In-Depth
A Look at Security in the Microsoft Cloud
A high-level overview of the security features on offer in Microsoft 365 -- covering what you can do in the lower-level SKUs, as well as what the higher-level SKUs provide.
An interesting shift is starting to happen when I talk to prospects and clients in my IT consultant role. They want to know that the solution or service I'm proposing is going to solve their business problem, but they tend to finish with, "Is it going to be secure?" And if they don't ask the question and actively push back when I bring it up -- I've started to simply say "No, unless you consider the security implications and take appropriate steps to mitigate the risks, I won't work with you."
In this article I'm going to take a high-level overview of the security features on offer in Microsoft 365 (SaaS), and cover what you can do in the lower-level SKUs, as well as what the higher-level SKUs provide. Next month I'll do the same for Azure (PaaS and IaaS). Taken together these two articles should provide a foundation to take to decision makers and work to improve the security of your Microsoft cloud deployments.
Office 365
I'll start with Office 365. The two main flavors that I find in business are Business/Business Essentials/Business Premium and Enterprise E1/E3/E5.
The Business SKUs top out at 300 users and they all provide mail filtering for spam and malware, mobile device management (for Office 365 app access), basic data governance (manually apply labels to documents -- no automatic policies, though), and eDiscovery searches (but no advanced eDiscovery Machine Learning assistance or eDiscovery exports).
Given their target market, it's not surprising that some of the "bigger business" features are missing (but see Microsoft 365 Business in the next section of this article). Nevertheless, there are many things a business can do to improve its security. First, make sure all global administrators (and other privileged accounts such as Exchange administrator -- rarely used in smaller businesses) use multi-factor authentication (MFA) for their accounts. Second, create a separate day-to-day account for any administrator that's just a normal account that they use for everything but administrative tasks. Train users in recognizing phishing attempts via e-mail or other channels, and institute manual checkup processes for financial staff so that if the "CEO" sends an e-mail to the accounting department and asks them to transfer $20,000 to a new supplier there's a manual phone checkup before the transfer is authorized.
Implementing MFA for all users is of course the ultimate end goal, but you'll need to train everyone (including support staff) before turning it on. One limitation in the Business SKUs is that you can't specify IP address ranges where MFA isn't applied (head office), meaning that the prompts may annoy users. Set the time that a successful MFA is remembered on a trusted device to the maximum (60 days) to minimize the irritation for users and make sure everyone installs and configures the free Microsoft Authenticator app on their phones as it provides the smoothest experience. According to Microsoft's statistics, using MFA mitigates 99 percent of all identity attacks.
On the Enterprise side of the fence (no limit on number of users) most businesses are on E3, reasoning that E5 doesn't provide enough value to justify the price gap. When it comes to security, nothing could be further from the truth. E3 adds to the security features in the Business SKUs with Data Loss Prevention (DLP) to stop users accidentally sharing sensitive information, export of eDiscovery results, the ability to put mailboxes on litigation hold based on eDiscovery searches and unlimited archive mailboxes (compared to 50GB in the Business SKUs).
E5, however, brings the full nine yards for security. On top of E3 it adds advanced eDiscovery, which can sort through mountains of data to find the important stuff based on a little bit of training from you, potentially saving hundreds of hours of work, advanced threat management which lets you control access by Microsoft engineers to your data (customer lockbox), the ability to educate your users with fake phishing campaigns and Threat Intelligence. Furthermore, you get Office 365 Cloud App Security, a slightly scaled down (but still very useful) version of Microsoft's Cloud App Security Broker (CASB) focused on your users' activity in Office 365. For the full details on what's available in Office 365 see these Service Descriptions.
The real deal when it comes to security, however, comes in the Microsoft 365 SKUs, not the Office 365 subset.
Microsoft 365
These SKUs also come in a Business version and Enterprise versions. In addition to Office 365 they also include Enterprise & Mobility + Security (EMS) and Windows 10 Enterprise licensing.
Microsoft 365 (M365) Business provides (on top of Office 365 Business) Azure Information Protection (AIP), Office 365 Message Encryption (OME), in-place/litigation hold and data loss prevention, along with self-service password reset with AD write-back, device write-back to AD from Azure AD, conditional access, application proxy, Advanced Threat Analytics (ATA), MDM auto-enrollment, Mobile Application Management (MAM), the ability to manage devices and their security profile, and self-service Bitlocker recovery (see Figure 1). Out of that list of security features the most important ones are OME, the ability to send protected e-mails to anyone with an e-mail address so that only that person can open the e-mail and AIP, the ability to protect documents (including PDF) with user rights that travel with the file so that you can send a sensitive document to four people and know that they can't forward it to others or print/copy from the document (if those are the rights you've restricted). Of course, this doesn't prevent someone from taking pictures of it with their phone or turning the laptop upside down on the photocopier but it's hard to claim that you did that by mistake. Another highlight is Conditional Access (CA), the ability to control access to Office and third-party applications depending on where the user is located (at the time of login), the device, the sensitivity of the application and so on. And instead of just granting or preventing access you can ask for further proof with MFA -- and once they're in you can limit their actions in the application. Finally, ATA is a comprehensive way of discovering intruders in your on-premises AD environment.
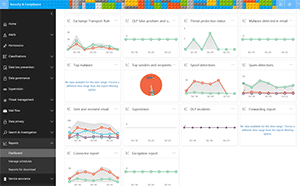 [Click on image for larger view.]
Figure 1. The Microsoft 365 Security & Compliance dashboard.
[Click on image for larger view.]
Figure 1. The Microsoft 365 Security & Compliance dashboard.
Any small business that's serious about security should definitely include Microsoft 365 on its wish list -- particularly as several of these security features were previously reserved for the enterprise SKUs.
M365 E5 adds
Azure Advanced Threat Protection, (basically the same application as ATA, but hosted by Microsoft instead of you having to deploy it on-premises),
Office 365 Advanced Threat Protection (yes, I know it's confusing, Microsoft has at least four "ATP" services) for safe links and safe attachments in e-mails and Teams. You also get the full
Cloud App Security, a full-fledged CASB that'll protect and analyze your users' cloud application access. Advanced eDiscovery uses machine learning to analyze large datasets across e-mail, documents and other data sources to make sure you gather the right information with a minimal amount of manual work.
Secure Score
All O365 and M365 customers can access Secure Score for no extra cost in the Security and Compliance Center (see Figure 2). This is a single place to view all the possible security controls that you can enable in a tenant, along with a score. As you mitigate risks by turning on security settings, your score will increase. You can compare your score to that of other tenants, of a similar size and in the same industry as you. And you can clearly see what impact a particular setting will have on your user's experience, along with what risk it'll mitigate.
Any O365/M365 administrator should use Secure Score to implement all the security controls (that I've listed in this article) of which they're able.
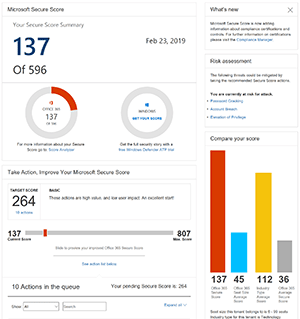 [Click on image for larger view.]
Figure 2. Microsoft 365 Secure Score dashboard.
[Click on image for larger view.]
Figure 2. Microsoft 365 Secure Score dashboard.
Wrapping Up
Security is a process, not an end goal. Microsoft provides a comprehensive, and ever-evolving, set of security features in O365/M365, the main issue I see with clients is that they aren't aware of what's available or simply choose not to use what they've actually paid for.