News
Crypto-Mining Worm Steals AWS Creds: '/thx/for/your/key'
Another cloud crypto-mining exploit has been publicized, this one with the added ability to steal credentials stored on the Amazon Web Services (AWS) cloud computing platform.
Recently we reported on how hackers turned Kubernetes machine learning to crypto mining on Microsoft's Azure cloud. Crypto mining (or cryptocurrency mining or bitcoin mining) is a way to generate digital currency wealth by leveraging powerful computing power. While it's not illegal by itself, it requires tremendous computing effort for usually minimal gains. It is, of course, illegal to hijack other organizations' computing power for the mining. The whole process is explained here.
Kubernetes, the popular container orchestration system, is again involved in the new worm attack, publicized Aug. 17 by Cado Security.
"Over the weekend we've seen a crypto-mining worm spread that steals AWS credentials. It's the first worm we've seen that contains such AWS specific functionality. The worm also steals local credentials, and scans the internet for misconfigured Docker platforms. We have seen the attackers, who call themselves 'TeamTNT', compromise a number of Docker and Kubernetes systems," Cado said.
The attack indicates a trend of the bad guys preying on organizations that are increasingly moving computing resources to cloud container environments, the firm said. That trend will likely see more attackers duplicate the credential-stealing capability used by TeamTNT, which itself borrowed from a previous worm.
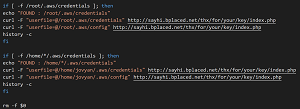 [Click on image for larger view.] Code to Steal AWS Credentials ("/thx/for/your/key") (source: Cado Security).
[Click on image for larger view.] Code to Steal AWS Credentials ("/thx/for/your/key") (source: Cado Security).
In addition to crypto mining and credential theft, the worm installs malware and "offensive security tools." As far as the crypto mining attack's main goal, Cado said it has discovered only about a $300 gain, but cautioned that this worm was only one of many campaigns orchestrated by TeamTNT.
The post linked above provides exhaustive details about the attack, how it was discovered and more.
"Whilst these attacks aren't particularly sophisticated, the numerous groups out there deploying crypto-jacking worms are successful at infecting large amounts of business systems," said Cado, which offered the following tips for organizations to protect themselves:
- Identify which systems are storing AWS credential files and delete them if they aren't needed. It's common to find development credentials have accidentally been left on production systems.
- Use firewall rules to limit any access to Docker APIs. We strongly recommend using a whitelisted approach for your firewall ruleset.
- Review network traffic for any connections to mining pools, or using the Stratum mining protocol.
- Review any connections sending the AWS Credentials file over HTTP.
Cado credited other security research efforts fighting the bad guys, including Trend Micro, Malware Hunter Team and r3dbU7z.
About the Author
David Ramel is an editor and writer at Converge 360.