News
Zero Trust Study Shows Gaps Remain
Despite the Zero Trust security model being heralded as integral to the future of network security, a new study revealed many gaps in enterprise implementations.
Zero Trust eschews the standard security approach of walling off IT systems behind a secure network perimeter. It has grown in popularity with the advent of hybrid work models, the proliferation of endpoints and bring-your-own devices, disparate and interconnected systems spanning clouds and enterprise datacenters, and just general complexity all around. Instead of trying to secure perimeters, Zero Trust assumes that such fortress security approaches will fail or have already been penetrated, seeking to lessen the damage that can be caused.
 [Click on image for larger view.] Zero Trust Principles (source: Microsoft).
[Click on image for larger view.] Zero Trust Principles (source: Microsoft).
Zero Trust is an increasingly popular security approach as organizations are besieged by sophisticated ransomware and other cybersecurity exploits. It has been adopted by major cloud players like Microsoft to fight ransomware and has been described as the future of network security.
A new Global State of Zero Trust Report from Zero Trust vendor Fortinet echoes findings from other studies that indicated problems with understanding and implementing Zero Trust.
"Although many organizations have a vision for Zero Trust, that vision isn't necessarily being translated into the solutions they're able to put in place," Fortinet said of the study based on a survey of 472 IT and security leaders from 24 different countries conducted in September 2021. In fact, more than half of organizations can't authenticate users and devices on an ongoing basis and are struggling to monitor users post-authentication, as shown in this report graphic:
 [Click on image for larger view.] Gaps to Address in Zero Trust Strategy (source: Fortinet).
[Click on image for larger view.] Gaps to Address in Zero Trust Strategy (source: Fortinet).
Along with implementation gaps, enterprises report several challenges in building a Zero Trust strategy, starting with a lack of qualified vendors with a complete solution.
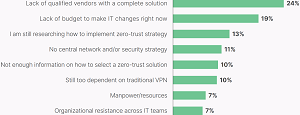 [Click on image for larger view.] Most Significant Challenge Building Zero Trust Strategy (source: Fortinet).
[Click on image for larger view.] Most Significant Challenge Building Zero Trust Strategy (source: Fortinet).
Despite those gaps, respondents see benefits to a Zero Trust solution, including:
- Security across the entire digital attack surface -- (listed by 22 percent of respondents)
- Better user experience for remote work (VPN) -- (19 percent)
- Quickly adapt to rapidly evolving network changes -- (19 percent)
What's more, a vast majority of the respondents reported they already have a Zero Trust and/or ZTNA (Zero Trust Network Architecture) strategy in place or development. And 40 percent report that their strategy is fully implemented.
Other highlights of the report include:
- "Minimizing the impact of breaches and intrusions" tops the priorities list at 34 percent, followed closely by "securing remote access" and "ensuring business/mission continuity" at 33 percent.
- The respondents to the survey indicated that they think they understand Zero-Trust (77 percent) and ZTNA (75 percent) concepts and are confident in providing secure access.
- While respondents report that they're well-versed in Zero-Trust concepts, over 80 percent felt that implementing a Zero-Trust strategy across an extended network wasn't going to be easy. Most of them (60 percent) report it would be moderately or very difficult, and another 21 percent said it would be extremely difficult.
- One striking statistic was that most survey respondents reported that they already have a Zero-Trust and/or ZTNA strategy in place or development, with over one-third saying they are fully implemented. Only 6 percent haven't started implementation yet.
- A vast majority of the survey respondents acknowledge that it is vital for Zero-Trust security solutions to be integrated with their infrastructure, work across cloud and on-premises environments, and be secure at the application layer.
"A proper Zero-Trust solution is all about knowing exactly who and what is on the network at any given moment and that authenticated users and devices are only provided with the minimum level of access for them to do their job," Fortinet said in its conclusion. "So, when organizations report that they aren't able to authenticate users and devices on an ongoing basis and struggle to monitor users for authentication, Zero Trust isn't doing its job."
As noted, the report's findings are similar to other industry studies. Last month, for example, Virtualization & Cloud Review reported on a One Identity report about Zero Trust and IT Security in the article "Survey Shows Zero Trust Confusion."
"According to the Dimensional Research-conducted survey of 1,009 IT security professionals, Zero Trust is a main security priority for most organizations, but comprehensive understanding and adoption of the Forrester-founded framework remains inconsistent," One Identity said.
About the Author
David Ramel is an editor and writer at Converge 360.