News
NSA Offers Cloud Security Mitigation Guidance for Top Vulnerabilities
In the wake of yet another massive cloud data leak, the National Security Agency (NSA) has published "Mitigating Cloud Vulnerabilities" guidance.
In fact, the report is dated Jan. 22, the same day Microsoft reported that a security misconfiguration in an Azure-hosted database exposed 250 million technical support accounts.
Similar misconfigurations have haunted the Amazon Web Services (AWS) platform in recent years, also.
It's no surprise then, that the NSA led off its guidance with the No. 1 vulnerability, misconfiguration, which it described as having widespread prevalence but requiring low attacker sophistication.
"While CSPs [Cloud Service Providers] often provide tools to help manage cloud configuration, misconfiguration of cloud resources remains the most prevalent cloud vulnerability and can be exploited to access cloud data and services," the NSA said. "Often arising from cloud service policy1 mistakes or misunderstanding shared responsibility, misconfiguration has an impact that varies from denial of service susceptibility to account compromise. The rapid pace of CSP innovation creates new functionality but also adds complexity to securely configuring an organization’s cloud resources."
The report provides this handy graphic depicting the shared responsibility model:
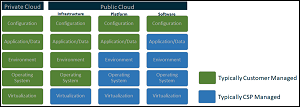 [Click on image for larger view.] Cloud Shared Responsibility Model (source: NSA).
[Click on image for larger view.] Cloud Shared Responsibility Model (source: NSA).
For actual misconfiguration mitigation advice, the report offers some 27 different items, depending upon an organization's situation and goals.
"Proper cloud configuration begins with infrastructure design and automation," the report said. "Security principles such as least privilege and defense-in-depth should be applied during initial design and planning. Well-organized cloud governance is also key to a defensible environment. Technical controls for implementing these principles vary by CSP but often include cloud service policies, encryption, Access Control Lists (ACLs), application gateways, Intrusion Detection Systems (IDSs), Web Application Firewalls (WAFs), and Virtual Private Networks (VPNs). A well-designed and well-implemented cloud architecture will include controls that prevent misconfigurations or alert administrators to improper configurations."
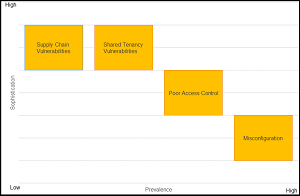 [Click on image for larger view.] Cloud Vulnerabilities – Prevalence versus Sophistication of Exploitation (source: NSA).
[Click on image for larger view.] Cloud Vulnerabilities – Prevalence versus Sophistication of Exploitation (source: NSA).
Other vulnerabilities for which mitigation guidance is given include:
- Poor Access Control -- Prevalence: widespread; Attacker Sophistication: moderate: Poor access control occurs when cloud resources use weak authentication/authorization methods or include vulnerabilities that bypass these methods. Weaknesses in access control mechanisms can allow an attacker to elevate privileges, resulting in the compromise of cloud resources.
- Shared Tenancy Vulnerabilities -- Prevalence: rare; Attacker Sophistication: high: Cloud platforms consist of multiple software and hardware components. Adversaries who are able to determine the software or hardware used in a cloud architecture could take advantage of vulnerabilities to elevate privileges in the cloud. Vulnerabilities in cloud hypervisors (i.e., the software/hardware that enables virtualization) or container platforms are especially severe due to the critical role these technologies play in securing cloud architectures and isolating customer workloads.
- Supply Chain Vulnerabilities -- Prevalence: rare; Attacker Sophistication: high: Supply Chain vulnerabilities in the cloud include the presence of inside attackers and intentional backdoors in hardware and software. CSPs source hardware and software from across the globe and employ developers of many nationalities. Third-party software cloud components may contain vulnerabilities intentionally inserted by the developer to compromise the application. Inserting an agent into the cloud supply chain, as a supplier, administrator or developer, could be an effective means for nation state attackers to compromise cloud environments.
"Managing risk in the cloud requires that customers fully consider exposure to threats and vulnerabilities, not only during procurement but also as an on-going process," the report concludes. "Clouds can provide a number of security advantages over traditional, on-premises technology, such as the ability to thoroughly automate security-relevant processes, including threat and incident response. With careful implementation and management, cloud capabilities can minimize risks associated with cloud adoption, and empower customers to take advantage of cloud security enhancements. Customers should understand the shared responsibility that they have with the CSP in protecting the cloud. CSPs may offer tailored countermeasures to help customers harden their cloud resources. Security in the cloud is a constant process and customers should continually monitor their cloud resources and work to improve their security posture."
The NSA seems to be taking a more active role in cloud/enterprise security lately. For example, for its first Patch Tuesday release of the year, Microsoft included a patch for a vulnerability affecting the latest versions of Windows that was discovered and reported to Microsoft by the NSA.
The NSA report can be accessed here.
About the Author
David Ramel is an editor and writer at Converge 360.