News
Threat Report: Big Hike in Cloud Attacks, but 'Access Broker' Biz Skyrocketed
Cybersecurity company CrowdStrike's recent threat report paints a bleak picture, citing increased attacks across the board from cloud attacks to malware-free exploitations, but the access broker business saw the biggest uptick.
That uptick is presented in detail in the 2023 CrowdStrike Global Threat Report, the company's ninth annual such offering.
While all kinds of attacks and techniques increased from last year's edition, the access broker biz was especially notable, as the company saw a whopping 112 percent increase in dark web advertisements for the service, sometimes called initial access brokers (IABs), in which threat actors who gain access to compromised systems sell that access -- sometimes at more than $6,000 per pop -- to other criminals.
The company said that year-over-year increase (reflecting 2022 data) illustrated the value of and demand for identity and access credentials in the underground economy, while noting that more than 2,500 IAB advertisements were found across the criminal underground.
"Several brokers advertised accesses in bulk during 2022, while others continued to use the 'one-access one-auction' technique," the report said. "Access methods used by brokers have remained relatively consistent since 2021; a particularly popular tactic involves abusing compromised credentials that were acquired via information stealers or purchased in log shops on the criminal underground."
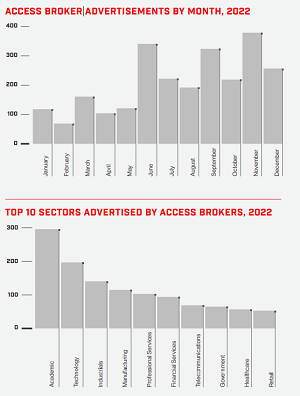 [Click on image for larger view.] Access Brokers (source: CrowdStrike).
[Click on image for larger view.] Access Brokers (source: CrowdStrike).
Furthermore, a companion CrowdStrike blog post said, "An especially popular tactic was the abuse of compromised credentials acquired via information stealers or purchased on the criminal underground, reflecting a growing interest in targeting identities that we also saw last year: Our 2022 report found 80 percent of cyberattacks leveraged identity-based techniques."
A post from February 2022 revealed that the average asking price across different sectors ran from about $1,800 (insurance sector) to more than $6,000 for the government sector.
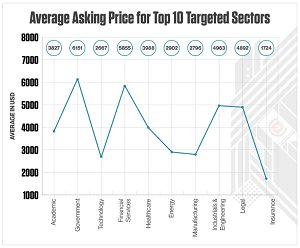 [Click on image for larger view.] Access Asking Prices (source: CrowdStrike).
[Click on image for larger view.] Access Asking Prices (source: CrowdStrike).
Beyond the access broker market, other highlights of the report as presented by CrowdStrike include:
- Cloud exploitation skyrocketed: Last year's Global Threat Report anticipated a rise in cloud exploitation, a trend that unfolded as expected in 2022. Cloud exploitation cases grew by 95 percent last year, and incidents involving cloud-conscious threat actors nearly tripled from 2021. The cloud continues to evolve as the new battleground as adversaries increasingly target cloud environments.
- Malware-free attacks continued to rise: Sophisticated adversaries relentlessly searched for new ways to evade antivirus protection and outsmart machine-only defenses. Seventy-one percent of attacks detected were malware-free, while interactive intrusions (hands-on-keyboard activity) increased 50 percent in 2022.
- Adversaries re-weaponized and re-exploited vulnerabilities: The constant disclosure of vulnerabilities affecting legacy infrastructure like Microsoft Active Directory continued to burden security teams and present an open door to attackers, while the ubiquitous Log4Shell vulnerability ushered in a new era of "vulnerability rediscovery," during which adversaries modify or reapply the same exploit to target other similarly vulnerable products.
- China-nexus adversaries scaled operations: CrowdStrike Intelligence tracks China-nexus adversaries as the most active targeted intrusion groups. China-nexus adversaries, and actors using TTPs consistent with them, were observed targeting nearly all 39 global industry sectors and 20 geographic regions we track. These intrusions are likely intended to collect strategic intelligence, compromise intellectual property and further the surveillance of targeted groups.
The report also provided five recommendations for organizations to follow to be prepared for cybersecurity attacks:
- Gain Visibility into Your Security Gaps: An organization is only secure if every asset is protected. It's impossible to protect what you don't know about. As adversaries continue to weaponize and target vulnerabilities, security teams should prioritize visibility and enforcing of IT hygiene across the entire enterprise asset inventory.
- Prioritize Identity Protection: The increase in malware-free attacks, social engineering and similar attempts to obtain access/credentials has made it clear that a traditional endpoint-only solution is not enough. Integrated identity protection with tight correlation across endpoints, identity and data is essential.
- Prioritize Cloud Protection: Stopping cloud breaches requires agentless capabilities to protect against misconfiguration, control plane and identity-based attacks, combined with runtime security that protects cloud workloads.
- Know Your Adversary: A cyberattack, by definition, is a conflict between two parties. Not knowing or understanding your adversary when you enter a battle is equal to being unprepared.
- Practice Makes Perfect: While technology is clearly critical in the fight to detect and stop intrusions, security teams are the crucial link in the chain to stop breaches.
The report further fleshes out each of those recommendations.
"The report shows that security must parallel the slope of technology innovation," said CrowdStrike CEO George Kurtz in the report. "As technology matures, security has to mature and match the innovation of the technology running our organizations. The same thing can be said for the adversary. With every innovation we achieve, we can expect the adversary to actively seek ways to exploit it. From the cloud to Kubernetes, from AI to applications and more, as technology gets more complex and provides tremendous operational gains, security must evolve to protect the productivity we gain."
About the Author
David Ramel is an editor and writer at Converge 360.