News
Microsoft: Need for MFA 'Cannot Be Overstated'
"It's the Multi-Factor Authentication, stupid."
While Microsoft doesn't go quite that far, that's the gist of a new cyber threat intelligence brief introduced by the company, part of a new quarterly series.
Called Cyber Signals, the series starts out with a PDF offering called "Identity Is the New Battleground," which echoes pervasive industry cybersecurity guidance as to the importance of MFA, as recently covered by Virtualization & Cloud Review in the article "Hackers Target Microsoft 365 'Legacy Authentication' 10x More than MFA, Report Says."
Even though identity and MFA are top-of-mind cybersecurity concerns these days, Microsoft data indicates most organizations are still unprotected against identity attacks, as shown in this graphic:
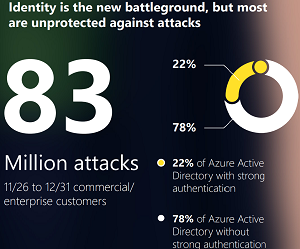 [Click on image for larger view.] Identity Is the New Battleground, but Most Are Unprotected Against Attacks (source: Microsoft).
[Click on image for larger view.] Identity Is the New Battleground, but Most Are Unprotected Against Attacks (source: Microsoft).
Using Microsoft threat data and research, Cyber Signals intends to provide a quarterly expert perspective into the current threat landscape through discussions of trending tactics, techniques and strategies used by notable threat actors.
With a focus on identity, MFA is a natural focus point for the inaugural brief.
"The need to enforce MFA adoption or go passwordless cannot be overstated, because the simplicity and low cost of identity-focused attacks make them convenient and effective for actors," the brief stated. "While MFA is not the only identity and access management tool organizations should use, it can provide a powerful deterrent to attacks."
The brief said a major source of threats are nation-state actors, who primarily try to steal or guess passwords via spear-phishing, social engineering attacks, and large-scale password-sprays.
"Microsoft gains insight into attackers' tradecraft and successes by observing what tactics and techniques they invest in and find success with," the brief said. "If user credentials are poorly managed or left vulnerable without crucial safeguards like multi-factor authentication (MFA) and passwordless features, nation-states will keep using the same simple tactics."
Recommendations to address the issue include:
- Enable multi-factor authentication: By so doing, they mitigate the risk of passwords falling into the wrong hands. Even better, eliminate passwords altogether by using passwordless MFA.
- Audit account privileges: Privileged access accounts, if hijacked, become a powerful weapon attackers can use to gain greater access to networks and resources. Security teams should audit access privileges frequently, using the principle of least-privilege granted to enable employees to get jobs done.
- Review, harden, and monitor all tenant administrator accounts: Security teams should thoroughly review all tenant administrator users or accounts tied to delegated administrative privileges to verify the authenticity of users and activities. They should then disable or remove any unused delegated administrative privileges.
- Establish and enforce a security baseline to reduce risk: Nation-states play the long game and have the funding, will, and scale to develop new attack strategies and techniques. Every network-hardening initiative delayed due to bandwidth or bureaucracy works in their favor. Security teams should prioritize implementing zero-trust practices like MFA and passwordless upgrades. They can begin with privileged accounts to gain protection quickly, then expand in incremental and continuous phases.
As that last item suggests, MFA and the Zero Trust security model often go hand-in-hand in such cybersecurity guidance, such as in the article "Ransomware Protection: Use MFA and 'Don't Trust Anyone or Anything'."
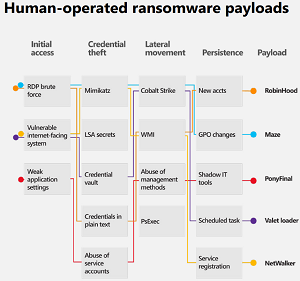 [Click on image for larger view.] Human-Operated Ransomware Payloads (source: Microsoft).
[Click on image for larger view.] Human-Operated Ransomware Payloads (source: Microsoft).
The brief also provides recommendations for defending against ransomware attacks, pointing out that while such exploits dominate cybersecurity mindshare right now, there are only a few primary strains, and ransomware groups aren't as monolithic as common perceptions indicate.
"That said, no matter how much ransomware is out there, or what strains are involved, it really comes down to three primary entrance vectors: remote desktop protocol (RDP) brute force, vulnerable internet-facing systems, and phishing," the brief said. "All of these vectors can be mitigated with proper password protection, identity management, and software updates in addition to a comprehensive security and compliance toolset. A type of ransomware can only become prolific when it gains access to credentials and the ability to spread. From there, even if it is a known strain, it can do a lot of damage."
About the Author
David Ramel is an editor and writer at Converge 360.