In-Depth
The Missing Piece in the Zero Trust Puzzle
The core principles of Zero Trust, Assume Breach, Least Privilege and Verify Explicitly, are slowly trickling through organizations' approach to cybersecurity. It's hard, because you can't just buy it, and it involves people and process just as much as it does technology. In the Microsoft world, most of the building blocks have been in place for some time, including Entra ID for authentication and authorization, identity governance to ensure users only have the access they need, and Defender XDR + Sentinel for spotting the inevitable breaches before they turn into major incidents. But the network has until recently been a weak spot, either because users are working in locations not protected by your fancy enterprise-grade firewalls, or because they've used a traditional VPN to connect to on-premises resources, in many cases bypassing most of your protections.
In this article I'll look at Microsoft's entry in the Secure Services Edge (SSE) market, Global Secure Access (GSA), and the different flavors of it, Internet Access and Private Access. Another buzzword for this kind of technology is Zero Trust Network Access, ZTNA.
That's a Good-Looking Suite
There are at least seven definitions of the word "suite" in the English language, and one is "a set of programs with a uniform design and the ability to share data," which is most likely the meaning of the Entra Suite license (as opposed to "a set of coordinating furniture" or "a group of people in attendance on a monarch or other person of high rank"). It includes:
- Entra Private Access
- Entra Internet Access
- Entra ID Governance
- Entra ID Protection
- Entra Verified ID
We'll focus on the first two, but I'll cover all five and how they work together to provide a Zero-Trust fabric for your organization, no matter where the resources your users are accessing are located, and irrespective of where they are connecting from. The suite is $12 per user per month, if you already have Entra ID P2 licensing or Microsoft 365 E5, which already includes identity protection, parts of ID governance and parts of verified ID, there's special pricing available so you don't pay twice for the same features.
Accessing Corporate Resources
When I started my career in IT, accessing corporate resources involved dial-up modems and clunky approaches to access file shares and databases. As connectivity improved, we swapped to Virtual Private Network (VPN) tech, nearly always with a user action component -- connect to the internet first, then do a second connection to access on-premises resources. As any network architect will tell you, the big problem here is once your device is connected, it's part of the network, as if the device was sitting on the LAN in the office. This gives an attacker that has compromised your device, or malware planted there, extensive access to attack other resources in the corporate environment and thus move laterally to other systems. Furthermore, as we've discovered (and continue to discover) the edge devices that we connect through from supposedly responsible cybersecurity vendors have holes big enough to drive a Borg cube through and not even scrape the sides.
This is where SSE or it's cousin, Secure Access Service Edge (SASE), enters the arena. SASE includes Wide Area Networking convergence, which SSE doesn't, and Entra Global Secure Access provides only SSE (today). Using various approaches, SSE/SASE services are cloud hosted, and provide a range of security features to connect clients with resources in a secure fashion, based on strong authentication methods.
Microsoft's unique approach is integrating with the rest of the Entra ID stack and using familiar building blocks such as Conditional Access (CA) Policies that most IT pros are familiar with.
For several years there's been the Entra ID application proxy, which allows you to provide secure access to on-premises web-based applications (only) and publish those for your users in Entra ID, alongside other SaaS apps that you've published, so Salesforce could be sitting next to the internal (not available on the web) vacation booking app in your MyApps portal.
Private Access, however, takes this to a whole new level by providing access to any on-premises application, no matter the protocol. And there's no VPN involved, nor do you need to open any inbound port in your corporate firewall. Need your IT administrators to RDP into servers after hours -- no worries, create a policy in two minutes. Worried about security? Require phishing resistant MFA for each connection. And if your users need access to traditional file shares, that's also just a few clicks away.
You do need an agent on the endpoint for both Private and Internet access, as eventually the Windows client will be built-in, but today it's a separate installation, as is the macOS agent (currently in preview), the Android client or the iOS agent (again in preview). Note that the iOS agent only supports Microsoft 365 and Private Access traffic, with internet traffic filtering coming in the first half of 2025.
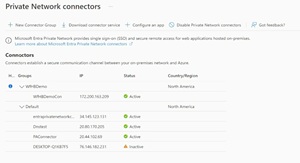 [Click on image for larger view.] Private Network Connectors
[Click on image for larger view.] Private Network Connectors
For Private access you also need at least one connector on a Windows server on-premises that has line of sight to the resources you want users to access from outside the network, this is what facilitates the outgoing connectivity so that you don't need to open inbound ports on your edge firewall(s). It's really just a newer version of the Entra ID application proxy mentioned above.
To get up and running quickly, there's a Quick Access option where you specify internal Fully Qualified Domain Names (FQDNs) and IP addresses that you want to publish into an application segment. You can also add private DNS suffixes so that the GSA agent knows how to resolve names of internal resources, plus you can configure a single sign-on (SSO) setup for accessing resources using Kerberos. Quick Access relies on an enterprise application being registered in Entra ID, to which you grant users and groups access, if you want them to be able to use Private Access. This is the first step in deploying Private Access, which can also be the start of your migration off your VPN.
