In-Depth
Microsoft Security Exposure Management, Why You Should Care
At the recent Microsoft Secure event a new tool was released in public preview into the company's stable of security tools, called Exposure Management.
I've enjoyed access to the private preview for some months -- in this article I'll outline what it does, why you should care and raise some still unanswered questions. I'll also look at the overall landscape of Vulnerability Management, exposure tools and the uphill battle we're all fighting to manage an ever-expanding attack surface in our organizations.
You Think You've Got a Long To Do List?
I manage the IT infrastructure and cyber security of a small handful of clients in my MSP, and the challenge of Vulnerability Management (VM, not to be confused with "Virtual Machine") is salient for me. Here's a single client, with about 125 endpoints and a list of 134 recommendations for me to attend to:
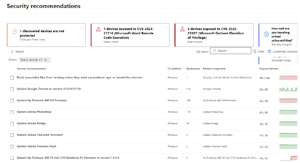 [Click on image for larger view.] Defender Vulnerability Management Recommendations List
[Click on image for larger view.] Defender Vulnerability Management Recommendations List
Note the number of exposed devices, remediating all of these would take me many, many hours, and the disheartening fact is that even if I did (and the client was happy to pay), this would only last for a very short time. New vulnerabilities in applications and platforms would appear, and the cycle would start over again. To be clear, there are automation tools that can do some of this, but they don't come with SMB friendly pricing. There's even an expression for this, "posture fatigue," a riff on the well-known alert fatigue cause of burnout for SOC analysts.
There are many different studies that show x number of vulnerabilities aren't patched with 30 days, for example, or the average time for patching ranging in months, not days. This is why -- it's an overwhelming problem, whether you're a one-man band like me or a large team servicing an enterprise. And attackers are turning revealed flaws into weaponized attacks much faster than in the past, sometimes in hours, mostly within days, and we just don't patch fast enough.
The limitations of traditional vulnerability management are also starting to show, as it often doesn't consider business context. The vulnerability (CVE) with the highest CVSS score is listed first, perhaps ranked based on how many endpoints have the flaw. But this doesn't include risks in custom code, data access misconfiguration, network vulnerabilities, resource misconfiguration and over-authorized identities, nor does it involve the business impact of different applications and data stores. And many larger businesses have several tools for tracking exposure and vulnerabilities for different parts of their infrastructure, all of which have different scoring and prioritization systems, all leading to overhead.
As you might have guessed, the buzzword factory known as Gartner has a term for the solution -- called Continuous Threat Exposure Management (CTEM).
The root cause of this problem is crap subpar software. The fact that small and large software vendors can sell software and services with such low quality is an indictment of our entire industry and would be completely unacceptable in most other fields. "Oh, the brakes on your new car didn't work -- tough luck." However, this is the reality we live in today, so as blue teams, what can we do to keep our heads above water? Read on to find out.
Microsoft's Vulnerability Management Journey
It all started with Secure Score -- I first wrote a four part series on it back in 2017, nearly seven years ago. This has since cropped up in other tools (there's Identity Secure Score, and there's one in Defender for Cloud in Azure and so on), all with the same idea: give you a list of recommended security configurations and hardening steps to improve your overall security posture, prioritized by overall impact, with points attached to each, to encourage admins to "catch them all."
Some years later Microsoft started investing heavily in Defender Vulnerability Management (MDVM) which now covers OS flaws, application issues, hardware and firmware vulnerabilities, security baselines, digital certificate security and expiry, browser extensions (at least if you pay for the VM add-on, on top of the M365 E5 license you've already sold your grandmother for). MDVM also extends to container registries in Azure, AWS and GCP, as well as running container instances.
In 2021 the company acquired Risk IQ, which led to the product now known as Defender External Attack Surface Management (EASM), which I covered here. This looks at your organization from the outside only, just as an attacker would initially. Hosts, IP addresses and web sites on the public internet are discovered, WHOIS info gathered and OWASP Top 10 vulnerabilities listed for web sites.
