News
As Virtualized RANs Emerge in 5G Efforts, Security Concerns Arise
As Radio Access Networks (RANs) get more attention with the ongoing rollouts of 5G networks, at least one firm is bringing up security concerns associated with the new virtualized technology.
RAN tech figured prominently in the recent 5G breakthrough claimed by Verizon: the first fully virtualized 5G data session in a live network in the U.S.
Verizon explained the key tech used for 5G rollouts this way: "In order for your cell phone to connect to a network or the internet, it connects first through a radio access network (RAN). Radio access networks utilize radio transceivers to connect you to the cloud."
Samsung provided its commercial 5G virtualized RAN solution for the effort.
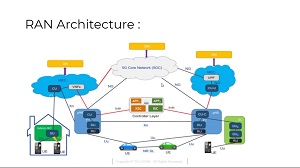 [Click on image for larger view.] RAN Architecture (source: TELCOMA).
[Click on image for larger view.] RAN Architecture (source: TELCOMA).
But it's another RAN implementation, O-RAN, that was the subject of a security-related post by 5G player Ericsson.
"Continued study and further work efforts are required to ensure that security, integrity and resilience of Open RAN architectures are preserved across future deployments," Ericsson said.
O-RAN is a version of the generic Open RAN ecosystem that was standardized by the O-RAN Alliance, which provided an O-RAN reference architecture.
Ericsson listed possible benefits to this new approach to RAN architecture, including:
- Lower deployment cost (commoditized hardware)
- Increased supply chain diversity (more vendors)
However, the company said it could potentially increase network integration costs and complexity, which is the point of the company's quote listed above.
Along with those concerns, the company's post listed potential expanded threat and attack surfaces in networks, such as:
- New interfaces increase threat surface -- for example, open fronthaul, A1, E2, etc.
- Near-Real-Time (RT) RIC and 3PP xApps introduces new threats that could be exploited
- Decoupling of hardware increases threat to Trust Chain
- Management interfaces may not be secured to industry best practices
- (not exclusive to O-RAN): adherence to Open Source best practices
"5G has the promise to be the foundational platform for the global digital economy by providing secure connectivity for everything and everyone," Ericsson said. "As the industry evolves towards RAN virtualization, with virtual RAN or Open RAN (O-RAN), it is important that a risk-based approach is taken to adequately address security."
Ericsson recommended that O-RAN implementations provide the following security measures:
- Protect expanded threat surface due to more interfaces and functions
- Close security vulnerabilities with Near-Real-Time RIC
- Address threat to trust chain introduced by decoupling of functions
- Ensure management interfaces are secured according to industry best practices using TLS and digital signing
- Practice a higher level of due diligence for exposure to public exploits from use of Open Source code
- Implement defenses from physical attacks
The post is based on a more comprehensive paper titled Security Considerations of Open RAN, which goes into much greater detail about the issue.
About the Author
David Ramel is an editor and writer at Converge 360.