News
Report Details Evolving 'Good vs. Evil' Cybersecurity Struggle
VMware's new Carbon Black cybersecurity report breaks things down into the most basic of concepts: the eternal cat-and-mouse struggle between "good" and "evil."
In more prosaic terms, the VMware Carbon Black 2020 Cybersecurity Outlook report released last week details the kinds of threats facing organizations -- including a ransomware resurgence -- along with information on how attackers are evolving and improving their techniques and how enterprises themselves need to evolve in order to combat the bad guys and their new nefarious ways.
"The conflict of 'good vs. evil' is a theme that's captivated humanity throughout history, spanning religion, ethics, philosophy, politics, art, literature, and cinema," the report says. "Often with larger-than-life characters leading the narrative, the 'good vs. evil' conflict reveals humanity's intrinsic desire to be safe amidst an omniscient and, often, ephemeral sense of fear.
"In cybersecurity, this conflict plays out on a daily basis, where 'good' is represented by the unsung cybersecurity heroes and 'evil' is represented by an aggregation of nation-state actors, cybercriminals, hackers, industrial spies, hacktivists, and cyber terrorists -- all with different agendas rooted in a desire to tip the balance of power in their favor."
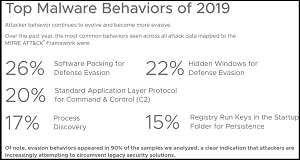 [Click on image for larger view.] Malware Behaviors (source: VMware).
[Click on image for larger view.] Malware Behaviors (source: VMware).
To better address the "good-vs.-evil" conflict, VMware said the report seeks to understand attacker behaviors, using the MITRE ATT&CK framework as a research backdrop in order to learn about the top attack tactics, techniques, and procedures (TTPs) seen during the past year. With an understanding of these behaviors, the report further provides specific guidance on how organizations can deal with ransomware, commodity malware, wipers, access mining, and destructive attacks. MITRE ATT&CK is a globally accessible knowledge base of adversary tactics and techniques based on real-world observations used as a foundation for the development of specific threat models and methodologies.
Furthermore, in addition to understanding attackers' behavior, the company commissioned Forrester Consulting to study the specific behaviors exhibited by defenders on the "good" side of the struggle, including CISOs and CIOs. With behavior analysis of both sides, the report provides advice to defenders on subjects ranging from software packaging to dealing with defensive evasion techniques such as "hidden window," which, as its name suggests, involves hiding windows in order to conceal malicious activity from users.
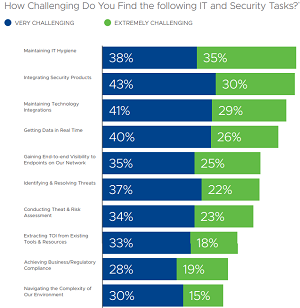 [Click on image for larger view.] Challenging Tasks (source: VMware).
[Click on image for larger view.] Challenging Tasks (source: VMware).
Six main highlights of the report as compiled and presented by VMware include:
- Defense Evasion Behavior: Attacker behavior continues to become more evasive, a clear sign that attackers are increasingly attempting to circumvent legacy security solutions. Defense evasion behavior was seen in more than 90 percent of the 2,000 samples we analyzed.
- Wiper Destructive Attacks:
Wipers continue to trend upward as adversaries (including Iran) began to realize the utility of purely destructive attacks. Leveraging techniques across the full spectrum of MITRE ATT&CK. Wipers rely heavily upon defense evasion techniques to avoid detection (64 percent of analyzed samples).
- Ransomware Resurgence:
Ransomware's evolution has led to more sophisticated Command and Control (C2) mechanisms and infrastructure for attackers. Cyber criminals continue to leverage standard application protocols in network deployments to operate under the radar and blend in with standard business traffic.
- IT vs. Security: IT and security teams appear to be aligned on goals (preventing breaches, efficiency, incident resolution), but 77.4 percent of survey respondents said IT and security currently have a negative relationship, according to our study conducted by Forrester Consulting.
- Understaffed Defense: Nearly 50 percent of both IT and security respondents reported being understaffed with security respondents noting their teams are currently 48 percent understaffed, on average, and IT teams are 26 percent understaffed, on average, according to the study.
- The Talent Gap: The talent gap continues to be a theme across the IT and security landscape. According to the study, 79 percent of respondents said finding the right security talent is either "very challenging" or "extremely challenging" and 70 percent reported the same level of challenge for IT talent.
"Defenders must stop thinking about how to achieve results on their own," said Rick McElroy, one of the report's authors, in a statement. "Defenders must continue to build bridges with IT teams. The time for cooperation is now. We can no longer afford to go at this problem alone. We need IT teams to look toward security solutions that are built in and not bolted on. It's time for security to become part of our organizational DNA. It's time security becomes intrinsic to how we build, deploy and maintain technology."
The methodology detailed in the report says it used data from a variety of sources that provided more than 2,000 samples that were analyzed and graphed with the MITRE ATT&CK framework.
About the Author
David Ramel is an editor and writer at Converge 360.