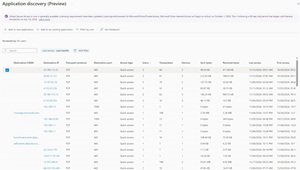 [Click on image for larger view.] List of Discovered Applications
[Click on image for larger view.] List of Discovered Applications
Quick Access is great for getting started, but after a while you'll probably want to implement different policies for different applications. A new feature called Application discovery is currently in preview, able to track every application accessed and show you the FQDN, IP protocol flavor, port(s), number of users, devices, sent and received bytes, first and last access. Based on this, you can create individual applications which will inherit the users and groups assigned through Quick access, which you can then trim down for each application.
It's really easy to get started with, and the granular control you get allows you to provide access to only a particular application, for just the people that should have access.
For both Private and Internet access, you then use Universal Conditional Access to add the conditions you need for each access. Without GSA, you can enforce phishing-resistant MFA, connectivity only from corporate devices and no sign-in risk for access to a specific SaaS cloud app, for example. With GSA you can do the same for access to any resource. To make this even easier, the connector is now available in the marketplace in the three major clouds, taking the setup from 30 minutes+ to 5 minutes.
You also get Universal Continuous Access Evaluation (CAE) so that if your need to disable access to resources, you can kill the sessions immediately, without the underlying apps supporting it. Normal CAE only works with applications specifically supporting it, with GSA, all connections are flowing through the agent, so if you disable the user's account, all sessions are terminated within a few minutes.
Notice the power you get over access to any application (SSH/RDP to a server, file share, web app, printer and so on) by combining Private Access with Conditional Access. You can add conditions to connections (from outside the corporate network) to a particular application such as MFA, corporate enrolled device, compliant with your policy, sign-in and user risk posture and so on. And this is per app. The difference between this and a traditional VPN is stark and greatly reduces the risk of lateral movement from one resource to another.
The Internet Is a Scary Place
There are various reasons you want to limit what websites users can visit from their work devices, and traditionally we do this with a firewall in the office. But of course, staff often aren't in the office anymore, instead working from anywhere. Entra Internet Access allows you to create web content filtering policies and group them together into security profiles, which are then targeted to groups of users using Conditional Access policies, which apply no matter where the device is.
An addition (at the end of 2024) is TLS inspection, which is currently in preview, a standard feature of many firewalls and Secure Web Gateways (SWGs). Not only does this allow the finding of malware and other nastiness in traffic, but it also gives more granular control for web category filtering. For example, if you block gambling, but not news, and a site hosts both types of content, the current model can't differentiate the separate parts of the site, but with TLS inspection it can apply filtering to the correct areas.
Microsoft already has two other features in products that do similar things to Internet Access, the first one being Defender for Endpoint, which has web content filtering support as well.
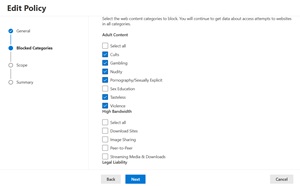 [Click on image for larger view.] Web Content Filtering in Defender for Endpoint
[Click on image for larger view.] Web Content Filtering in Defender for Endpoint
If you're using a different EDR for your endpoints, the power of having web filtering centrally managed through CA policies and being able to target different cohorts with different policies is a plus in the GSA column, as is the upcoming TLS inspection.
There's one third party service integration (with more on the way) available for Internet Access, Netskope (preview), which allows you to do advanced threat protection on the traffic, as well Data Loss Prevention (DLP).
Identity Governance
This area of the Entra Suite could easily fill another article, but essentially this takes the base Entra ID platform and extends it with automation for Joiner, Mover and Leaver scenarios. It automatically assigns users the right applications and resources for their job role, and automatically (with supervisor approval if preferred) changes the access when a user moves to another department, and removes access when the user leaves. There are also Access Reviews to regularly review if the access granted is still required, and also tools to manage external guest users in the organization.
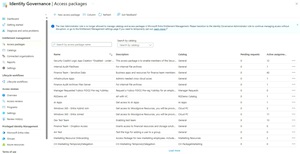 [Click on image for larger view.] Identity Governance Access Packages List
[Click on image for larger view.] Identity Governance Access Packages List
Identity Protection
IdP has been part of Entra ID P2 licensing for several years and is the basis for the sign-in and user risk tracking features. Every sign-in is evaluated in real time for characteristics such as which device is the user signing in from, what's their location, time of day, is it a device we've seen before or a new one, plus many others. You then apply a CA policy that can enforce an extra MFA if the risk is higher to make sure the user is who they say they are. User risk on the other hand is tracked over time, and based on other signals, with an important one being if the user's credentials are found exposed on the internet. It's very common for users to use their work credentials on other sites, and sometimes the same password, which means that if that site is compromised, criminals will test those credentials for Microsoft 365 access. If a user's risk is elevated, you can have a policy to enforce a self-service password change (with an MFA first) on the next sign in.
Verified ID
This is another feature that deserves a deeper dive in a different article, but at the core, this is about the user being in control of their own identity details and being able to control the sharing of these with different services. One of the features here is Face Check in the Microsoft Authenticator app which can identify a user based on a selfie picture compared with their known picture, it's privacy preserving because only the pass / fail result is shared.
Conclusion
It's early days for GSA, which was released to General Availability mid-2024. As you can see, there's been quite a few features added since, with more on the way. Later in 2025, support for BYOD / unmanaged devices is coming, as well as DLP polices for network traffic.
Traditional VPNs bring a host of business / cyber risk and managing them, both from an end user experience point of view, and for administrative effort is resource intensive. Global Secure Access is a modern approach to solving the resource access problem, without compromising security, using technology your administrators are already familiar with.