News
Windows Server 2022 Is Coming!
The big theme of Windows Server 2022 is security -- primarily bringing the concept of Secure Core from Windows client to the server world with Secure Core Servers.
The next version of Windows Server will be known as 2022 and it's in public preview since Ignite in March 2021. The Long-Term Servicing Channel (LTSC=five years mainstream + five years extended support) release is planned for later in 2021.
There was a time when this would have been huge news, with (nearly) every IT shop on the planet looking for new features that were going to make their life easier and planning how to convince bosses to approve the upgrade. That's not really the case anymore.
The preview news had a single 30-minute presentation devoted to it, and half that presentation covered updates to Azure and Windows Admin Center, tangentially connected to Windows Server.
This isn't to say that there aren't some interesting things coming that will probably make your life easier, but it sends a clear message -- Windows Server isn't a priority at Microsoft like it was some years ago. We have two sources for what new features we can expect -- the presentation at Ignite, as well as the Semi-Annual Channel (SAC) releases of Windows Server. If you have Software Assurance for your Windows Server licenses and you want to use the latest from the server team -- there are actually two releases each year of Windows Server with new features, as long as you don't mind using Server Core only and upgrade at least every 18 months. This blog post from August 2020 and this one from September 2020 are more sources for what's coming.
A Strong Focus on Security
The big theme of Windows Server 2022 is security -- primarily bringing the concept of Secure Core from Windows client to the server world with Secure Core Servers. This is a type of PC that you can buy from Microsoft, Lenovo, Dell, Panasonic, HP and others that has a Trusted Platform Module (TPM) 2.0 chip, Bitlocker turned on and Virtualization Based Security (VBS) to protect credentials while the system is running. Instead of enabling these (and other) security features after taking delivery, it's all turned on out of the box.
On servers this will protect against boot kits and root kits, malware designed to compromise the system before it starts, thus bypassing any defenses running in the OS. To carry the label Secure Core Server the OEM must provide secure firmware and drivers and enable these features by default.
To be able to audit this across a fleet of servers, there's a new extension for Windows Admin Center that lists which of the six requirements a server meets. Here's a one-year-old Dell Hyper-V host with quite a few missing.
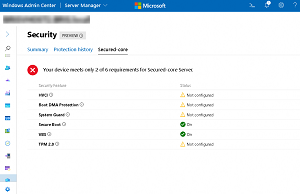 [Click on image for larger view.] Windows Admin Center Secure Core Features(source: Microsoft).
[Click on image for larger view.] Windows Admin Center Secure Core Features(source: Microsoft).
There's been some interesting work in the security community over the last few years, demonstrating issues with the TPM platform, as they're a separate component on the motherboard and the traffic between it and the rest of the system can be manipulated. This new Secure Core Server platform lays the foundation for the forthcoming Pluton security processor, built on technologies first incorporated into Xbox One. Pluton will be different than TPM as it will be part of the CPU itself, all three main vendors, Qualcomm, Intel and AMD are on-board with Pluton.
Each of the six areas shown above protects different parts of the boot process and the OS so let's look at them in detail. TPM stores Bitlocker keys and other secrets and key material while Secure Boot verifies signatures on boot software (UEFI firmware, EFI applications and the OS itself) to ensure that they haven't been subverted by a root kit.
Virtualization-based Security (VBS) uses hardware virtualization (based on Hyper-V technology but don't think of this as a separate VM, just an isolated part of the memory space in the OS) to stop credential attacks like Pass-the-Hash through Mimikatz. On top of VBS is Hypervisor-Enforced Code Integrity (HVCI) which protects modification of the Control Flow Guard (CFG) bitmap, provides a valid certificate for Credential Guard and checks that device drivers have an EV certificate. Control Flow Guard lets Windows protect itself against malicious applications that corrupt memory of legitimate applications.
System Guard sits on top of these features and provides the following security guarantees for Windows: protects the integrity of the system as it starts up and validate this through local and remote attestation using Static Root of Trust for Measurement (SRTM), Dynamic Root of Trust for Measurement (DRTM) and System Management Mode (SMM) protection (see more).
