How-To
Microsoft Defender for Business: 'The Arsonist Is Also the Fire Department'
Microsoft is no longer primarily relying on ISV partners to innovate and provide security solutions. Here's an overview of enhanced Defender offerings.
Something interesting is happening on the security front in IT when it comes to Microsoft. For many years they were content to provide a basic anti-malware solution in Windows Defender and leave the security space open to ISV partners to innovate and provide solutions.
That's no longer true as a concerted effort over the last 3-5 years has completely changed this situation. Microsoft has a powerful Cloud App Security Broker (CASB), Defender for Cloud Apps -- think SaaS based firewall in the cloud, that by some accounts has the largest market share of all -- plus a cloud-based Security Information and Events Management (SIEM) and Microsoft Sentinel, which is showing good growth despite being only two years old. Microsoft also now offers a full-fledged Endpoint Detection and Response (EDR) tool, with built-in Threat and Vulnerability Management (TVM) for Windows, macOS, Linux, iOS and Android in the form of Defender for Endpoint P1 and P2. The former is part of Microsoft 365 E3 licensing and has some serious limitations, while the latter comes in Microsoft 365 E5 and has all the bells and whistles.
We've looked at these solutions in depth here at Virtualization & Cloud Review. Defender for Cloud Apps is covered here, Microsoft Sentinel here and Microsoft 365 Defender here.
Building on this technology stack, there's a new member of the family, Defender for Business, which is sort of Defender for Endpoint P1 ½, sitting somewhere in-between P1 and P2 in functionality, but tailored for the SMB space (up to 300 users). It's the focus of this article.
The Arsonist Is Also the Fire Department
This is an expression I heard on a recent podcast, referring to Microsoft selling (expensive) security tools to protect their underlying platforms and sometimes mitigate flaws that some might argue shouldn't have been there in the first place. It's a difficult balance, and I totally understand security architects who decide that using non-Microsoft tools to provide protection is a better approach, making sure that the platform responsibility is separate to the security of those same platforms. My only recommendation would be to ensure that whatever tools you pick for endpoint protection, threat and vulnerability management, email and collaboration platform hygiene, data protection, cloud assessment and protection and SIEM all integrate without too much work. Because that's the issue: for enterprises, Microsoft's suite of tools is very easy to integrate, sometimes only requiring a single click to be connected.
Disparate, siloed security tools that don't give your defenders a complete picture of an attack and require manual work to correlate alerts in separate systems are a hindrance to timely defense.
But in the SMB space -- where there are no security architects and very little concern about separating platforms and defense tools, and the pragmatic need to just have something that "works" and keeps the business safe is paramount -- is where the new Defender for Business will likely find success.
Most SMBs rely on an outsourced Managed Service Provider (MSP) to take care of their IT needs, and rarely, also on a Managed Security Service Provider (MSSP). In the case of the normal MSP, sometimes they use a modern and capable EDR tool for all endpoint platforms, but more often than not, a simpler anti-malware solution is used. In today's threat landscape this just isn't good enough because there's no way to manage modern malware with signature-based approaches. Your endpoint protection must identify abnormally behaving software using machine learning, both on the endpoint and where necessary ("not sure if this is malicious") further in the cloud, something that Defender for Business offers.
Defender for Business
As mentioned, Defender for Business is available for Windows, macOS, iOS and Android. Missing from that list compared to its bigger brother P2 is Linux, which is fine for most SMBs as they rarely have a lot of Linux deployed. A more challenging issue is that Windows Server is also not supported, which is something Microsoft is aware of -- hopefully there will be a solution soon.
Onboarding can be done through the Microsoft 365 Defender Portal or using Microsoft Endpoint Manager, with a special simplified configuration experience on offer in the former.
This step-by-step wizard takes you through assigning Security reader or Security admin permissions to user's who should have access to the data from Defender for Business and who should receive alert emails for intrusions and/or identified vulnerabilities.
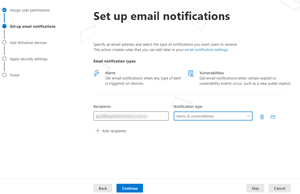 [Click on image for larger view.] Email Notifications Configuration
[Click on image for larger view.] Email Notifications Configuration
Next you add Windows devices, either through Endpoint Manager, with the easy option of adding all devices enrolled in Endpoint Manager (and any future devices), or specific devices, which in my tenant there were 10 that were only registered in Azure Active Directory, and one Intune enrolled.
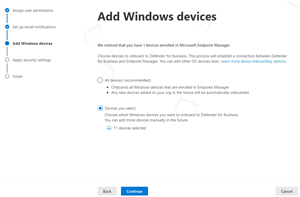 [Click on image for larger view.] Adding Windows Devices to MDB
[Click on image for larger view.] Adding Windows Devices to MDB
The next screen lets you choose between managing endpoint settings through the Microsoft 365 Defender portal or use Endpoint Manager.
