In-Depth
Microsoft Entra Internet and Private Access
Paul's review: Entra Internet Access makes a lot of sense, while Entra Private Access is an interesting evolution of the existing App Proxy and could be a no-brainer for SMBs with on-premises resources.
In last month's article I looked at Entra, Azure Active Directory and how strong identity and security are related. And then Microsoft renamed Azure AD to Entra ID. Everything in that article is still accurate, just the name has changed.
In this article I'll look at two recent public previews in the Entra family, Microsoft Entra Internet Access and Microsoft Entra Private Access, collectively called Global Secure Access. These were revealed at a recent Tech Accelerator event.
I'll also touch on the Azure AD rename, and why I think it's actually a good move, albeit 10 years late.
Alphabet Soup
Back in 2019, Gartner coined the term Secure Access Service Edge (SASE), often contrasted with Zero Trust (coined in 1994 by Stephen Paul Marsh, but made popular by Forrester). SASE refers to an enterprise network architecture where security and networking functions are moved to the cloud. A complete SASE solution combines a Cloud Access Security Broker (CASB), Zero Trust Network Access (ZTNA), Firewall as a Service (FWaaS), Secure Web Gateway (SWG) with a Software Defined Wide Area Network (SD-WAN). Examples of vendors in this space are Netskope, Zscaler, Barracuda Networks, Fortinet, Palo Alto Networks and Cisco, but as most of them don't offer everything on the SASE menu, Gartner defined a subset of SASE in Secure Service Edge (SSE) in 2021. This focuses on only the security portions, and skips SD-WAN, QoS and WAN optimization.
These two new Entra services are SSE, not SASE solutions.
One more acronym deserves mention: Continuous Access Evaluation (CAE). Traditionally, in any OAuth system, once a client authenticates and receives a refresh token, it's generally valid for an extended period of time (1 hour). This means that if you need to cut off access for a user quickly (their account is compromised, or they've been fired and escorted out of the building), they might still have access to email, SharePoint sites and so on for up to one hour. CAE changes this by having the client aware of the need for an extra check, so today for Microsoft client apps, account disablement takes effect within a few minutes.
Entra Internet Access
There's no doubt that the last few years, both with the pandemic with its resulting lockdowns and changes in work from home approaches plus the intensity and scale of cyberattacks, corporate networks have changed forever. Forcing remote workers to use clunky VPN solutions to tunnel all traffic back through corporate headquarters firewalls just doesn't scale or provide an acceptable user experience.
The alternative -- a free-for-all connectivity approach to SaaS services -- is far too risky, which is where a good CASB comes into the picture, but this doesn't cover on-premises applications.
Entra Internet Access is an identity-centric Secure Web Gateway (SWG), providing dedicated tunnels for traffic you designate directly via Microsoft's global network. Currently Microsoft 365 traffic is supported, but eventually all internet and SaaS apps will be covered. It's worth pointing out that in both these public preview services there are many puzzle pieces still "coming soon."
You'll need an agent on the endpoint; 64-bit Windows 10 / 11 is supported with a download today, and it will eventually be integrated into Windows 11 as part of the OS. That client will also be integrated with Defender for Endpoint and Endpoint Manager. Agents for MacOS, Android and iOS are coming. This is a single agent for both Entra Internet Access and Private Access. For branch offices and for scenarios where you can't install an agent, branch offices will be able to establish an IPsec VPN tunnel from their firewall / router -- this is currently in private preview.
If you already have a third-party SSE solution deployed, you can easily split Microsoft 365 traffic into Entra Internet Access and let the current solution take care of everything else. I particularly like that the configuration of traffic profiles is done through Conditional Access (CA) policies, and in fact network traffic is a new resource type that you can use in CA. You can designate networks as compliant in the same place where you manage named locations for CA policies today. Here's the creation of a new CA policy, picking the Microsoft 365 traffic profile (nternet traffic is in private preview and I haven't configured any Private access resources):
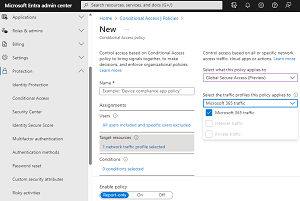 [Click on image for larger view.] Creating a Conditional Access Policy with Global Secure Access
[Click on image for larger view.] Creating a Conditional Access Policy with Global Secure Access
It's worth noting that while no pricing has been announced, it has been mentioned that using Entra Internet access for M365 traffic will be included in M365 E3/E5 licensing.
You can create your own traffic policies, based on port, protocol, IP address or FQDN, while user and group device targeting is coming. Another powerful capability is integration with any Entra ID cloud apps already in your Azure AD Entra ID. As can be expected of any SWG web category (social networking, violence, hate and so on) filtering is coming (private preview at the moment). In the "coming soon" bucket is full 5-tuple support, TLS termination and inspection and Threat detection and Intrusion Detection and Prevention. As mentioned above, CAE requires support in the client app, but also coming soon is "Universal Continuous Access Evaluation" for any destination through the SWG. This also extends CA to be able to cover any destination/app, a much-requested feature.
