News
Ransomware Payouts Can Be 'A Matter of Life or Death' but 'Don't Pay' Generally Advised
A new ransomware survey from Cybereason published during this week's RSA security conference reaffirms general industry advice to not pay off the attackers, but many do so when it becomes "a matter of life or death."
These observations come with the survey-based report titled "Ransomware: The True Cost to Business Study 2022" published by Cybereason, a specialist in extended detection and response (XDR). In addition to business disruptions, those true costs include senior leadership attrition, layoffs and more.
"The study also once again finds that 'it doesn't pay-to-pay' a ransom demand, as 80 percent of organizations that paid were hit by ransomware a second time, with 68 percent saying the second attack came in less than a month and 67 percent reporting that threat actors demanded a higher ransom amount," said Cybereason in a June 7 blog post.
Furthermore, among organizations who opted to pay a ransom demand in order to regain access to their encrypted systems, 54 percent said that some or all of the encrypted data was corrupted during the recovery process. That signifies a 17 percent year-over-year increase compared with last year's report when that number was 46 percent.
"These findings underscore why it does not pay to pay ransomware attackers, and that organizations should focus on detection and prevention strategies to end ransomware attacks at the earliest stages before critical systems and data are put in jeopardy" Cybereason said.
That advice jives with another recent report by data protection specialist Veeam titled "2022 Ransomware Trends Report," which found that many victimized organizations paid ransoms and recovered their data. However, nearly as many either recovered their data without paying the ransom or paid the ransom and still didn't recover their data.
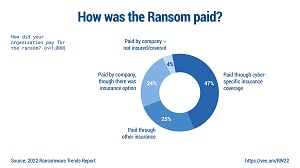 [Click on image for larger view.] How Was Ransom Paid? (source: Veeam).
[Click on image for larger view.] How Was Ransom Paid? (source: Veeam).
You can read more about the Veeam report in last month's article titled "Survey Shows Limits of Ransomware Insurance, Payoffs."
The Cybereason report, meanwhile, notes one scenario when many organizations opt to pay the ransom: when it becomes "a matter of life or death," and that's talking about actual human lives, not a corporation going out of business. "Nearly 30 percent of companies said they paid a ransom because of the risk to human life due to system downtime," Cybereason said.
That human life concern was listed as one of the top five reasons organizations reported for paying off a ransomware demand, with the others being avoiding revenue loss, expediting recovery, recovering data and being short-staffed.
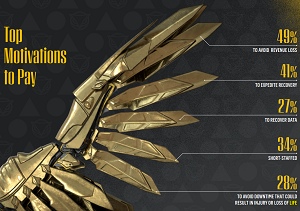 [Click on image for larger view.] Top Motivations to Pay (source: Cybereason).
[Click on image for larger view.] Top Motivations to Pay (source: Cybereason).
"The decision to pay a ransom demand is not easy, especially for organizations with a critical infrastructure designation like those in the Healthcare sector," the report said. "In cases where ransomware prevents access to crucial systems and data needed to provide care, the consequences could be dire the longer the attack persists. This urgency explains why nearly one-third of respondents (28 percent) said they paid the ransom demand because any delays in remediation could result in injury or loss of life."
In claiming that "it still does not pay to pay," the report listed concerns that organizations should weigh in making the decision, including:
- Will the attackers honor their promise to provide a decryption key and restore access to all systems and data?
- What if the data gets corrupted during the decryption process?
- What if the attackers reside in a country subject to sanctions where a ransom payment could be considered a criminal violation?
- What if paying a ransom demand encourages the threat actors to launch another ransomware attack against the organization?
- Aside from delayed data and system recovery, what are the other risks to the victim organization if the ransom demand is not met?
"The big takeaway from both this year's study and the last is that it really does not make sense to pay a ransom demand unless there is the risk of losses that go beyond monetary costs, such as when human life is at risk," the report said. "Overall, the cost of preventing a ransomware attack from being successful is lower than the combined cost of paying the ransom and all the associated costs of recovery when responding to a successful ransomware attack -- possibly multiple times by the same threat actor."
Other big takeaways as presented by Cybereason include:
- A Weak Supply Chain Leads to Ransomware Attacks: Nearly two-thirds (64 percent) of companies believe the ransomware gang got into their network via one of their suppliers or business partners.
- Senior Leadership Attrition: 35 percent of companies suffered C-level resignations following a ransomware attack.
- Ransom Demands Increase with Each Attack: Nearly 70 percent of companies paid a higher ransom demand the second time.
- Ransomware Attacks Lead to Business Disruptions: Nearly one-third (31 percent) of businesses were forced to temporarily or permanently suspend operations following a ransomware attack.
- Layoffs Result from Ransomware Attacks: Nearly 40 percent of organizations laid off staff as a result of the attack.
- Organizations Don't Have the Right Tools: 60 percent of organizations admitted that ransomware gangs were in their network up to6 months before they discovered them. This points to the double extortion model where attackers first steal sensitive data then threaten to make it public if the ransom demand is not paid.
The survey was conducted by Censuswide in April 2022 on behalf of Cybereason, polling 1,456 cybersecurity professionals from organizations with 700 or more employees.
About the Author
David Ramel is an editor and writer at Converge 360.