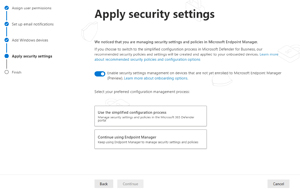 [Click on image for larger view.] Use M365 Defender or Endpoint Manager for Settings
[Click on image for larger view.] Use M365 Defender or Endpoint Manager for Settings
Onboarding with the wizard is easy, compared to the setup in P1/P2. There are further steps to onboard macOS, iOS and Android devices. Here you can see the local script download option for macOS, but you can also use Intune to deploy to Macs at scale.
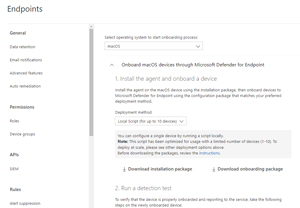 [Click on image for larger view.] Onboarding macOS Devices
[Click on image for larger view.] Onboarding macOS Devices
On macOS and Windows, Defender for Business brings complete endpoint protection, recording everything that happens on the device for forensics purposes (EDR), and blocking known and new malware using local and cloud-based machine learning. This is called Automated Investigation and Response (AIR), which in P1/P2 are optional. You can choose the level of automation as you likely have SOC analysts watching queues, investigating and responding to alerts as they arise. In SMBs however, it's unlikely that you have 24x7 monitoring, so automated remediation and isolation of infected devices automatically are crucial and thus enabled by default in Defender for Business.
Furthermore, you can block categories of web sites (this works for all browsers on the endpoint), handy in today's world where many users aren't working in the corporate office, behind the expensive web filtering firewall.
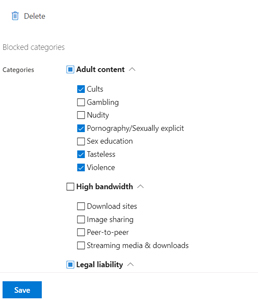 [Click on image for larger view.] Web Content Filtering Policy Configuration
[Click on image for larger view.] Web Content Filtering Policy Configuration
Apart from EDR and AIR, the power of Threat and Vulnerability Management is a huge selling point of Defender for Business, identifying all installed software that has known vulnerabilities and giving you a prioritized list across all devices of what to upgrade first.
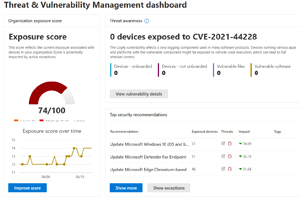 [Click on image for larger view.] Threat and Vulnerability Management Dashboard
[Click on image for larger view.] Threat and Vulnerability Management Dashboard
One thing I've always liked about Defender for Endpoint is the tutorial selection, getting your techs up to speed with how it works and how to manage incidents.
 [Click on image for larger view.] Defender for Endpoint Tutorials
[Click on image for larger view.] Defender for Endpoint Tutorials
Here I noticed another difference between P2 and Defender for Business: The former doesn't just have Tutorials, it also comes with Evaluation labs where you can (at no extra cost, with monthly limitations on number of VMs and hours they run) spin up client and server OS VMs to test the different attacks in a sandbox.
Note that Defender for Business has per-user licensing, covering up to five devices per user, so a user's iPad, Android phone and Windows laptop for example are included.
Compared to Defender for Endpoint P2, you miss out on six months' worth of stored data and the ability to do Threat Hunting over that data -- something that most SMBs won't have the staff for anyway. There's also no Threat Experts, a pair of services. In the first, Microsoft will notify you when it sees an intrusion into your network, based on the collected telemetry from the endpoints. In the second (paid for and you must apply to it and then be accepted), SOC analysts from Microsoft will help your staff during times of extra load. Neither of these are available for SMBs.
Conclusion
While I think Defender for Business is going to be a hit in SMBs, it's not all roses. For example, today you can't mix licensing in a tenant with P1/P2 and Defender for Business. This will come in the future, but if you have a tenant today on P2 and you're switching to Defender for Business, make sure you un-assign all the P2 licenses first and then assign the new licenses. Note that you don't need to offboard and re-onboard clients.
The inclusion of Defender for Business into M365 Business Premium makes this a no-brainer in my mind. Any business with less than 300 users who are using M365 should make sure all users are covered by Business Premium and have Defender for Business deployed, along with all the other great security features that are now included in this plan.
If you're not using Microsoft 365, there will be a stand-alone version of Defender for Business available later in the year.
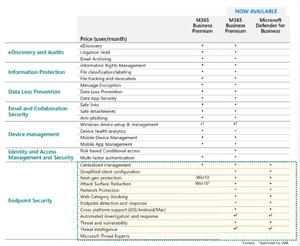 [Click on image for larger view.] Security features in M365 Business Premium (source: Microsoft).
[Click on image for larger view.] Security features in M365 Business Premium (source: Microsoft).