Another cool feature is the restoration of original source IP for CA policies, risk detection scenarios and activity logs. Most other proxies / SWGs will translate the client's IP address into its own, making creating flexible CA policies difficult. Entra Internet Access also provides data exfiltration control so you can control external identities usage in your tenant, with granular control over accounts and applications.
There are some nice dashboards for monitoring, one showing user, device and endpoint relationships, another one for cross-tenant user activity, and one with top destinations by user, sessions and devices. The logged data can be exported to Log Analytics and further visualized in Azure Workbooks or accessed through an API. There are also rudimentary connections to Microsoft Sentinel and third-party SIEMS, with more robust ones to come.
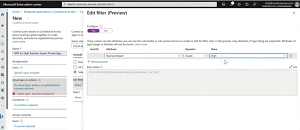
 [Click on image for larger view.] Entra Internet Access Traffic Logs Filtering Options
[Click on image for larger view.] Entra Internet Access Traffic Logs Filtering Options
For threat detection the metadata gleaned (without breaking TLS and deep packet inspection) includes device context (OS, version, device ID/name, process name, logged on user/SID), network context (tunnel, tenant info, ports/protocol, geo location) plus user and token context, which should make spotting bad activity easier. This is part of the enriched M365 logs, which currently only supports SharePoint activity, with Teams and Exchange Online coming soon.
Another strength underlined by Microsoft is that the infrastructure is co-located with Microsoft 365's native front doors, something no other SWG can match (obviously). The current public preview is available in North America and Europe with more regions to follow.
Entra Private Access
The challenges of large-scale VPN deployments to manage access to on-premises business resources were covered above, although one huge issue wasn't highlighted: If you connect clients with traditional VPN tunnels, they become full-fledged clients on the corporate network. It just takes one compromised client to spread an infection internally.
Microsoft does have a solution today, called Azure AD Entra Application Proxy. This deploys lightweight agents on internal servers that establish outbound connectivity and allow seamless publishing of web applications only, to external users, without having to expose those applications to the internet.
But there are many other resource types that you'd like users on the road to access, such as RDP servers, SSH for management, FTP for file transfer, printers and of course the "original sin," SMB file shares.
This is where Entra Private Access comes in. Building on the strengths of App Proxy, it allows you to publish all types of resources for external access securely, again without having to open inbound ports on your corporate firewall. And unlike a traditional VPN, the client doesn't get full network access, just access to the application(s). Single sign on is possible using Kerberos, SAML or http headers. And you can target app access based on user and device identity. Coming soon (and shown in a cool demo) is the ability to target a specific process ID. Finding what applications you have that could be published is also included in the form of app discovery and onboarding.
Coming soon here is TLS termination and inspection, web application firewall (a similar service to what you have in Azure, protecting web apps against common attack types), and intelligent local access. This last one is interesting. If you're on the corporate network, accessing a published application, it'll allow the network traffic to go directly between your device and the app, whilst still applying CA policies to the connection.
Getting started with Entra Private Access is easy with QuickAccess that publishes apps already in Entra. You can then use app discovery to create more granular policies for different apps. You can, for example, tag applications as low, medium and high business impact, and for any apps tagged high, you can use the new authentication strength construct to only allow phishing-resistant authentication for them.
 [Click on image for larger view.] Creating a Conditional Access Policy to Enforce Strong Authentication for a High Business Impact Application
[Click on image for larger view.] Creating a Conditional Access Policy to Enforce Strong Authentication for a High Business Impact Application
It's worth contrasting Private Access with Microsoft's current VPN offering, Always On. This is a more traditional VPN setup, requiring more infrastructure and configuration, whereas Private Access is easier to set up (just deploy the agents, as everything else is configured from the cloud).
What's in a Name?
So, Azure AD is no more -- replaced by Entra ID. Many a keyboard has been worn out by typing out opinions for or against this change so I'll keep this brief.
Azure AD didn't exist as a resource in Azure. In fact, its only relationship to Azure was that you can associate a default subscription with an Azure AD tenant. It also has nothing to do with Active Directory (as I've had to explain in many a course I've delivered over the last 10 years). Also, it doesn't have a hierarchical structure, doesn't support Kerberos (until recently, and then only for limited scenarios) and so forth. Apart from both authenticating identities and storing accounts, they are two totally different technologies.
I like the new name, but I just wish the rename had been done 10 years ago and we could have avoided the confusion in the meantime.
Wrapping Up
As seems to be the new norm for Microsoft (looking at you -- Security Copilot), there are lots of pieces of Entra Global Secure Access in private preview or coming soon, so it's a bit hard to form a solid opinion going by the bits that have been released so far.
Entra Internet Access makes a lot of sense to me -- Microsoft has a fantastic global network, and bringing more of the traffic of the world's most popular productivity suite "in house" will provide better security and better performance (generally those are traded off against each other). What I'm still waiting to see is how Defender for Cloud Apps, Microsoft's popular CASB, fits into the picture. Arguably it does some of what Internet Access sets out to do.
Entra Private Access is an interesting evolution of the existing App Proxy. Large enterprises will already have systems for this in place, and it'll take some maturing and demonstration in the market for this to be a valid alternative. For SMBs with some on-premises resources, this could be a no-brainer, depending of course on cost and ease of setup.