts, but TechCrunch today reported a spokesperson said: "CISA is working with our public and private sector partners to assess the impacts of these reported incidents and providing assistance where needed. Any organization experiencing a cybersecurity incident should immediately report it to CISA or the FBI."
About the Author
David Ramel is an editor and writer at Converge 360.