News
Cloud Architect Details How to Build a Database Security Playbook
Cloud architect Joey D’Antoni breaks down a six-part framework for building a resilient database security playbook across AWS and Azure. From access reviews to incident drills, here’s how to lock down your most critical cloud assets.
In today's hybrid and multi-cloud environments, databases remain among the most targeted and vulnerable assets. In today's Virtualization & Cloud Review summit on cloud database security, principal architect Joey D'Antoni shared a detailed framework for organizations looking to strengthen their defenses.
Today's multi-part event, From Azure to AWS, Closing the Security Gaps in Your Cloud Database Summit, is available for on-demand replay.
 "It's not just the CISO who makes an organization secure. It's going to be an organizational mantra to improve the security in the organization, understand where those gaps are and continue."
"It's not just the CISO who makes an organization secure. It's going to be an organizational mantra to improve the security in the organization, understand where those gaps are and continue."
Joey D'Antoni, Principal Cloud Architect at 3Cloud
D'Antoni's session emphasized a structured approach to building a cloud database security playbook -- one that balances policy, tooling, architecture, and collaboration.
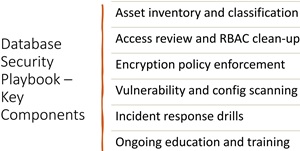 [Click on image for larger view.] Playbook Components (source: Joey D'Antoni).
[Click on image for larger view.] Playbook Components (source: Joey D'Antoni).
Here are the six key components D'Antoni recommends for any organization serious about protecting its cloud databases:
1. Asset Inventory and Data Classification
Security begins with visibility. Organizations need a clear picture of where their databases live, what kinds of data they hold, and which systems interact with them. "If you don't know what data you have, you don't know how to protect it," D'Antoni said. Identifying data types -- especially personally identifiable information (PII) -- is critical to applying the right protections and policies.
2. Access Review and RBAC Clean-up
Over-permissioned identities are one of the most common database vulnerabilities. D'Antoni emphasized the importance of auditing access regularly and aligning it with least-privilege principles. "Ideally, you want your access built into the source control for your application," he noted, referring to the practice of managing roles and permissions through infrastructure-as-code models.
3. Encryption Policy Enforcement
Encrypting sensitive data -- both at rest and in transit -- must be standard practice. D'Antoni advised organizations to take full advantage of cloud-native encryption tools, such as AWS Key Management Service and Azure Key Vault, and to understand how bring-your-own-key (BYOK) models affect compliance requirements. Knowing where PII resides makes it easier to apply consistent encryption policies.
4. Vulnerability and Configuration Scanning
Misconfigurations remain a top cause of cloud database breaches. D'Antoni recommended automated scanning and policy-based enforcement to flag risky conditions, such as open ports, excessive permissions, or disabled logging. Tools mentioned included Azure Defender, AWS Config rules, and policy-as-code frameworks that integrate into CI/CD pipelines.
5. Incident Response Drills
D'Antoni stressed the importance of operational readiness. "You want to be prepared and understand what your threat vectors are like," he said. He encouraged teams to regularly simulate security incidents and validate their response plans. Testing real-world scenarios -- such as credential compromise or SQL injection -- helps ensure gaps are identified before attackers exploit them.
6. Ongoing Education and Training
Security is a team-wide responsibility. Developers, database administrators, and security personnel must stay aligned and informed as threats evolve. D'Antoni noted that while some attack types (like SQL injection) haven't changed much in 20 years, education and secure coding practices are still essential defenses. "It's not just the CISO who makes an organization secure," he said. "It's going to be an organizational mantra."
Why This Framework Matters
- It is comprehensive: covering everything from asset visibility to team training.
- It is practical: with specific tools and processes for detection and enforcement.
- It is adaptable: designed to apply across both AWS and Azure environments.
This framework gives IT and security professionals a structured, repeatable way to assess and improve their cloud database security posture -- without depending on any one vendor or product.
And More
Replays are fine -- this one is available on-demand so readers can flesh out those playbook plans in more detail -- but there's real value in attending live, like the opportunity to ask presenters questions and get one-on-one expert feedback. And that's not to mention a chance at a sponsor giveaway like $5 Starbucks cards awarded to attendees today, in this case from Rubrik, a leading data security specialist, which also presented at the summit and provided free resources to attendees.
With that in mind, here are upcoming events from our parent company over the next month:
About the Author
David Ramel is an editor and writer at Converge 360.