News
Help Stop Breaches and Bill Shock with These 2 Cloud Fixes
Cloud costs creeping higher than expected? Security risks keeping you up at night? You're not alone -- and you're not without options. In a recent cloud strategy summit, cloud security expert Steven Smiley offered practical guidance to help organizations get ahead of both challenges and bring discipline to their cloud environments.
Smiley is a consulting director at ScaleSec, where he leads the firm's cloud security advisory and engineering efforts. He's also a certified cloud security professional and AWS ambassador, working with organizations of all sizes to build secure, scalable cloud environments and align technical solutions with business objectives.
Smiley's presentation, titled "Expert-Level Cloud Tactics To Manage Bloat and Fight Breaches," kicked off the Cloud Management Strategy Summit, a virtual two-session event sponsored by Rubrik and hosted by Virtualization & Cloud Review, now available for on-demand viewing. Over the course of nearly an hour, he walked attendees through practical strategies for regaining control over sprawling cloud environments. His talk covered everything from credential management and cost containment to network topology planning, backup hardening, and zero-trust access -- all with an eye toward reducing risk and eliminating waste.
 "Some organizations will just allow people to expense costs as if they were any other cost in the organization, and kind of allow people to run these themselves. It's a really bad idea."
"Some organizations will just allow people to expense costs as if they were any other cost in the organization, and kind of allow people to run these themselves. It's a really bad idea."
Steven Smiley, Consulting Director, ScaleSec
While Smiley covered a wide range of advanced cloud tactics, the session packed in too much detail to fully cover here. Instead, what follows are two standout takeaways that offer immediate, high-impact value. For those interested in the full presentation, an on-demand replay is available through the event site.
Protect Access by Eliminating Long-Lived Credentials
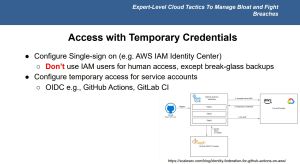
One of Smiley's key recommendations for reducing cloud breach risk is to eliminate long-standing credentials. Instead, organizations should adopt temporary access methods for both users and services. This not only reduces the attack surface but also limits the damage if credentials are exposed. As he explained during the session, "One of the most common ways that we're seeing organizations get compromised in the cloud, is that their credentials get leaked."
 [Click on image for larger view.](source: Steven Smiley/AWS).
[Click on image for larger view.](source: Steven Smiley/AWS).
He emphasized that these incidents aren't always the result of sophisticated exploits. "You've just accidentally committed access credentials to a GitHub repository, or it's on a user's laptop, and that laptop gets compromised, something like that." These simple mistakes can have outsized consequences if the credentials involved are permanent or overly permissive.
Smiley recommended replacing permanent credentials with two more secure approaches:
- Use single sign-on (SSO) for human users: Instead of issuing individual IAM credentials, organizations should integrate their cloud accounts with an identity provider. "Instead having users use single sign on through something like AWS identity center, and just getting rid of Iam users for humans that will make it so that these credentials are not long lived." This minimizes credential sprawl and ensures that access is limited to a defined session window.
- Configure temporary access for service accounts: Many automation platforms now support identity federation via standards like OpenID Connect (OIDC), which eliminates the need to store long-term secrets in pipeline code. "We're using protocols like OIDC to allow GitHub actions to deploy into my account, but GitHub actions does not have a set of permanent credentials."
He added that these temporary credentials often expire in just a few hours -- dramatically reducing their value if leaked. "They will expire within something like one to eight hours, depending on your configuration, and so these temporary credentials will not nearly be as valuable."
Smiley also pointed attendees to a how-to blog (linked in the slide) for configuring GitHub Actions with OIDC, noting that while his examples stem from AWS, these patterns are broadly supported across major cloud platforms.
Use Budget Alerts to Catch Cost Spikes -- and Potential Breaches
Smiley also highlighted budget alerts as a deceptively simple but powerful tactic for managing both cloud spending and security. Setting cost thresholds -- at both the organizational and individual account level -- not only helps avoid surprise bills, it can also serve as an early warning system for suspicious activity.
 [Click on image for larger view.](source: Steven Smiley/AWS).
[Click on image for larger view.](source: Steven Smiley/AWS).
"Don't ignore your cloud costs," Smiley advised. "Think about what these are. Set some budgets at different levels." He recommended defining limits for both high-value production accounts and lower-priority environments, like development sandboxes. For example, a dev account might be capped at a few hundred dollars per month to ensure experiments don't spiral into financial surprises.
"Inside my development account, where I'm just letting some developers learn and do some sandbox work, let's make sure that doesn't go over some defined amount. Maybe that's 200 bucks a month," he suggested. "If they go over that for a good reason, that's fine, but let's make sure that we don't get a surprise bill for $5,000 at the end of the month."
Much More
Of course, one of the best things about attending online education summits like this is the opportunity to ask questions directly to seasoned experts -- an increasingly rare chance to get real-world, one-on-one guidance tailored to your organization's unique challenges. And, of course, there's a fun incentive for sticking around, including prize giveaways. Today, for example, the first 300 attendees were awarded Starbucks gift cards courtesy of Rubrik, which also presented at the summit.
Of course, one of the best things about attending such online education summits and events is the ability to ask questions directly to the presenters -- a rare opportunity for expert, real-world, one-on-one advice (not to mention the chance to win a great prize).
With that in mind, here are some events from our parent company coming up in the remainder of May:
About the Author
David Ramel is an editor and writer at Converge 360.