How-To
How to Secure Azure Deployments
Paul Schnackenburg examines the comprehensive guidance Microsoft offers for "how to do security" in Azure and demonstrates how to use the tool that brings it all together: Azure Security Center (ASC).
That this year has been an interesting one for us in IT is an understatement. It's been a very good year for public cloud though, with record growth in AWS and Azure. And for many businesses, the "digital transformation" journey towards the cloud has been highly accelerated. Maybe last year's small proof-of-concept Azure deployments have grown into full-scale production resources. Or the inability to access your co-lo datacenter servers due to COVID-19 restrictions has forced a migration of VMs to public cloud.
Whatever the reason, you may find yourself responsible for a lot more cloud Infrastructure-as-a-Service (IaaS) and Platform-as-a-Service (PaaS) resources and now taking stock of the security posture of all of it.
This article will look at the comprehensive guidance Microsoft offers for "how to do security" in Azure and how to use the tool that brings it all together: Azure Security Center (ASC).
Cloud Adoption Framework
The CAF is a good place to start, at any stage in your cloud journey, particularly for larger businesses. Based on cloud adoption best practices from Microsoft, partners and customers, it has guidance and tools to shape technology, people and processes for cloud success. It covers strategy and planning, migration, governing, management, organization and innovation. Here we're going to focus on the security strategy, part which covers conceptS such as securing your cloud resources as well as using cloud technology to transform how you do security, along with the shared responsibility model.
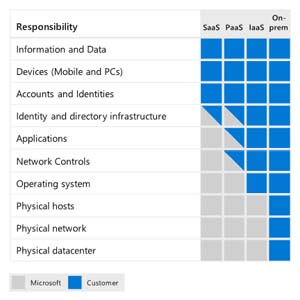 [Click on image for larger view.] Shared Responsibility Model (source: Microsoft).
[Click on image for larger view.] Shared Responsibility Model (source: Microsoft).
Moving to the cloud means that some parts of security (physical hosts/network/datacenters) are now the responsibility of the provider, whereas other parts stay with you (data, endpoint devices, accounts and identities). Further, with IaaS you still have to secure the OS and applications in your VMs, apply network controls and manage your identity directory (Azure Active Directory -- AAD). Using PaaS services shifts some of these responsibilities to the cloud provider, depending on the service you're using. This is one reason that you should look to modernize your applications away from IaaS towards PaaS as there's less for you to secure, but new features to understand to ensure a good security resilience.
The CAF also covers different admin security roles involved in managing cyberrisk and how they change when you're in the cloud. More direct guidance is also on offer through a set of recommendations and a reference implementation.
 [Click on image for larger view.] Well-Architected Security Assessment
[Click on image for larger view.] Well-Architected Security Assessment
The Well-Architected Framework, on the other hand, is a set of assessments building on these five pillars:
- Cost Optimization
- Operational Excellence
- Performance Efficiency
-
Reliability
- Security
The assessments ascertain where you're at today, and then spits out a set of curated guidance to improve your approach.
Azure Security Benchmark
The Azure Security Benchmark (ASB) builds on the Center for Internet Security (CIS) controls to manage security settings for: Network, Identity, Privileged Access, Data Protection, Asset Management, Logging and Threat Detection, Incident Response, Posture and Vulnerability Management, Endpoint Security, Backup and Recovery and Governance and Strategy.
If you haven't heard of CIS, it's a not-for-profit that provide security benchmarks for Linux, Windows, Cisco, Docker and many, many other platforms, for free. Microsoft has worked closely with the organization to nail down the CIS 1.1.0 benchmark that surfaces in Azure.
Each of the links above leads to the individual list of controls that you should implement. Take Backup and Recovery as an example. It has four tasks to complete. BR-1 is about ensuring regular, automated backups, and BR-2 stipulates encrypting the backed-up data. BR-3 covers validating all backups including the use of your customer managed keys to do so. After all, you don't want just backup; you need successful restores, and making sure it all works as expected is vital, including the decryption part. BR-4 talks about recovering lost or accidentally deleted keys using soft delete in Azure Key Vault.
Reading through the ASB (it's short and concise) will give you a thorough understanding of why each security control is important and what to do, but if that was all you had, it would still be a big project to inventory all your Azure resources and then ensure that every control was enabled for each applicable resource. Fortunately, you don't have to do any of that -- Azure Security Center will do all the heavy lifting for you.
Azure Security Center
When ASC first came on the scene, I wasn't impressed. It seemed limited in scope and of questionable value. If that's your idea of ASC, it's time to revisit it -- it has grown up a lot and is now indispensable in any Azure deployment I do for my clients.