Boot Direct Memory Access (DMA) protection is part of Kernel DMA Protection which protects Bitlocker keys and other secrets stored in memory while the OS is running. The classic attack here is to plug a drive with malware into a port that offers DMA on a running PC and read Bitlocker keys from memory. DMA offers fast transfer of data, essentially directly into memory (as it says on the tin) but also comes with this risk -- Boot DMA mitigates it. These improvements aren't just for Windows, Microsoft wants to bring the improved boot security to Linux as well, just as they're doing in Azure.
Apart from the Secure Core Server features, Windows Server 2022 will come with the newest version of Transport Layer Security (TLS), 1.3 enabled by default and offers AES 256-bit encryption for SMB traffic.
Windows Server 2022 will also make it possible to give containers an identity in Active Directory using group Managed Service Accounts (gMSAs) which you can only do today by domain joining the host -- this won't be required in 2022.
 [Click on image for larger view.] Windows Server 2022 preview build 20317.1 -- it looks like Windows Server 2016/2019(source: Microsoft).
[Click on image for larger view.] Windows Server 2022 preview build 20317.1 -- it looks like Windows Server 2016/2019(source: Microsoft).
Networking Improvements
There is one feature coming that I think any IT Pro dealing with on-premises deployments and access will love and that's MsQuic. This implements the QUIC protocol and Microsoft has open sourced their flavor.
You'll see several improvements -- HTTP/3 will be faster and SMB traffic will also be faster. On top of this you'll be able to set up file shares on-premises and access them securely from anywhere without the need of VPNs. Ned Pyle from Microsoft has a video and description here.
The TCP protocol will determine the best transfer rate faster using TCP HyStart++ and PktMon will improve packet capture. Newer network cards that support UDP Segmentation Offload (USO) will speed up UDP traffic, in a similar way to how TCP is accelerated today.
If you're using Kubernetes and containers, Direct Server Return will speed up traffic by allowing incoming and outgoing traffic to take different paths. And full support for Calico is now on the table. Kubernetes doesn't manage networking between containers and Calico is an example of a Container Network Interface (CNI) plug-in that relies on Kubernetes Network policies to secure traffic. Going forward Windows containers will respect the policies and be managed just like Linux containers using Calico. The overall size of Windows containers has also been significantly reduced.
Containers will also be able to use virtualized time zones, today the time zone in a container is controlled by the host's, going forward you can control the time zone in a container using the virtual registry key, the tzutil tool or using a Docker argument when starting the container.
In the Hyper-V switch Windows Server 2019 offered Receive Segment Coalescing (RSC) which combines multiple packets in the virtual switch for lower CPU load, but the traffic was broken up again as it was sent over the VMbus, in 2022 it'll remain combined all the way to the application.
Hyper-V Improvements
Mixed domain or workgroup clusters have been available for a little while but if you wanted to use Bitlocker on each cluster node (and you REALLY should), they had to be in the same domain. In Windows Server 2022 you can store the key in local encrypted storage, opening up this scenario.
Keeping VMs together on the same host for speed or separate for resiliency (keeping Domain Controllers on separate nodes) in a cluster can be done today with Affinity and AntiAffinity rules. They're however not very easy to use, nor are they site aware in stretched clusters. In Server 2022 there are new PowerShell cmdlets to set up rules which are easier to set up and who do understand geo clusters.
On the scalability front this release will support 48 TB of memory and 2,048 logical processors per host which is ridiculously large (and incredibly expensive), but will find at least one good customer, Azure where large databases and SAP deployments are demanding ever larger VMs and hosts.
Summary
Although this list of new features is a bit underwhelming there's no doubt that there are some worthwhile features on the way, primarily under the hood.
And many, many businesses rely on Windows Server, whether it's running on-premises or in a cloud so the rumors of its demise are vastly exaggerated. I expect more reveals of features as we progress through 2021 towards the final release.
My recommendation is to
join the community and sign up to the
Windows Server Insider program. The latest preview was
released on March 24.