In-Depth
5 Smart Database Security Moves You Can Make with AI Analytics Right Now
Data breaches are becoming more sophisticated, more frequent and far more costly. But what if your organization already has the data it needs to detect them -- if only you knew how to analyze it? That was one of the key messages from data security expert Karen Lopez during her recent presentation, part of the "Next-Gen Database Security Strategies for the Intelligence Era" summit hosted by Virtualization & Cloud Review and sponsored by Rubrik. It's available for on-demand viewing.
 "We all know what ROI stands for, but with current legislation, there are more and more criminal penalties for data breaches and threats, and therefore ROI also stands for risk of incarceration, so tell your boss that."
"We all know what ROI stands for, but with current legislation, there are more and more criminal penalties for data breaches and threats, and therefore ROI also stands for risk of incarceration, so tell your boss that."
Karen Lopez, @datachick.bsky.social
The July 29 session, titled "When, Why and How To Use Analytics to Mitigate Database Threats," featured Lopez -- a Microsoft MVP and longtime data architecture consultant -- taking attendees through a whirlwind tour of how modern analytics tools can be used not just for compliance and alerting, but for proactive threat detection. Along the way, she blended real-world experience with practical advice and even a few data-driven zingers (she reminded viewers that in an era of rising legal penalties, "ROI" might also mean "Risk of Incarceration").
While Lopez covered a wide range of topics -- from AI copilots to the dangers of permissions drift -- she kept returning to one core idea: analytics isn't just about dashboards. It's a way of surfacing the things that traditional monitoring often misses. "Monitoring is more about real-time observations," she explained. "Analytics is...about historical and predictive" views that help uncover risk factors before they lead to a breach.
Here are five of the most practical action items from Lopez's session -- each one showing how security-minded IT professionals can put analytics to work in their own environments, right now.
Throughout the session, Lopez presented many of her analytics scenarios as natural-language question -- "AI agent questions," as labeled on several slides. These prompts reflect how many modern security tools, such as Microsoft Copilot or Sentinel integrations, now allow IT teams to interact directly with their data using conversational input rather than writing custom scripts. "We're asking the AI to go look at things," Lopez said, offering examples of how these tools help surface anomalies that humans might otherwise overlook.
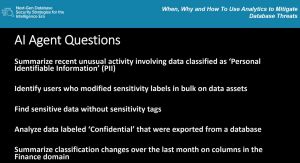
Analyze Unusual Activity Involving Data Classified as PII
 [Click on image for larger view.]
[Click on image for larger view.]
One of the most immediately actionable ways to bring analytics to bear on database security is to focus on activity involving personally identifiable information (PII). As Karen Lopez put it, classifying data is what "enables everything else we're going to talk about," and nowhere is that more evident than when trying to detect anomalous interactions with sensitive personal data.
"Maybe someone's allowed to see sensitive data," she said, "but maybe you want to know about a user that has modified a bunch of data assets that would be in some cases abnormal, and we'd want to know about it." That kind of analysis moves beyond traditional monitoring, which Lopez described as being reactive and limited to “point in time" events.
Lopez emphasized that tools like Microsoft Purview can automate much of the classification work and make sensitivity labeling actionable. But she was also clear that automation alone isn't enough: "We want also that these labels, these tags we put on them, to be usable throughout the life cycle of the data, so it's not just a report... it's so that tools and systems can actually stop some people from doing either stupid things or bad things with it."
Ultimately, by labeling PII effectively and then analyzing behavior around it, organizations can move from reactive alerts to proactive threat hunting. And that, according to Lopez, is a major step toward making data protection work in an era of increasingly professionalized threats.
Identify Databases Where Encryption Has Changed or Been Disabled After Initial Deployment
 [Click on image for larger view.]
[Click on image for larger view.]
One of the clearest signals of rising database risk is a change in encryption settings -- especially when protections are downgraded or turned off. Lopez flagged this scenario as a high-priority use case for analytics tools, noting it as a question you can put directly to an AI agent: "Identify databases where encryption was changed or disabled after initial deployment."
She warned that such changes often occur outside of standard governance channels, introducing silent vulnerabilities. "Maybe it's been changed in a weaker way instead of a stronger way," she said, adding that tracking configuration drift over time is essential to prioritizing remediation and uncovering risky behaviors that otherwise go unnoticed.
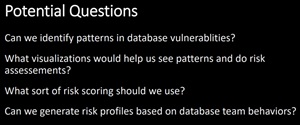
Detect Patterns in Database Vulnerabilities Across the Organization
 [Click on image for larger view.]
[Click on image for larger view.]
Instead of chasing isolated security issues, Lopez urged organizations to look for patterns. Are the same misconfigurations recurring across teams? Are certain departments consistently deploying risky settings? "Can we identify patterns in database vulnerabilities?" she asked. "Can we generate risk profiles based on team behaviors?"
She emphasized that identifying repeat offenders -- whether human or system-level -- is where analytics excels. Trend spotting over time can expose systemic weaknesses that monitoring tools alone won't catch.
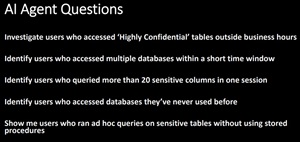
Investigate Users Who Access Highly Confidential Information Tables Outside of Business Hours
 [Click on image for larger view.]
[Click on image for larger view.]
Time-based anomalies are often overlooked, but Lopez said they can be red flags for credential abuse or insider threats. One scenario she highlighted: "Investigate users who accessed 'Highly Confidential' tables outside business hours."
While she acknowledged that business hours are a fluid concept, especially in global environments, she emphasized the value of behavioral baselines. When someone suddenly deviates -- querying sensitive data at odd hours -- it may warrant closer scrutiny.
Identify Any New Service Accounts Created with Access to Sensitive Databases
 [Click on image for larger view.]
[Click on image for larger view.]
Service accounts with broad access can be a quiet entry point for attackers -- or for well-meaning automation gone wrong. That's why Lopez recommended asking analytics tools to flag unexpected additions: "Show me any new service accounts created with access to sensitive databases."
Correlating these account changes with recent privilege escalations or password resets can help uncover threats in the making, before they escalate into breaches.
And More
Lopez had a lot more expert advice to share on those five action items and a lot more about other topics in her complete presentation, and an on-demand replay is definitely in order. And, although replays are fine -- this was just today, after all, so timeliness isn't an issue -- there are benefits of attending such summits and webcasts from Virtualization & Cloud Review and sister sites in person. Paramount among these is the ability to ask questions of the presenters, a rare chance to get one-on-one advice from bona fide subject matter experts (not to mention the chance to win free prizes -- in this case $5 Starbucks gift cards which were awarded to the first 300 attendees during a session by sponsor Rubrik, a leader in cloud data management and enterprise data protection which also presented at the summit).
With all that in mind, here are some upcoming webcasts coming up from our parent company in the next month or so:
About the Author
David Ramel is an editor and writer at Converge 360.