News
Biden Signs Metrics Bill to Combat Cybercrime into Law
President Joe Biden signed into law the Better Cybercrime Metrics Act, enlisting the FBI and other government agencies to spearhead a metrics reporting initiative. It's the latest in a string of White House cybersecurity measures enacted this year.
According to a May 5 White House statement, the act "establishes requirements to improve the collection of data related to cybercrime and cyber-enabled crime." Primary congressional backers of the bill were Rep. Abigail Spanberger (D-Va.) and Sen. Brian Schatz (D-Hawai'i), although the bill managed to garner rare bipartisan support in both the House and Senate, speaking to the gravitas of the situation.
The act will:
- Require the FBI to report metrics on cybercrime and cyber-enabled crime categories, just as they do for other types of property crime
- Encourage local and federal law enforcement agencies to report incidents of cybercrime in their jurisdictions to the FBI
- Authorize a study at the National Academies of Science to create a taxonomy for cybercrime incidents in consultation with federal, state, local, and tribal stakeholders, criminologists, and business leaders that would inform the FBI's reporting of cybercrime and cyber-enabled crime
- Require the Bureau of Justice Statistics at the Department of Justice and the Census Bureau to include questions related to cybercrime and cyber-enabled crime as part of its annual National Crime Victimization Survey
"By starting the process of building an effective system to track cybercrime incidents, her legislation will allow U.S. law enforcement agencies to better identify cyberthreats, prevent attacks, and take on the challenge of cybercrime," said a news release from Spanberger.
"The bipartisan bill, which will improve data collection on cybercrimes and give law enforcement and policy makers more tools to combat cybercrime in the United States, passed the Senate in December and the U.S. House of Representatives in March," said a news release issued by Schatz.
 [Click on image for larger view.] Better Cybercrime Metrics Act (source: U.S. Government).
[Click on image for larger view.] Better Cybercrime Metrics Act (source: U.S. Government).
The Biden administration has been active on the cybersecurity front as the nation faces increased attacks such as ransomware, which Spanberger alluded to: "One year ago this week, we saw the damaging effects of the ransomware attack on the Colonial Pipeline. In an instant, the American people saw how cybercrime -- now the most common crime in America -- could jeopardize the integrity of critical infrastructure, the American economy, and our national security."
That Colonial Pipeline attack resulted in a $4.4 million payout accompanied by a crippling gas shortage and $7-per-gallon gas gouging.
Ransomware bad actors, becoming increasingly sophisticated and acting much like organized corporations, come from all kinds of sources, including hostile nations, something Biden noted in March while pinning some blame on Russia.
"This is a critical moment to accelerate our work to improve domestic cybersecurity and bolster our national resilience," Biden said in a March 21 statement on the nation's cybersecurity. "I have previously warned about the potential that Russia could conduct malicious cyber activity against the United States, including as a response to the unprecedented economic costs we've imposed on Russia alongside our allies and partners. It's part of Russia's playbook. Today, my Administration is reiterating those warnings based on evolving intelligence that the Russian Government is exploring options for potential cyberattacks."
 [Click on image for larger view.] Ransomware Has Gone Global (source: Allan Liska).
[Click on image for larger view.] Ransomware Has Gone Global (source: Allan Liska).
The FBI, as with the new cybercrime act, is instrumental in advice the White House espoused in March to protect against potential cyberattacks:
- Mandate the use of multi-factor authentication on your systems to make it harder for attackers to get onto your system
- Deploy modern security tools on your computers and devices to continuously look for and mitigate threats
- Check with your cybersecurity professionals to make sure that your systems are patched and protected against all known vulnerabilities, and change passwords across your networks so that previously stolen credentials are useless to malicious actors
- Back up your data and ensure you have offline backups beyond the reach of malicious actors
- Run exercises and drill your emergency plans so that you are prepared to respond quickly to minimize the impact of any attack
- Encrypt your data so it cannot be used if it is stolen
- Educate your employees to common tactics that attackers will use over email or through websites, and encourage them to report if their computers or phones have shown unusual behavior, such as unusual crashes or operating very slowly
- Engage proactively with your local FBI field office or CISA Regional Office to establish relationships in advance of any cyber incidents. Please encourage your IT and Security leadership to visit the websites of CISA and the FBI where they will find technical information and other useful resources
It's probably no coincidence that Multi-Factor Authentication (MFA) tops that bullet-point list, as it's commonly cited -- along with other measures such as Zero Trust architectures -- as a top defense mechanism.
 [Click on image for larger view.] MFA GOOD! (source: Joey D'Antoni).
[Click on image for larger view.] MFA GOOD! (source: Joey D'Antoni).
Zero Trust has also gained government attention, as in January the U.S. Office of Management and Budget (OMB) published a strategy to move the government to a Zero Trust cybersecurity model.
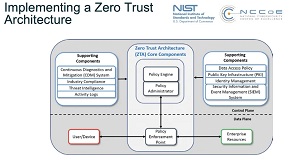 [Click on image for larger view.] Zero Trust Architecture (source: NIST).
[Click on image for larger view.] Zero Trust Architecture (source: NIST).
A May 5 Forbes article quoted Lisa Plaggemier, interim executive director at the National Cybersecurity Alliance, as saying, "The Biden administration has made no secret about making cybersecurity one of its top priorities.
"On a purely cyber level, for far too long the United States.... has operated in an opaque and uncoordinated manner when it comes to cybersecurity. And unfortunately, this has made it much easier to compromise American entities and has resulted in a widespread erosion of public trust."
About the Author
David Ramel is an editor and writer at Converge 360.