In-Depth
Being a One-Person Security Operations Center
Paul looks at new Microsoft Sentinel features/improvements added over the last 6-12 months and how he uses it with his SMB clients to give them monitored cybersecurity protection on a shoestring budget.
It's no secret on this site that I'm a fan of Microsoft Sentinel -- I've covered this cloud-base Security Information and Event Management (SIEM) offering here and here. In this article I'll look at new features and improvements that have been added over the last 6-12 months, and how I use Sentinel with my clients to give them monitored cybersecurity protection on a shoestring budget.
Introduction to Sentinel
Let's start with a quick primer on what Sentinel does and why it's so foundational to how I keep my clients cyber safe. A SIEM tool collects (ideally) all your logging / telemetry from your security tools. So, your Endpoint Detection and Response (EDR) solution, your email hygiene solution, your firewalls / proxies / web-based gateways along with Software-as-a-Service (SaaS) applications (think Microsoft 365 / Google Workspace / Salesforce) all feed their data into a single database.
Sentinel is a cloud-based SIEM, so instead of having to purchase large amounts of storage hardware on-premises, it uses Log Analytics in Azure, a service originally built to house IT metrics and telemetry. Log Analytics is optimized for storing vast amounts of log data and being able to search across it using the Kusto Query Language (KQL).
Once you have your data stored (you can choose retention periods for different types of data, depending on regulations and so on), Sentinel runs Analytics rules across the data and raises incidents if something suspicious matches the logic of the rule. There are also Workbooks to visualize large amounts of data points to understand what's normal for example. Playbooks provide the other half of Sentinel -- Security, Orchestration, Automation and Response (SOAR) capabilities -- built on Logic Apps in Azure, a user account could be automatically disabled if a rule shows that their account is compromised for example. Hunting allows you to retroactively look through stored data to see if a newly discovered type of attack was used against your organization in the recent past.
Notebooks builds on Jupyter notebooks to assist in investigations with code, visualization, and text in one place to analyze data. User Entity Behavior Analytics (UEBA) looks at user / device accounts normal behavior and alerts on anomalous actions. Sentinel is expandable with Solutions which can contain data connectors, analytics rules, workbooks, hunting queries and playbooks in a central location, the Content hub. These solutions are provided by Microsoft, third parties and the community.
 [Click on image for larger view.] Content Hub in Sentinel
[Click on image for larger view.] Content Hub in Sentinel
For my clients, they're either on Microsoft 365 Enterprise E5 (or A5 Security) or Business Premium. This unlocks Microsoft's integrated eXtended Detection and Response (EDR) services, collectively called Microsoft 365 Defender, which includes Defender for Office (email hygiene), Defender for Identity (Active Directory and AD Federation Services), Defender for Endpoint (EDR) and Defender for Cloud Apps (CASB). All that telemetry feeds directly into each clients Sentinel instance. Once you enable the connector, this is a bi-directional flow, so if you investigate and close an incident in Sentinel, it's closed in Microsoft 365 Defender, and vice versa.
An Interesting Email
As mentioned, I'm the Security Operations Center (SOC) for my clients, and I'm busy with ordinary IT support, or writing articles such as this one during the day, so I don't have time to watch the Sentinel console. Hence, I've set up a Playbook to notify me of suspicious activity via email.
 [Click on image for larger view.] Playbook for incident notification via email
[Click on image for larger view.] Playbook for incident notification via email
A little over a week ago as I'm writing this, I received this interesting email from this automated system:
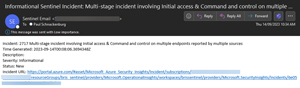 [Click on image for larger view.] Email notification for multi-stage attack on multiple devices
[Click on image for larger view.] Email notification for multi-stage attack on multiple devices
Notice that there's a bit of information in the email as to the nature of the incident, helping me with initial triage, as well as a link to take me directly to the incident in the Sentinel portal. As you can probably guess, I quickly followed this one up as it seemed serious.
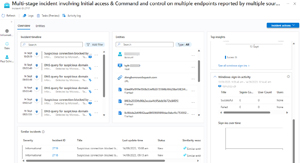 [Click on image for larger view.] Incident Overview page
[Click on image for larger view.] Incident Overview page
This is the new incident Overview page, created with a lot of input from the community, which now gives (almost) all the relevant information on one page, minimizing the need to jump around to different areas of Sentinel. On the left I can see the timeline (a feature I love in both Sentinel and M365 Defender), which has aggregated related individual alerts so I can quickly see what happened. At 08:57 a.m. (this is a student's Windows 11 laptop at a small, independent school) three DNS queries for suspicious domains were issued, followed by a suspicious connection five minutes later. This was blocked by network protection (a part of Defender for Endpoint), and nearly an hour later, the same DNS queries were issued, this time on a different PC. Clicking on any of the entries in the timeline brings up the details such as which entities were involved, the product that raised the alert, which MITRE ATT&CK technique it maps to and so on.
The middle pane shows all the entities involved, user and computer accounts, URLs, file hashes and initiating process (Chrome.exe in this case). For additional context, other similar incidents are shown underneath, while the Top insights pane on the right shows related activity -- in this case sign-ins in the 24 hours leading up to the incident.
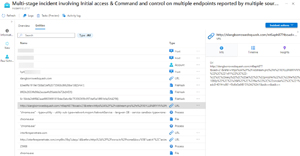 [Click on image for larger view.] Incident Entities page
[Click on image for larger view.] Incident Entities page
The second "tab" shows all of the Entities and lets me quickly get all relevant details for each of them.
