News
Hackers Target Microsoft 365 'Legacy Authentication' 10x More than MFA, Report Says
Just in case the drumbeat to adopt Multi-Factor Authentication (MFA) hasn't yet sunk in, a new report from Okta reveals that organizations using Microsoft 365 "Legacy Authentication" (like passwords) are much more likely to be attacked by hackers.
How much more likely? Here are some data points:
- Attackers are targeting accounts using Legacy Authentication to Microsoft 365 at rates 10 or more times higher than accounts using modern authentication protocols, depending on the industry. On average across all industries, organizations using Microsoft Legacy Authentication face a 53 times higher ratio of threats to authentications.
- There is at least a 90 percent reduction in the ratio of threats to authentications when an organization denies access using Legacy authentication.
- Government organizations using Microsoft Legacy Authentication face a 104 times higher ratio of threats to authentications.
- Education organizations using Microsoft Legacy Authentication face a 65 times higher ratio of threats to authentications.
- Wholesale trade businesses using Microsoft Legacy Authentication face a 58 times higher ratio of threats to authentications.
- Healthcare organizations using Microsoft Legacy Authentication face a 36 times higher ratio of threats to authentications.
Those data points are included in Okta's latest Businesses at Work report, the eighth annual edition from the San Francisco-based identity provider specialist. The report seeks to explore how organizations and people work today, based on data from the company's more than 14,000 global customers and the Okta Integration Network, which includes more than 7,000 integrations with cloud, mobile and web apps, as well as IT infrastructure providers.
Specifically, the security aspects of the report rely on a year's data collected by a homegrown ThreatInsight tool that detects potentially malicious IP addresses, which was designed to prevent credential-based attacks.
"Here's what we found: Microsoft Legacy Authentication is simply more vulnerable to attack than modern forms of authentication. This means that organizations allowing legacy forms of auth are more frequently subject to credential-based attacks," said Okta CEO and co-founder Todd McKinnon in a Jan. 25 blog post.
The report provided more details.
"This year we wanted to test the hypothesis that attackers are deliberately targeting Microsoft 365 accounts in organizations that allow Legacy Authentication. Microsoft calls 'Legacy Authentication' any method to authenticate to Microsoft 365 that doesn't support MFA. Accounts with Legacy Authentication enabled are far more vulnerable to credential stuffing because the security of the account relies on the strength of user-defined passwords."
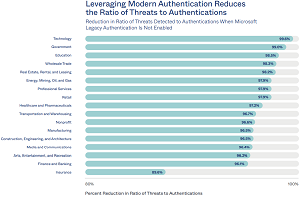 [Click on image for larger view.] Leveraging Modern Authentication Reduces the Ratio of Threats to Authentications (source: Okta).
[Click on image for larger view.] Leveraging Modern Authentication Reduces the Ratio of Threats to Authentications (source: Okta).
Indeed, Microsoft has published guidance like "New tools to block legacy authentication in your organization" (March 2020) and "How to: Block legacy authentication to Azure AD with Conditional Access" (December 2021).
What's more, Microsoft-centric organizations soon won't have much of a say in the matter: The company's guidance includes a note, "Effective October 1, 2022, we will begin to permanently disable Basic Authentication for Exchange Online in all Microsoft 365 tenants regardless of usage, except for SMTP Authentication." Microsoft also provided some "stark" statistics of its own and published an RSA Conference 2020 graphic:
- More than 99 percent of password spray attacks use legacy authentication protocols.
- More than 97 percent of credential stuffing attacks use legacy authentication.
- Azure AD accounts in organizations that have disabled legacy authentication experience 67 percent fewer compromises than those where legacy authentication is enabled.
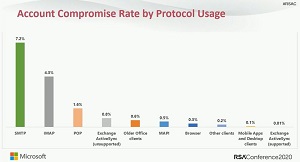 [Click on image for larger view.] Account Compromise Rate by Protocol Usage (source: Microsoft/RSA Conference 2000).
[Click on image for larger view.] Account Compromise Rate by Protocol Usage (source: Microsoft/RSA Conference 2000).
Another security mechanism figuring prominently in the report is Zero Trust, which eschews the standard security approach of walling off networks and systems behind a secure perimeter. It's one of the latest security darlings in an industry that has seen the advent of hybrid work models, the proliferation of endpoints and bring-your-own devices, disparate and interconnected systems spanning clouds and enterprise datacenters, and just general complexity all around. Instead of trying to secure perimeters, Zero Trust assumes that such fortress security approaches are destined to fail and that systems have already been penetrated, seeking to lessen the damage that can be caused. Microsoft recently touted Zero Trust as a security model to fight ransomware.
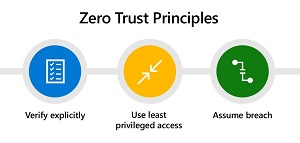 [Click on image for larger view.] Zero Trust Principles (source: Microsoft).
[Click on image for larger view.] Zero Trust Principles (source: Microsoft).
"Beyond MFA, Okta customers have demonstrated that they are sold on the vision of Zero Trust, and are rapidly progressing their journey from unified access management to contextual-based access," the Okta report said. "Customers are increasingly assessing the security behaviors of users and factoring in other risk signals at authentication."
The report found an increase in the number of customers putting Zero Trust building blocks in place:
- 31 percent increase in customers deploying WebAuthn.
- 9 percent increase in device trust configuration.
- 91 percent increase in risk-based policies.
Okta provided this graphic to illustrate the progress in the adoption of Zero Trust:
 [Click on image for larger view.] Progress in Adopting Zero Trust (source: Okta).
[Click on image for larger view.] Progress in Adopting Zero Trust (source: Okta).
The wide-ranging report also explores the most popular and fastest-growing apps, best tools for the job, the rise of multi-cloud and more. Here are some data highlights as presented by Okta:
- Apps at Work: 2021's most popular apps: Collaboration and security tools are the two most popular categories of tools deployed through the Okta Integration Network. Meanwhile, categories that support remote work are the fastest growing: design software (39 percent year-over-year growth), electronic signature tools (38 percent ) and cloud platforms (34 percent ).
- Fastest-growing apps: Seven out of the top 10 fastest-growing apps are brand new to the ranks: Notion, TripActions, Postman, Keeper, Airtable, Fivetran and Gong.
-
The best tools for the job:
- The average number of apps organizations deploy increased from 88 to 89 this year, contributing to an increase of 24 percent since 2016.
- Larger companies (2,000 employees or more) deploy more apps: 187 on average.
- The days of being a loyal, one-vendor shop are gone. Among Okta customers deploying Microsoft 365:
- 45 percent also deploy Zoom.
- 33 percent also deploy Slack.
- 38 percent also deploy Google Workspace, up from 36 percent in 2020.
- The rise of multi-cloud: The runaway favorite cloud platform is AWS, which grew 32 percent year over year and claims more than six times as many Okta customers than second-place Microsoft Azure and third-place Google Cloud Platform (GCP) grew 40 percent year over year.
"For many of us, 2021 felt like a continuation of the challenges of 2020 -- a year stuck in limbo," McKinnon said. "However, the most innovative companies found ways to push forward and evolve. Our data shows that organizations around the globe leaned heavily into two areas: choice and collaboration. This matches a drum we've beat since our inception, and we're excited to see more organizations around the world put them at the forefront of their technology strategies."
About the Author
David Ramel is an editor and writer at Converge 360.