News
Report: Open Source Security Ignored by Many Organizations
The once-sorry state of secure open source software has been improving lately, but a new report indicates it's still being largely ignored by many organizations.
That report, "The State of Open Source Security 2022," a joint venture between developer security specialist Snyk and The Linux Foundation, an open-source-focused nonprofit organization, includes some potentially worrisome findings, including:
- Less than half (49 percent) of organizations have a security policy for OSS development or usage (and this number is a mere 27 percent for medium-to-large companies)
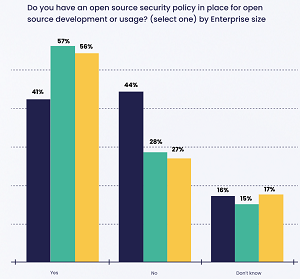 [Click on image for larger view.] Do you have an open source security policy in place for open source development or usage? (source: Snyk).
[Click on image for larger view.] Do you have an open source security policy in place for open source development or usage? (source: Snyk).
- Three in 10 (30 percent) of organizations without an open source security policy openly recognize that no one on their team is currently directly addressing open source security
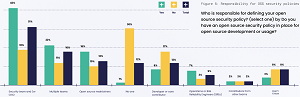 [Click on image for larger view.]Who drives OSS security policies? (source: Snyk).
[Click on image for larger view.]Who drives OSS security policies? (source: Snyk).
Those data points come from a survey of more than 550 respondents in the first quarter of 2022 that backed the report, which also is based on interviews and data from Snyk Open Source, a product which has scanned more than 1.3 billion open source projects. Snyk and The Linux Foundation combined to research how organizations detect, mitigate and reduce the security risks posed by open source software (OSS).
"Just as developers of proprietary code use open source packages to speed up development, so do the creators of open source," Snyk said in a June 21 blog post. "This means that open source libraries often build upon other open source libraries -- which are known as indirect or transitive dependencies -- creating a complex tree of dependencies. From a security perspective, open source software introduces many layers of code into your applications -- and vulnerabilities can live throughout those layers (as we recently saw with Log4Shell). Managing this risk requires thoughtful planning and implementation of security policies that address the potential attack surface in open source libraries. It also requires equipping your team with reliable, effective tools for fixing detected vulnerabilities, and keeping pace as new vulnerabilities emerge."
An improving OSS security scene was detailed in a March Virtualization & Cloud Review article titled "Once a Security Problem, Open Source Now a Solution, Report Says." Coming from Red Hat, that report said: "This year, 89 percent of IT leaders said enterprise open source is at least as secure as proprietary software. This is a big change from not all that long ago. It used to be that quite a few potential buyers figured that being able to see the source code inherently decreased code security in the same manner as being able to see the schematics of a physical security system."
However, the new Snyk report indicates there still might be more work to be done to improve the amount of vulnerabilities that could be surfaced in applications using OSS components. Snyk said that most estimates indicate 70-90 percent of any piece of modern software includes open source code.
"Perhaps the most important finding is that many organizations still don't fully understand the scope of potential vulnerabilities in open source packages, and don't have the policies in place to effectively protect their applications," Snyk said. "Using open source packages requires a new way of thinking about developer security that many organizations have not yet adopted."
Other data points from the report include:
- 41 percent of organizations don't have high confidence in OSS security
- The average number of outstanding, critical vulnerabilities in an application is 5.1 (range was between 2.6 and 9.5, depending upon programming language used)
- Over four out of every ten (41 percent) organizations don't have high confidence in their OSS security
- The average application development project has 49 vulnerabilities and 80 direct dependencies (open source code called by a project)
- The time it takes to fix vulnerabilities in open source projects has steadily increased, more than doubling from 49 days in 2018 to 110 days in 2021
- Over one-quarter of survey respondents noted they are concerned about the security impact of their direct dependencies
- Only 18 percent of respondents said they are confident of the controls they have in place for their transitive dependencies
- 24 of organizations are confident in the security of their direct dependencies
- 40 percent of all vulnerabilities were found in transitive dependencies
- Time to fix vulnerabilities more than doubled from 49 days in 2018 to 110 days in 2021
- 59 percent of organization report their OSS is somewhat or highly secure
"The tremendous benefits and prevalence of OSS in organizational software, combined with the vulnerability of the OSS software supply chain, puts us at a crossroads," the report said. "Organizations and companies that use open source software need to become more aware of what dependencies they are using, proactively and regularly monitoring all components for usability, trustworthiness, and vulnerabilities. Ultimately, open source software is a two-way street: consumers of open source software must contribute back to the OSS communities to ensure the health and viability of the dependencies they rely on. Merely using open source software, without contributing back, is not enough. What is required is both to 1) incorporate the nature of OSS dependencies into standard cybersecurity and development practices and 2) contribute back to the OSS communities that organizations rely on."
Specifically, Snyk made these recommendations, which are fleshed out in the report:
- Collaborate with vendors to create more intelligent security tools
- Define robust cybersecurity policies and procedures
- Implementing best practices for secure software development is the other leading way to improve OSS security
- Encourage developers to improve their security knowledge
- Use automation to reduce your attack surface and incorporate security checks into your developers' existing toolchain
- Leverage specialized security tools
- Consumers of OSS should give back to the communities that support them
About the Author
David Ramel is an editor and writer at Converge 360.