In-Depth
AWS S3 Security: Three Action Items to Lock Down Your Buckets
At a AWS S3 security webcast today held by Virtualization & Cloud Review, cloud instructor Carlos Rivas outlined the core practices IT teams must follow to keep S3 data safe, from monitoring configurations to enforcing encryption. As part of his presentation, he provided a handy list of three action items that organizations can tackle right now for cloud security.
The Event
The webcast, titled "AWS S3 Security Essentials: Safeguarding Data in the World's Biggest Cloud," took place on Aug. 20 and was sponsored by Druva, who also presented at the event and has made the whole thing available for on-demand replay.
 "Misconfigured information is going to be the number one [vulnerability], and you're going to find out there is something that is public that shouldn't have been public. And you usually find out when it's already too late."
"Misconfigured information is going to be the number one [vulnerability], and you're going to find out there is something that is public that shouldn't have been public. And you usually find out when it's already too late."
Carlos Rivas, Sr. Solutions Architect
Rivas, a senior solutions architect and AWS instructor whose work appears on LinkedIn Learning, Cloud Academy, and Udacity, delivered the opening session. He brought years of consulting experience, including migrating California community colleges to the cloud, to bear on one of AWS' most widely used but often misconfigured services: Amazon S3.
The Three Action Items
Rivas presented a slide that distilled his guidance into three key practices:
- Evaluate configuration, security and monitoring constantly
- Set up automation such as Config Rules to monitor your buckets
- Above all, protect your data with encryption and access controls
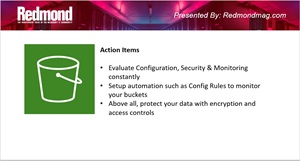 [Click on image for larger view.] Action Items (source: Carlos Rivas).
[Click on image for larger view.] Action Items (source: Carlos Rivas).
He expanded on each point during the session, drawing on practical experience and AWS-native services.
1. Evaluate Configuration, Security & Monitoring
Misconfiguration remains the top vulnerability in S3. As Rivas put it, "misconfigured information is going to be the number one, and you're going to find out there something that is public that shouldn't have been public. And you usually find out when it's already too late". He emphasized routine checks of bucket policies, public access settings, and logging.
To strengthen monitoring, he pointed to AWS CloudTrail and GuardDuty. CloudTrail can provide a full record of actions within S3, though he cautioned that in busy environments the logs can quickly become overwhelming. GuardDuty, on the other hand, is "probably the number one tool when it comes to monitoring CloudTrail events," offering more real-time detection of unusual activity such as mass downloads.
2. Automate Monitoring with Config Rules
Rivas highlighted AWS Config as a foundational tool. It allows teams to continuously check S3 against compliance requirements and best practices, from ensuring versioning is enabled to prohibiting public writes. Importantly, Config can also take corrective action without human intervention. "If there's an S3 bucket that is not encrypted, you can use Config Rules to enforce encryption to automatically against the will of the user that created the bucket. It will go ahead and turn on encryption."
He also explained how tagging strategies make automation scalable. Instead of configuring rules for each bucket, tags like "production" or "sensitive" can be used to apply policies across dozens or even hundreds of resources at once.
3. Protect Data with Encryption and Access Controls
Encryption is now enforced by default in S3, but Rivas recommended going further by using AWS Key Management Service (KMS) or customer-managed keys. "I don't think I have a single deployment out there these days that doesn't use encryption, unless it's just a proof of concept," he said.
He also covered network-level protections, such as private S3 endpoints inside a VPC to keep traffic off the public internet, and object-level sharing with pre-signed URLs. For stricter cases, explicit deny policies can act as an emergency brake. "What you can do is create one bucket policy and just have a deny statement, deny everything ... everything gets blocked. You know, nobody can read, nobody can write. It's like frozen in time."
Beyond encryption, Rivas encouraged organizations to adopt cross-region replication for disaster recovery, and to consider tools like Amazon Macie, which scans S3 for sensitive data such as credit card or Social Security numbers that may have been stored inadvertently.
The Bottom Line
For Rivas, these three action items form the core of any S3 security posture. Evaluating and monitoring configurations prevents accidental exposures, automation keeps oversight consistent across environments, and encryption plus access controls ensure that even compromised data is unusable to attackers. In a service as widely deployed as S3, he stressed, constant vigilance is essential.
For more on Amazon S3 security best practices, see the official AWS documentation on S3 security best practices.
And Much More
Those are all concise summaries, of course, and you need to watch the on-demand replay to get the individual items fleshed out in detail -- along with many other actionable tips -- but this gives you the overall idea of Rivas' presentation.
And, although replays are fine -- this was just today, after all, so timeliness isn't an issue -- there are benefits of attending such summits and webcasts from Virtualization & Cloud Review and sister pubs in person. Paramount among these is the ability to ask questions of the presenters, a rare chance to get one-on-one advice from bona fide subject matter experts (not to mention the chance to win free prizes).
With all that in mind, here are some upcoming summits and webcasts coming up in the next month or so from our parent company:
About the Author
David Ramel is an editor and writer at Converge 360.