News
Cloud Infrastructure Misconfigurations Still Plague Industry, Security Study Affirms
Over the past several years, user misconfigurations of cloud storage infrastructure settings have led to a spate of high-profile security vulnerabilities, and a new study shows the problem persists despite heightened visibility of the problem and copious remediation guidance.
Perhaps nowhere is the misconfiguration problem more apparent than in the highly publicized string of data breaches and security vulnerabilities associated with Amazon Web Services (AWS) S3 storage buckets over the past several years, though other cloud providers have also been affected.
And, while the pace of discovered AWS vulnerabilities has seemingly slowed somewhat, S3 misconfigurations are still a problem, said DevSecOps specialist Accurics in publicizing its new report on risks and best practices.
"The recent breach attempt on Twilio was an indicator that attackers are crafting new ways to attack the cloud," Accurics said in a an August 4 blog post announcing the study results. "While a misconfigured cloud storage service (S3 bucket) was involved, this incident was not about stealing sensitive data. Instead, attackers gained access to the javascript code for their TaskRouter SDK that allows Twilio customers to integrate incoming phone call routing. Since the cloud storage service was publicly writable, attackers modified the code. Although the change was non-malicious, the severity of the risk was a stark indicator that breaches are increasing in sophistication."
The Summer 2020 edition of the State of DevSecOps report analyzed cloud native infrastructure across hundreds of deployments across Accurics customers and community users.
"The research revealed that misconfigured cloud storage services are commonplace in 93 percent of the cloud deployments analyzed, and most also had at least one network exposure where a security group was left wide open," Accurics said. "These issues have already contributed to more than 200 breaches over the past two years. However, new policy violations are starting to become commonplace such as storing hardcoded keys within environments -- 72 percent of deployments had this issue; this was a key factor in the Imperva breach in 2019."
The reports lists the top three common threats plaguing cloud deployments as:
- Hardcoded keys with high privileges -- 41 percent of respondents
- Overly permissive Identity and Access Management (IAM) policies -- 89 percent
- Misconfigured routing rules -- 100 percent
Another problem, the report said, is that cloud risk posture eventually drifts from a secure state, as almost all organizations allow users to make cloud infrastructure changes occurring in runtime. These changes, or drifts, have a high correlation between the type of drift/change and risks that create serious exposures.
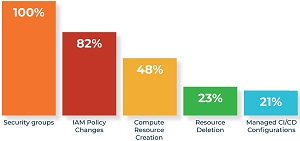 [Click on image for larger view.] Top Cloud Infrastructure Drifts (source: Accurics).
[Click on image for larger view.] Top Cloud Infrastructure Drifts (source: Accurics).
"This implies that even if organizations exercise strong security hygiene when cloud native infrastructure is initially defined, drifts in runtime will create exposures," the report said.
Key takeaways from the report as listed by Accurics include:
- The nature of cloud native infrastructure demands that security must be codified into development pipelines and enforced throughout the lifecycle
- Policy checks and breach path detection should be codified across Infrastructure as Code (IaC) to identify risks before cloud infrastructure is provisioned
- Remediation must be codified into the development pipelines in order to address the risks before cloud infrastructure is provisioned and establish a secure baseline
- Any new resources or configuration drifts in runtime from the baseline defined through IaC should be assessed for risk
About the Author
David Ramel is an editor and writer at Converge 360.