Defender for Cloud followed up with Cloud Security Posture Management (CSPM) capabilities, now split into a foundational core that's free, and the paid-for CSPM plan that adds advanced features such as agentless scanning, data aware security posture ("patch this VM first because it's database contains PII") and more.
Source code and "shift-left" is covered by GitHub Advanced Security (GHAS) and DevOps Security, part of the CSPM plan above.
As you can appreciate, there is information spread across these different tools for you to gain an understanding of your overall exposure and lists of recommendations to remediate the flaws. But there's no single tool to bring them all together, which is what Exposure Management is aiming to do, just like eXtended Detection and Response (XDR) has done in Defender.
Meet Security Exposure Management
The public preview is now available with no sign-up process and it has shown up in the Defender XDR portal for other clients of mine that weren't part of the private preview.
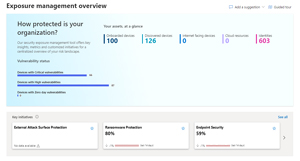 [Click on image for larger view.] Exposure Management Overview Dashboard
[Click on image for larger view.] Exposure Management Overview Dashboard
The simplest way to explain Exposure Management is that it gathers the data and recommendations from all the tools mentioned above and brings them to a single place. Anything related to cyber security that happens before an incident (called "left of boom"), is visible here. It brings in data from:
This isn't limited to only Microsoft's data sources. There's been talk of bringing in information from Qualys, Wiz, Okta, Rapid7, Tenable and Service Now's CMDB. In the current preview the Data connectors page doesn't have any of these yet, but you can join early previews to test them out as they're being developed.
But this isn't just a compiled list of recommendations. It brings several features to help businesses both small and large manage their vulnerabilities and exposure overall. The overview page has widgets with summaries of initiatives, metrics, the Attack surface map, the score of initiatives over the last few months and recent security events.
Let's look at each of these in more detail, Attack surface has Map and Attack paths. The former has an overview of your entire estate, and you can also search for individual assets. Here I'm looking at a server which is marked as critical automatically (it's a Hyper-V host), and an edge that connects it to two user accounts that log-in frequently to it, and another edge connecting it to two groups, including one marked as critical (Domain Admins).
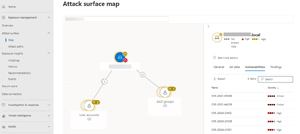 [Click on image for larger view.] Attack Surface Map
[Click on image for larger view.] Attack Surface Map
Attack paths, on the other hand, help with the critical task of understanding and remediating the potential paths attackers could use to breach the environment. Here I've clicked on one such attack path which gives me a graph of the path, in this case from a file server, through a Domain Admin account, to the Domain Admins group, to a Hyper-V host, my account (☹) and from there to the Enterprise Admins group. There are also recommendations on what steps to take to secure this path. Note that it'll identify "choke points" where a specific remediation will block several attack paths in one fell swoop, you can even group the map view by choke points.
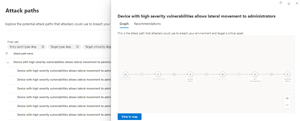 [Click on image for larger view.] Attack Paths
[Click on image for larger view.] Attack Paths
This data is also stored in tables, available in Advanced Hunting, where all the other security data from endpoints, emails and so on is stored, including edges and nodes. This allows for queries of the exposure graph and seeing the labels on edges (the connections) and node labels (CVE, device, user, group, configuration).
There are three ways an asset (user account, device/server, group) can be designated as Critical -- there are automatic inbuilt rules that will flag Domain Controllers and user accounts / groups with admin level credentials. You can also build your own queries to tag assets, based on your naming standard of servers or groups for example, and finally you can manually mark assets as critical.
