In-Depth
What's New in the GA Release of Microsoft Windows Admin Center
Extension and Storage Spaces Direct support, plus some security changes are among some of the new features in the GA release of "Project Honolulu."
I looked at project "Honolulu" a little while ago but now that it's been released for general availability, it's time to have another look.
It's been renamed to Windows Admin Center (WAC) and has added support for Storage Spaces Direct (S2D) on Windows Server 2016. The promised support for extensions has also started to bear fruit with several already available. This article was written on the 1804.25 build of WAC.
WAC will come built into the next version of the server technology -- Windows Server 2019. Interestingly, Microsoft is saying that WAC won't replace Server Manager, but I suspect that as more and more features make it into WAC, the need for Server Manager will wane. What won't change, though, is the size expectation for WAC -- if you have tens of servers to manage (and you're doing it today with a combination of Server Manager and MMC consoles), WAC is definitely a tool for you to consider (especially because it's free). On the other hand, if you have hundreds of servers, perhaps with System Center Configuration Manager (SCCM) and System Center Operations Manager (SCOM) already deployed, WAC isn't going to replace those tools, although the Squared Up extension helps with SCOM integration.
WAC is built on HTML5 and Angular and supports 18 languages.
Deployment
WAC is a single MSI download with no reliance on IIS or a SQL database. It uses remote PowerShell and WMI over WinRM to remotely interact with managed nodes. If you're managing Windows Server 2012 or 2012 R2, make sure Windows Management Framework (WMF) 5.1 or higher is installed on those nodes.
There are two main deployment modes -- Windows 10 or gateway mode. The former works fine for small environments, your management PC (which should be a Privileged Access Workstation [PAW]) connects directly to each managed server. It could also be installed on a server, which in turn manages other servers (and itself) and you connect to it to manage nodes (which could be in Failover Clusters).
In gateway mode you connect to the server from administrative workstations and it in turn connects you to each managed node. If you become reliant on WAC, a new option is to install it in an Active-Passive mode in a Failover Cluster.
A nice touch is the ability to add tags to server connections so that you can group and filter them based on workload (DC, Exchange, Hyper-V) or environment (Prod, QA), for example.
Extensions
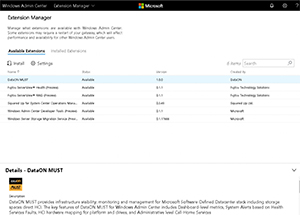
As Microsoft promised during the Honolulu preview, WAC supports extensions. In fact, most of the tools available in a new WAC installation are included plug-ins for such tasks as viewing processes and services or managing Storage Replica and devices.
 [Click on image for larger view.]
WAC Extensions
[Click on image for larger view.]
WAC Extensions
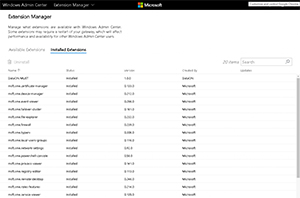
At the time of writing there were six additional extensions available (Settings | Extension Manager | Available Extensions); MUST from DataON for managing its Hyper Converged failover clusters, two from Fujitsu for managing its physical servers -- one for server health and one for the RAID setup. Squared Up works with its management of SCOM and the extension for Windows Server Storage Migration service works with this new service in Windows Server 2019. Finally, the Developer tool for WAC is available as an extension. The extension list that you see in WAC is a NuGet feed that Microsoft maintains, you can find out more information from the Build 2018 session THR2016.
 [Click on image for larger view.]
WAC Extension List
[Click on image for larger view.]
WAC Extension List
The SDK is available here and guidance for building extensions is here.
Security
A lot has changed between the preview and this final product when it comes to security. In gateway mode (running on a Windows Server 2016 host), users can either have the Gateway user role, where they can connect to servers through it, but not change settings on the gateway itself, or the Gateway administrator role. The latter can manage user settings for the gateway, as well as how they authenticate. Note that for both roles, there's still a requirement to authenticate to the servers that are being managed using valid administrative credentials. There's an interesting twist to this functionality that I think will be popular in security-conscious environments. When a user attempts to connect to a server to manage it, if they're an administrator on the target system they're given full access. If they're not, however, WAC checks to see if they're a member of the pre-defined Just Enough Administration (JEA) RBAC role -- if so they'll be connected using this more restricted session.
Interestingly, you can now choose between two identity providers, Active Directory/local machine groups or Azure Active Directory. With AD you can optionally enforce smartcard authentication and with Azure AD you can optionally use conditional access and multi-factor authentication, provided your Azure AD license supports those features. If you select the Azure AD option you have to connect the gateway to Azure, which creates an application in your Azure AD tenant, where you control the user access.
WAC
logs management activities to the Windows Event Log from the source SMEGateway, which can help you audit administrative activities.
Azure
Speaking of Azure, you can use an on-premises WAC to manage Infrastructure-as-a-Service (IaaS) virtual machines (VMs) in Azure. If they have public IPs (probably not a good idea for production assets) you can open the right ports, both on the Windows Firewall and in the Network Security Group (NSG) on the vNet. If, on the other hand, your VMs don't have public IPs, you'll need to use a VPN or ExpressRoute connection to connect the WAC to the VMs. A third option is to run WAC on a VM in Azure and then connect to it for management.
As in the preview -- if you've integrated WAC with Azure, you can enable Azure Site Recovery for an on-premises VM with a simple click.
My Cluster
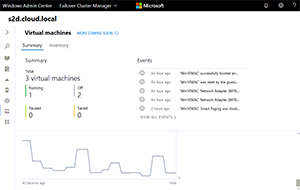
My S2D cluster on Windows Server 2016 showed up in WAC as a normal Failover Cluster. When I tried adding it as an HCI cluster (steps here) it refused to work, with an error message to the fact that another dll version of the resource already existed. I'm not sure if this is related to the latest cumulative update for Windows Server 2016 (1805, WAC requires Cumulative Update 1804). A nice feature for HCI are the new contextual safety checks. You'll get a big red warning if you try to take a volume offline when VMs are still running on it, or if a repair job is running and you try to pause a server for maintenance. If you've chosen mirror accelerated parity (mixing parity and mirroring on the same volume) you can now control the ratio in WAC, from 70 percent parity to 30 percent mirror or 80/20, 90/10. There's a great learning resource on GitHub for Windows Admin Center and S2D clusters.
 [Click on image for larger view.]
The WAC Dashboard for a Failover Cluster
[Click on image for larger view.]
The WAC Dashboard for a Failover Cluster
What's Missing
There are still a few things missing from WAC. You can add servers manually one by one or provide a CSV file with server names, but there's no discovery function to automatically find servers/clusters to manage or even search AD for them.
And while Fujitsu is leading the charge by integrating its server hardware management into WAC, where's HP, Dell and Lenovo?
Overall, though, WAC is coming together nicely, especially for Hyper-V and HCI environments.
About the Author
Paul Schnackenburg has been working in IT for nearly 30 years and has been teaching for over 20 years. He runs Expert IT Solutions, an IT consultancy in Australia. Paul focuses on cloud technologies such as Azure and Microsoft 365 and how to secure IT, whether in the cloud or on-premises. He's a frequent speaker at conferences and writes for several sites, including virtualizationreview.com. Find him at @paulschnack on Twitter or on his blog at TellITasITis.com.au.