In-Depth
How Microsoft CIEM (CloudKnox) Addresses Cloud Management Challenges
Managing cloud, whether IaaS, PaaS or SaaS, has made our lives as IT pros more complex. As someone who has been in IT for nearly three decades, I long for the "good old days" (yes, I know I've got biased glasses on) when change wasn't such a constant wave towering over me.
Nowhere is this more evident than in how we now handle security, identity and permissions. Don't get me wrong, this article isn't against cloud, it's a statement of facts around the complexity of configuring and securing modern cloud environments. Overall cloud is more secure than what we had on-premises, but there's a lot of complexity in ensuring that it's configured correctly, with the shifting sands under our feet of daily updates, particularly in multi-cloud environments.
Across Google's GCP, Amazon's AWS and Microsoft's Azure there are more than 40,000 different permissions, with half of them high impact if compromised. And unlike say a fleet of Windows Servers 10 years ago in your datacenter where applications and OSes changed maybe every six months/few years, it's changing daily/weekly, maybe monthly if you're lucky. And complexity is the enemy of security. The more complex a system is, with multiple dependent components (sometimes with unexpected interactions), the more likely an attacker can find a gap to get in.
In this article we'll look at Microsoft Cloud Infrastructure Entitlement Management (CIEM), the new name for the CloudKnox product Microsoft recently acquired, and how it can help with these challenges.
Hyperscale Public Cloud -- Developers Gone Wild
I think one cause of the problem is the relentless drive for new services and features and being first to market with a Minimum Viable Product (MVP). In large clouds this leads to a proliferation of services, permissions to interact with each of them, and new roles to assign those permissions. Thus, the matrix of privileged accounts in your organization, exactly what they have access to, and the resulting effective permissions grows ever larger. And there's little time devoted to think it through, ensuring that the principle of "least privilege," a core tenet of Zero Trust, is adhered to. All users, whether end users or privileged accounts, should have access only to what they need to perform their duties. Easy to say, but hard to implement in practice in an ever-changing infrastructure.
Compare this to something most of us know, file permissions on a file share. It's IT 101: create one group for Sales, another for Marketing. Put the right user accounts into the right group, assign share and NTFS permissions to the groups and now Sales users can edit their own documents and read, but not change, Marketing documents. And those permissions should be able to stay relatively static for the next few years. The cloud equivalent is that the available permissions you can assign change every few months; the way you assign them change regularly and getting a report of exactly who's got access to what is a major project.
I've heard it said by analysts I respect that the issue with Azure (I hear similar things from folks who know AWS and GCP), is that there isn't a central security chief -- who lays down the law for all the teams building and improving services. Imagine if Windows server file permissions changed every version with additions by a group of developers who had a "good idea."
Meet Microsoft CIEM
Currently Microsoft CIEM is in public preview -- you can find instructions here on how to onboard. It involves three steps: first click on the link under Features highlights in the Azure AD portal, then run a single command in Azure AD cloud shell (or locally) to create a service principal.
 [Click on image for larger view.] Running the Script to Add a Service Principal to Your Azure AD Tenant
[Click on image for larger view.] Running the Script to Add a Service Principal to Your Azure AD Tenant
Finally, you click the button "Enable CloudKnox Permissions Management".
 [Click on image for larger view.] Enabling CloudKnox in a Tenant
[Click on image for larger view.] Enabling CloudKnox in a Tenant
Microsoft CIEM is designed to help alleviate the problems described above by giving you granular cross-cloud visibility for all accounts, all permissions and all actions taken. It also shows you the gap between permissions granted and the actual usage of those permissions, allowing you to right-size the permissions to get closer to least privilege. Plus, it looks for anomalies and gives you comprehensive reporting.
It uses Permissions Creep Index (PCI) to measure the difference between permissions assigned and those used. PCI ranges from 1 to 100, with bigger numbers indicating higher risk. You can also see PCI per cloud and see changes over time. If it increases sharply, it means that users have been granted more permissions (that they're not using) or more users with high permissions have been added. If, on the other hand, it's decreasing over time, it means you're right-sizing permissions for your administrators so there's less gap between what they're assigned and what they use. Microsoft CIEM collects data from each cloud hourly.
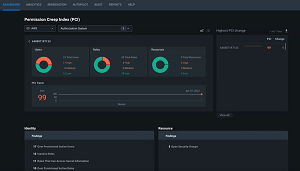 [Click on image for larger view.] Permission Creep Index Dashboard
[Click on image for larger view.] Permission Creep Index Dashboard
You can also see in the dashboard for a user if the assignment of roles is direct to that user or through that account being a member of a group. It'll also show you if the assignment is permanent or using Privileged Identity Management (PIM) in Azure where a user is eligible for a role but doesn't have that role permanently and must elevate to have those rights, for a limited amount of time. That elevation can involve an extra MFA, being approved by another user, having to enter a service ticket number and is time limited to the number of hours given to that role.
One interesting challenge in the cloud, (not so much on-premises because they weren't enforced in Active Directory) is the rise of workload/machine/non-human identities. Applications, VMs, containers and so forth are registered with Azure AD (or in AWS/GCP) and have permissions to access resources. These are a vector for attacks and often preferred by attackers (including the Russians in the SolarWinds hacks) because these accounts are less scrutinized. In CloudKnox these are inventoried alongside user permissions, and you can right-size them as well.
This all makes sense from a day-to-day perspective; I'm a user administrator and I've been granted too many permissions that I don't use -- Microsoft CIEM shows this, and I'm instead given a role with the right permissions for what I do. But what about the exceptional cases, where I need higher permissions on a one-off basis? That's where requesting permissions comes in -- another feature that lets you apply for permissions, either once or on a schedule, to be approved.
Roles, permissions, and usage is analyzed across all three clouds, and machine learning-powered anomaly and outlier detection alerts will notify you in case of suspicious activity. Reporting lets you dig in to used permissions by a specific user at a specific scope, for example. There are also specific reports for "Super users," people with very high permissions, especially when they have them across a large scope.
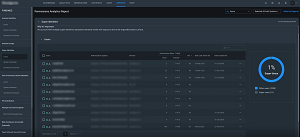 [Click on image for larger view.] Permissions Analytic Report Used and Granted
[Click on image for larger view.] Permissions Analytic Report Used and Granted
Microsoft CIEM currently integrates with ServiceNow, but I suspect a lot of work happening during this public preview phase has to do with integrating CloudKnox into the overall security portfolio from Microsoft.
Conclusion
There's one important limitation in the current preview: it can't be used in the EU, as it's not GDPR compliant. This is something that's planned for some time in 2022, along with the General Availability of the service. Licensing and cost haven't been revealed yet, but it looks like it's not going to be part of Azure AD Premium P2, for example, and more likely will be a separate service. This makes some sense as it'll be more attractive for larger companies and/or those with multi-cloud deployments.
I think Microsoft CIEM will be a great solution for mid-sized and larger businesses, as the problem it solves is a crucial one to get right and it's impossible to do manually.
About the Author
Paul Schnackenburg has been working in IT for nearly 30 years and has been teaching for over 20 years. He runs Expert IT Solutions, an IT consultancy in Australia. Paul focuses on cloud technologies such as Azure and Microsoft 365 and how to secure IT, whether in the cloud or on-premises. He's a frequent speaker at conferences and writes for several sites, including virtualizationreview.com. Find him at @paulschnack on Twitter or on his blog at TellITasITis.com.au.