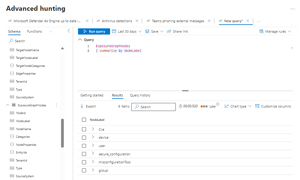 [Click on image for larger view.] Advanced Hunting with KQL over the Exposure Management Data
[Click on image for larger view.] Advanced Hunting with KQL over the Exposure Management Data
Under Exposure insights we have Initiatives, Metrics, Recommendations and Events. These are the Initiatives available:
- Business Email Compromise
- CIS M365 Foundations Benchmark (2.0.0) and (3.0.0)
- Cloud Security
- Critical Asset Protection
- Endpoint Security
- Enterprise IoT Security
- External Attack Surface Protection
- Identity Security
- Ransomware Protection
- Kerberos attacks
- On-premises credential theft
- Vulnerability Assessment
- Zero Trust (Foundational)
Each of them has an attached score (if the data source is available, this client, for example, isn't using Defender for Cloud so those initiatives are empty), and a graph showing the change over the last 14 days.
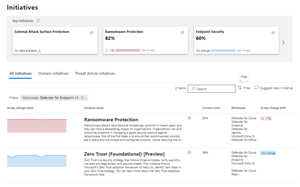 [Click on image for larger view.] Initiatives List
[Click on image for larger view.] Initiatives List
Each of these is like an action plan focused on that specific area or topic, gathering metrics from the different related workloads, and giving you a weighted score of where you're at today, along with a list of recommendations to improve your posture. Here you can see the page for Ransomware Protection, with a current score of 82 percent, along with 93 security recommendations (47 of which haven't been remediated yet), and if they're related to more than one initiative.
It's an interesting approach. If your organization is focusing on having a good posture against ransomware, for example, this gives you a prioritized list of steps to take.
Metrics gives you a list that shows the number of affected items, its weight, and how many recommendations are included in each metric, along with a handy bar that shows the balance between significant exposure and none.
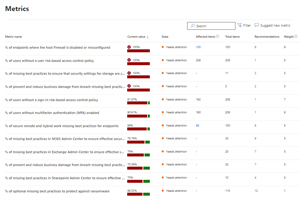 [Click on image for larger view.] Metrics List with Number of Affected Items and Recommendations
[Click on image for larger view.] Metrics List with Number of Affected Items and Recommendations
Recommendations is a list of all of them, how many related initiatives they each have and the workload that generated it, and which domain it covers.
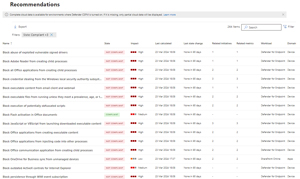 [Click on image for larger view.] Recommendations List with Workload and Domain
[Click on image for larger view.] Recommendations List with Workload and Domain
Helping you track initiative and metrics over time, Events lists significant happenings in Exposure Management in your tenant.
 [Click on image for larger view.] Events Impacting Exposure Management
[Click on image for larger view.] Events Impacting Exposure Management
The final page is Secure Score, which has now moved here (it used to live under Investigation & response in XDR). It's interesting to compare the two, Exposure Management is certainly more comprehensive -- here's a docs page listing the differences.
Conclusion
When I first heard of Exposure Management, I thought here was another tool with another long list to add to the overwhelm. After some time playing with it though, I think Microsoft is on to a winner here. The different options for slicing and dicing the data are useful, and Initiatives clearly tie the remediation steps you're taking to a specific threat class or CIS benchmark. It doesn't have the gamification, and comparison angle that Secure Score does ("how is my business security posture compared to others in my industry and my size?"), but it clearly outlines what you need to do, with the most important actions at the top of the list.
I have questions around pricing, there's been no official announcement if this will be included in M365 E5 (or E3) licensing, or if it will require yet another add-on. And the third-party angle is still unclear, for this to truly become the single tool to understand the overall security exposure of your enterprise it'll need to ingest data from the existing third-party tools on the market.
But overall, I like it and I'm going to spend the next few months drilling down on the recommendations for each of my clients and change the graphs you've seen in the screenshots here from pointing downwards over time to instead point upwards.