News
New Cloud Cybersecurity Worry: 'Alert Fatigue'
As if you didn't have enough to fret about from rampant ransomware and other cybersecurity threats, Orca Security has published a new survey-based report on a new worry: "alert fatigue."
Focusing on the cloud, the report examines a problem that can not only cause obvious security problems like missed alerts, but which can also overburden security teams, leading to staff turnover, internal team friction and other issues.
"Alert fatigue happens when security professionals are exposed to a large number of often meaningless, unprioritized security alerts and consequently become overwhelmed," Orca said in a March 15 blog post announcing the report. "Alert fatigue is a common problem in IT security and is no different in public cloud security.
"Like the story of 'The Boy Who Cried Wolf,' if the amount of meaningless and false positive alerts becomes too great, responders become desensitized, resulting in alerts that actually do deserve attention, getting missed."
The "2022 Cloud Security Alert Fatigue Report," reportedly an industry first, indicates burned-out security teams are overburdened by alerts numbering 500 or more per day, with the problem exacerbated by siloed security tools and other factors that result in inaccurate or unnecessary alerts. Those issues result in problems like misdirected remediation and wasted work, missed security issues, employee turnover and internal friction among staffers.
That latter problem, team friction, can result from the typical shared responsibility model where security, IT and DevOps teams are stakeholders.
Some 60 percent of respondents said that alert fatigue has created friction between their DevOps and security teams, with the following graphic indicating slight differences in the numbers when broken down by industry and geography. So apparently there's more bickering among the French and in tech companies.
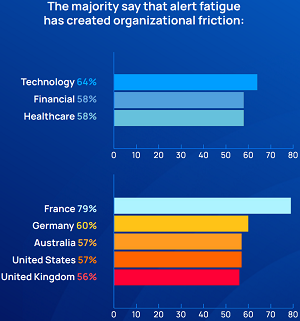 [Click on image for larger view.] Alert Fatigue Is Leading to Internal Friction (source: Orca Security).
[Click on image for larger view.] Alert Fatigue Is Leading to Internal Friction (source: Orca Security).
"Security professionals are all too familiar with alert fatigue," the report said. "They faced it in the on-prem world, and now they're dealing with it in the cloud. Organizations use many different security tools that each generate alerts, overwhelming security teams who have to spend hours each day reviewing alerts to determine which issues need to be fixed first."
Some data highlights of the report as presented by Orca include:
-
Security teams are inundated with cloud security alerts: 59 percent of respondents receive more than 500 public cloud security alerts per day.
Critical alerts are being missed: 55 percent of respondents said that critical alerts are being missed, often on a weekly and even daily basis.
Alert fatigue causes turnover and internal friction: 62 percent of respondents say that alert fatigue has contributed to turnover, and 60 percent of respondents said that alert fatigue has created internal friction in their organization.
-
Siloed security tools exacerbating the problem: The vast majority of respondents use three or more public cloud security tools (87 percent), with 57 percent using 5 or more tools. The types of tools most used are network scanning tools (84 percent), followed closely by cloud platform native security tools (82 percent).
 [Click on image for larger view.] Too Many Tools (source: Orca Security).
[Click on image for larger view.] Too Many Tools (source: Orca Security).
- Security teams receive many falsely flagged issues: As many as 81 percent of respondents say that more than 20 percent of alerts are false positives. A little less than half (43 percent) said that more than 40 percent of their alerts are false positives. Regardless, teams must address each alert as if it's a true positive until they know otherwise. This leads to wasted time and contributes to desensitization.
- Remediation burden falls on security teams: In addition to deciding which alerts need to be prioritized, security teams bear the greatest responsibility for triaging and remediating alerts, with 82 percent of respondents listing the IT security team, and 31 percent listing SecOps as the group responsible for remediating alerts. Software development seems to be called upon the least often, with only 20 percent of respondents naming development as responsible for remediation.
- Security teams are getting burned out: With the sheer number of alerts, with many false positives and low priority alerts and only a small number of alerts that actually need attention, teams are getting demoralized, overworked, and burned out. 62 percent of respondents say that alert fatigue has contributed to turnover at their organization. No matter which country or industry, the majority of respondents all say that alert fatigue has led to staff leaving their positions.
- Critical alerts are being missed: Due to the sheer number of unprioritized alerts, security practitioners are becoming desensitized with the result that alerts that actually do need immediate attention are being missed with possibly disastrous consequences.
Key recommendations, meanwhile, include:
- Tool consolidation: Instead of adding more siloed tools, consolidate tools in fewer platforms to avoid duplicated alerts and improve risk prioritization by leveraging centralized contextual information to discover dangerous risk combinations.
- Demand more from your security tools: Ask security vendors how they prioritize risk. Ensure that they combine numerous factors such as severity, ease of exploitation, accessibility and potential business impact.
- Protect the target instead of the entry point: Make sure you know where your most critical assets are, and find out if your security vendor automatically prioritizes risks based on potential exposure of these assets.
- Focus on attack paths: Security teams need to shift from investigating siloed alerts to investigating and prioritizing attack chains to get quicker insight into which issues need to be fixed first. Strategic remediation: Instead of trying to fix all alerts in the attack chain, start by fixing the one that breaks the chain to stem the most immediate danger.
The report is based on a survey of more than 800 IT security professionals in five countries (US, UK, France, Germany and Australia) and across 10 industries (including financial services, healthcare and technology) who are deploying applications on Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), Oracle Cloud, Alibaba Cloud, IBM Cloud and other public cloud providers.
About the Author
David Ramel is an editor and writer at Converge 360.