News
The Public Cloud 'Sensitive Data' Problem
Two days ago, reports emerged about a ransomware attack on a healthcare debt collector that might have exposed the records of 1.9 million patients, potentially one of the biggest data breaches of personal/health information in 2022.
On the same day, the Cloud Security Alliance (CSA) announced a new survey-based report on the storage of sensitive data in the cloud.
While the victim of the February ransomware attack reportedly managed to stop the exploit by shutting down its systems, CSA's "
Sensitive Data in the Cloud" report indicates we might well expect such attacks to continue to be trumpeted in the news headlines.
For example, one key finding of the report is that most organizations already store sensitive data in the cloud. Specifically, 89 percent of organizations surveyed host sensitive data or workloads in the cloud. Among those, 67 percent host some sensitive data in the public cloud, and 45 percent host in the private cloud.
"With such sensitive data in these cloud environments, it emphasizes the need for proper security of this data with measures like encryption," the report said.
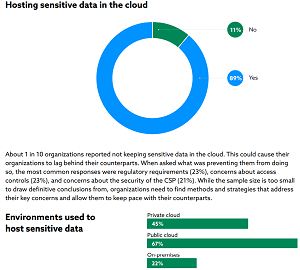 [Click on image for larger view.] Hosting Sensitive Data (source: CSA).
[Click on image for larger view.] Hosting Sensitive Data (source: CSA).
The April online survey received 452 responses from IT and security professionals from various organization sizes and locations, said the CSA, which says it's dedicated to defining and raising awareness of best practices to help ensure a secure cloud computing environment.
A second key finding identified by CSA is that even though cloud service provider (CSP) security controls are effective, many organizations still have low confidence in their ability to protect sensitive data in the cloud.
"Most organizations report that their CSP security controls are highly effective (38 percent) or somewhat effective (51 percent)," the report said. "However, organizations feel less confident in their own ability to protect sensitive data in the cloud, slightly (31 percent) or moderately (44 percent) confident. Taken together it appears organizations are not as confident in their ability to protect data even though CSPs provide effective security controls."
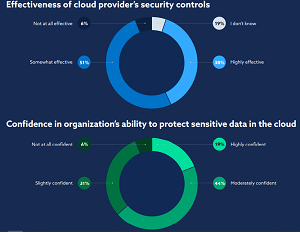 [Click on image for larger view.] Effective Tools, Low Confidence (source: CSA).
[Click on image for larger view.] Effective Tools, Low Confidence (source: CSA).
"These results could be due to CSPs' greater access to security resources such as knowledgeable staff, budget, and time," the report said. "All these resources can be dedicated to understanding and addressing the ever-evolving threatscape. But despite organizations' sense of confidence in their CSPs' security controls, they still have reservations about their ability to protect sensitive data in the cloud. Just over a third of organizations were not confident or only slightly confident about their ability to protect sensitive data in a cloud environment and another 44 percent reported they were only moderately confident. Despite this, 81 percent of organizations have sensitive data in the cloud. This makes it clear that organizations need to address the protection of the data layer in addition to utilizing their CSP's security controls."
The other two key findings of the report concern a practice called "Confidential Computing," specifically indicating that 27 percent of respondents are already using it to protect workloads, while 55 percent have plans to implement it in the next two years.
The CSA report was sponsored by Anjuna, which offers Confidential Computing software.
About the Author
David Ramel is an editor and writer at Converge 360.