Building on the CIS/ASB, it gives you an at-a-glance insight into your overall Cloud Security Posture (CSP -- we definitely need another acronym in IT), not only for Azure but also for AWS and GCP. This latter feature is in preview and connects ASC to your AWS and/or GCP accounts as well as the AWS Security Hub/GCP Security Command, so you'll get their respective security recommendations together with the ASC ones. It also uses Azure Arc on each deployed IaaS resource.
For Azure, ASC relies on a default policy to audit current settings across your PaaS and IaaS resources. Examples include making sure Azure Backup is enabled for VMs, that the latest version of Python is used in your Function App, or that Private endpoints are enabled for your MySQL servers.
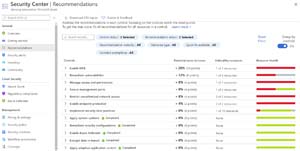 [Click on image for larger view.] Secure Score Recommendations in ASC
[Click on image for larger view.] Secure Score Recommendations in ASC
Further, on the Recommendations blade is Secure Score, an engine that identifies what controls you have already enabled (increasing your score for those) and which ones you haven't enabled yet. It then rank those in order of biggest score improvement/security posture enhancement. This last point is crucial: non-IT Pros tend to think that if we just come up with a technical solution to a vulnerability, the problem is solved. Not so. What's needed is a way for time-poor administrators with broad skills -- but not necessarily deep technical skills on the nuance, for example -- of enabling managed identity in a function app (one of the audits in the default security policy), to gain visibility and an easy way to remediate the issue.
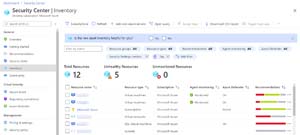 [Click on image for larger view.] Inventory Blade in ASC
[Click on image for larger view.] Inventory Blade in ASC
The Inventory blade that shows all the resources that are deployed (you need to know what you have to be able to protect it) and security alerts are raised for resources if there are anomalies.
You can also customize this using the Workflow automation blade to compose Logic Apps in Azure to automatically remediate issues. Furthermore, you can connect ASC alerts and recommendations to the SIEM used by your security team (Sentinel, Splunk Enterprise & Cloud, QRadar, ServiceNow, ArcSight, PowerBI or Palo Alto Networks).
 [Click on image for larger view.] Regulatory Compliance Blade in ASC
[Click on image for larger view.] Regulatory Compliance Blade in ASC
The Regulatory compliance blade shows you your current compliance and missing actions with several different regulations: PCI DSS 3.2.1, ISO 27001, SOC TSP and Azure CIS 1.1.0.
Until recently there were two flavors of ASC, the free tier (it gives you recommendations but you're missing out on many other useful features) and the Standard tier (pricing). This tier is now called Azure Defender.
Best Practices for Azure Security
While there's good guidance from Microsoft aviailable, here are some tips for Azure security based on my experience. Start by changing how your IT and security team thinks of cyberrisk. Bringing your on-premises mindset to the cloud will cause friction. Thoroughly understand how Zero Trust applies, both to SaaS services your business uses as well as your Azure workloads.
Start with identity and ensure that all your Azure administrators are using MFA (it's free). Improve on their "prompt on a phone app" MFA experience with Windows Hello for Business and consider using FIDO2 hardware tokens for the ultimate in "un-phishable" credentials (I'm fond of the Yubico series). Invest in Privileged Access Workstations (PAWs), sometimes known as Secured Access Workstations (SAWs), for your IT administrators. Implement Privileged Identity Management (PIM) for access to Azure resources as an additional layer of protection (requires Azure AD Premium P2 licensing).
When administering your cloud VMs, don't leave the Windows RDP or Linux SSH ports open to the internet. Use Just in Time (JIT) access, or better yet, use Azure Bastion. In preparation for the inevitable breach ("assume breach" is part of the zero-trust approach) use micro segmentation in your network to minimize the blast radius. And to prepare for a coming ransomware attack, ensure that each workload is backed up using Azure Backup and that business-critical workloads are replicated to a secondary region to protect against an entire region outage.
Conclusion
Sometimes when I talk to fellow IT pros, they seem to think that once you've migrated to the cloud, security is all taken care of by the provider. This is NOT true and thinking that it is will eventually create a RGE ("Resume Generating Event") as you look for a new job. However, Microsoft has excellent written guidance and a comprehensive tool in ASC to improve your security posture. Take advantage of them.