How-To
Protecting Amazon EC2 Instances Against Removal
Many organizations use a mixture of both persistent and temporary Amazon EC2 virtual machine instances. The persistent instances may run mission-critical workloads and are intended for long term use, while temporary instances are created and removed on an as needed basis. The problem is that with so many instances being constantly created and deleted, it can be easy to accidentally terminate an instance that you did not intend to remove. Thankfully, there are a few things that you can do to protect yourself against the loss of a critical instance.
First and foremost, it's important to make sure that you are backing up any instance that you plan on using for an extended period of time. Backups represent your best option for getting your instance back in the event that the instance is accidentally deleted.
Another way that you can safe guard your instances is by enabling termination protection. Termination protection is a safeguard that will not allow an instance to be deleted, though it is possible to disable termination protection and then remove the instance.
You can enable termination protection as a part of the instance creation process, but it is also possible to enable termination protection for an instance that already exists. To do so, open the EC2 console and click on the instance that you need to protect. Next, click on the Actions menu and then choose the Instance Setting option, followed by the Change Termination Protection option, as shown in Figure 1. This will cause AWS to display the Change Termination (Deletion) Protection dialog box. All you have to do now is to select the Enable checkbox and then click Save, as shown in Figure 2.
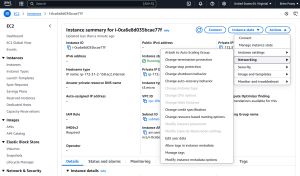 [Click on image for larger view.] Figure 1: The Termination Protection Option Is Found in the Instance Settings Section.
[Click on image for larger view.] Figure 1: The Termination Protection Option Is Found in the Instance Settings Section.
 [Click on image for larger view.] Figure 2: You Can Turn on Termination Protection by Selecting the Enable Checkbox and Clicking Save.
[Click on image for larger view.] Figure 2: You Can Turn on Termination Protection by Selecting the Enable Checkbox and Clicking Save.
You can turn on termination protection by selecting the Enable checkbox and clicking Save.
Even though Termination Protection can protect an instance from being deleted, it's always possible that someone will disable termination protection and then delete an instance. One way that you can reduce the chances of an instance being accidentally removed is to create a policy within your organization stating that termination protection should only be used for instances that are intended for long term use.
If termination protection were to be used for both long term and short term instances, then disabling termination protection would become a normal part of the instance remove process and would do little to protect your long term instances against accidental deletion since every instance uses termination protection.
On the other hand, suppose that an admin tries to delete a short term instance, but clicks on the wrong instance and ends up attempting to delete a long term instance. In this situation, the termination protection warning should immediately signal to the admin that they are doing something wrong since termination protection is only being used to protect instances that truly need to be protected.
But what if, in spite of your best efforts, someone deletes a mission critical instance anyway?
Normally, when you terminate an instance, the instance is fully removed. At that point, your only option for getting the instance back is to restore a backup. However, there is a way to prevent an instance from being fully deleted when the instance is terminated.
When you terminate an instance, AWS deletes the instance itself and it deletes the underlying EBS volume, though additional volumes that are attached to the instance are not usually deleted automatically. You can however, configure AWS to not delete instance volumes. That way, if an instance is accidentally terminated, its volumes and the data that they contain will remain. As such, you can just create a new instance and configure it to use the terminated instance's volumes.
It's best to configure this type of volume protection at the time that the instance is created. To do so, expand the Storage section on the Launch an Instance screen and set the Delete on Termination value to No, as shown in Figure 3.
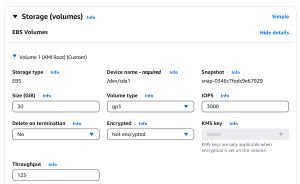 [Click on image for larger view.] Figure 3: Set the Delete on Termination option to No.
[Click on image for larger view.] Figure 3: Set the Delete on Termination option to No.
For a root volume that is attached to an existing instance, you will have to use the command line to enable this protection. The command is:
aws ec2 modify-instance-attribute --instance-id --block-device-mappings file://mapping.json
You will also have to supply a JSON file similar to this one:
[
{
"DeviceName": "device_name",
"Ebs": {
"DeleteOnTermination": false
}
}
]
Keep in mind that you will need to replace device_name with the actual device name (such as /dev/sda1).
Finally, one last thing that you can do to protect your important instances is to use tagging as a way of identifying the instances that should not be terminated. Tagging won't do anything to prevent your instances from being terminated, but it can help to identify your important instances, decreasing the chances that someone will accidentally attempt to terminate those instances.
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.