With all this information immediately available, I quickly determined that the malicious activity was blocked, and all that was required was following up with the teacher for this student as to how the malicious links were clicked in the first place (didn't get a good answer, unfortunately).
Here's an example of a custom analytics rule (based on this blog post) to catch MFA fatigue attacks -- which is when an attacker generates so many MFA prompts for a user that in the end they click Approve just to make it stop (sometimes enhanced by a legitimate sounding phone call from the "IT Helpdesk"). In this case I quickly checked with the user in question and determined that it was benign.
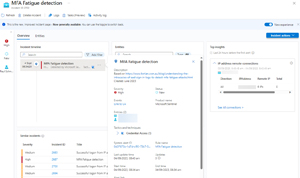 [Click on image for larger view.] MFA Fatigue Incident overview
[Click on image for larger view.] MFA Fatigue Incident overview
I'll anticipate a question here -- have any of my clients been breached since Sentinel and Microsoft 365 Defender have been in place? The answer is no, we've had some near misses with malware-laden files, and the usual brute-force password attacks, and of course phishing emails, but so far nothing leading to compromise.
We did have a successful Business Email Compromise (BEC) attack last year, where an email purporting to come from a teacher (it was a Gmail account, not her work account) asked for a bank account change for salary payments. It would have been nice if this had been caught by Defender for Office 365, but I see this more as a failure of process -- the lady in the accounts department should have known / been trained to always follow up via phone with any bank account change notification (she was a new hire). This drives home the fact that cybersecurity is not just a technology problem, it can only be solved by people and process working hand in hand with technology.
New Features in Sentinel
This is a very popular product from Microsoft, and as such receives a lot of attention and development, leading to rapid improvements in several areas. Here are some of my personal highlights from the last 6-12 months.
Incident tasks is an easy way to attach a "To Do list" to incidents, which would be very handy in a large environment with many analysts, although I haven't seen a use for it myself yet. Audit and health monitoring, currently in preview, adds two new tables to Sentinel and lets you track the health of your Analytic rules, Data connectors (both are very important), Automation rules and Playbooks.
Ingestion time transformation of incoming log data, also in preview, using Data Collection Rules (DCR) seems very interesting, again not something I think will apply to my SMB clients. The new Sentinel Optimization workbook, however, is a real gem that I'm using in all my client's tenants. This has three pages, the first one visualizes ingested data, which tables receives the most data, monthly cost, data ingested under the E5 benefits and much more.
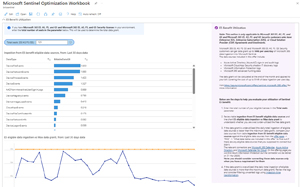 [Click on image for larger view.] Optimization Workbook E5 benefit
[Click on image for larger view.] Optimization Workbook E5 benefit
The second page tracks average and mean time to acknowledge, to resolve incidents, with or without automation and much more. The last page shows data about retention periods, playbooks, workbooks and so on.
Sentinel, and Log Analytics overall, are migrating from the legacy Microsoft Monitoring Agent (MMA) to the newer Azure Monitoring Agent (AMA), which runs on both Windows and Linux. This brings the flexibility of DCRs, but also the need to create them, and the (newish) Data Collection Rule Toolkit workbook assists with this. I have yet to migrate the on-premises VMs and hosts at one client to the AMA agent, but I'll need to create DCRs for those when the time comes.
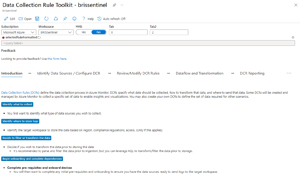 [Click on image for larger view.] Data Collection Rule Toolkit
[Click on image for larger view.] Data Collection Rule Toolkit
For each analytic rule, you can see insights into any failed executions and health issues, as well as a tally of the runs the rule has had in the last seven days. An exciting new feature is Hunts, which lets you create hunts based on a hypothesis, add queries, add bookmarks for interesting findings and if required, create an incident if malicious activity is found.
By far the biggest improvement recently for me in Sentinel is the connector to Microsoft Defender Threat Intelligence (MDTI) for correlating alerts with TI data. The premium license of MDTI is (way) out of my budget, but the free community version provides invaluable data through the new connector.
The new Solution for SAP is never going to be used with any of my clients, and I don't have clients with Power Platform usage yet, however the Purview Information Protection connector should prove useful as my financial services client starts using DLP and Information Protection.
There's a new set of "essential" solutions for DNS, Network Sessions, Security Threat, SOAR and UEBA. While I've only experimented with the DNS and Network Sessions Solutions so far, they all look useful. They're based on the Advanced Security Information Model (ASIM) approach of normalizing data coming from different data connectors.
The ability to have a central workspace, with "child" workspaces for easy duplication of content, is interesting but not something I see myself deploying (my clients' workspaces are in their own Azure subscriptions), and the ability to manage log tiering and storing some data in basic logs (which can be queried, but you can't run analytics rules against it) is on my list to explore.
The simplified pricing tier combines the cost of data ingestion into Log Analytics with the analysis cost of Sentinel (these are separate charges in workspaces created before July 2023), but I don't expect noticeable changes in the monthly cost (one of my clients pays about $75 per month for their Sentinel tenant, whereas another smaller client pays less than $5 per month).
The final improvement to mention is the centralization of all content types into Content hub -- previously you had to look through workbook templates in Workbooks, Analytics rule templates in Analytics and so forth. With many Solutions now combining different content artifacts into a single package, having them all in Content hub makes a lot of sense.
Conclusion
Sentinel has matured into a very capable SIEM and SOAR solution, and I'm pleased with the visibility and flexibility it provides me for protecting my clients. If you'd like to try it out, you can get started with a free account.