News
Survey Shows Zero Trust Confusion
So what's this Zero Trust thing popularized by Forrester Research?
A lot of people are asking the same thing, according to new research from One Identity, which offers Zero Trust functionality in its for-sale unified identity security products.
"According to the Dimensional Research-conducted survey of 1,009 IT security professionals, Zero Trust is a main security priority for most organizations, but comprehensive understanding and adoption of the Forrester-founded framework remains inconsistent," the Aliso Viejo, Calif., company said last week in announcing the Zero Trust and IT Security report.
Zero Trust is emerging along with best practice techniques like regular system backups and using Multi-factor Authentication (MFA) in the fight against ransomware, which is regularly making headline news as one attack (and corresponding ransom payout) after another are reported.
One Identity says Zero Trust is: "A proven model for implementing robust and selective security, Zero Trust eliminates vulnerable permissions, unnecessary and excessive access in favor of specific-rights delegation and provisioning with granularity."
The ZT security model has been described as part of the future of network security, and Microsoft recently backed it to fight ransomware while investing in early ZT advocate Rubrik.
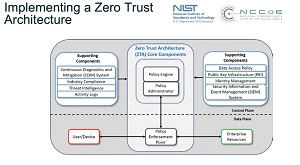 [Click on image for larger view.] Zero Trust Architecture (source: NIST).
[Click on image for larger view.] Zero Trust Architecture (source: NIST).
The model eschews the standard security approach of walling off networks and systems behind a secure perimeter. It's one of the latest security darlings in an industry that has seen the advent of hybrid work models, the proliferation of endpoints and bring-your-own devices, disparate and interconnected systems spanning clouds and enterprise datacenters, and just general complexity all around. Instead of trying to secure perimeters, ZT assumes that such fortress security approaches are destined to fail and that systems have already been penetrated, seeking to lessen the damage that can be caused.
Along with poor understanding of the term that has actually been around since 1984, adoption rates don't seem to align with its purported importance among enterprises and organizations.
"While 75 percent of organizations recognize Zero Trust as being critically or very important to bolstering overall cybersecurity posture, only 14 percent report that they have fully implemented a solution," One Identity said. "Another 39 percent of organizations have begun to address this important need, and an additional 22 percent noted that they plan to implement Zero Trust over the course of the next year."
Other highlights of the report as presented by One Identity include:
-
IT security teams getting started with Zero Trust in a variety of ways:
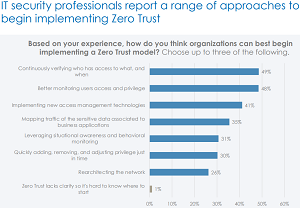 [Click on image for larger view.] Getting Started (source: One Identity).
[Click on image for larger view.] Getting Started (source: One Identity).
-
Top recommendations for getting started with Zero Trust include continuously verifying access
(49 percent) and betting monitoring user access and privilege (48 percent)
-
61 percent of companies are reconfiguring access policies and 51 percent are implementing new technology
as part of their Zero Trust implementation
-
Multiple barriers remain to Zero Trust adoption
- Only 21 percent say they are "very confident" in their organization’s understanding of Zero Trust
- 94 percent report challenges with implementing Zero Trust
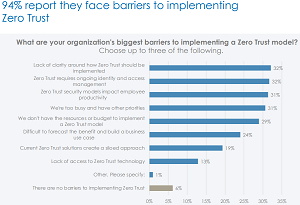 [Click on image for larger view.] Barriers (source: One Identity).
[Click on image for larger view.] Barriers (source: One Identity).
- Challenges include lack of clarity (32 percent), other priorities (31 percent), and lack of resources (29 percent)
"Organizations recognize that the traditional perimeter is no longer enough and that they will be best served by prioritizing identity security and taking steps to ensure bad actors are limited once they gain access," said Bhagwat Swaroop, president and general manager, One Identity. "Zero Trust is fast becoming an enterprise imperative because it eliminates vulnerable permissions and excessive access by delivering a continuum of different rights across the organization to ultimately limit attack surfaces if they are breached."
As far as methodology for the report, One Identity said independent sources of IT security stakeholders were invited to take part in an online survey in which a variety of questions were asked about adoption and experiences with Zero Trust security, with responses being captured Sept. 8-27, 2021.
About the Author
David Ramel is an editor and writer at Converge 360.