News
Despite 'Perceived Risk,' Edge Deployments Mature: AT&T Report
AT&T published a report on Securing the Edge, finding that despite perceived risks, enterprise edge deployments have momentum and are at a surprisingly high level of maturity.
It's part of the company's 11th annual AT&T Cybersecurity Insights report series, seeking to understand how enterprises and organizations globally are architecting and securing edge initiatives.
So, first things first, the company described what the ambiguous term "edge" means in this context, listing three common characteristics that edge deployments may share:
- A distributed model of management, intelligence and networks
- Applications, workloads and hosting closer to users and digital assets that are generating or consuming the data, which can be on-premises and/or in the cloud
- Software defined (which can mean the dominant use of private, public, or hybrid cloud environments; however, this does not rule out on-premises environments)
Coincidentally, there are also three things the company wanted to understand through its research:
- What are the most common architectures used in edge networks?
- What are the most common use cases of these architectures?
- What is the perceived risk and perceived benefit of the common use cases?
That last item may pique the most interest, however, as security is always top-of-mind in enterprises and organizations these days, as all days.
"Our research shows that edge deployments have surprising momentum despite a high concern of 'perceived risk' among organizations globally," the company's Theresa Lanowitz said in a Jan. 25 blog post announcing the report. "Security is a critical success factor for edge initiatives."
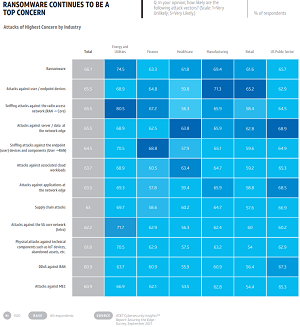
Foremost of those perceived risks is ransomware, said the report, which breaks down data into specific industry categories like healthcare and so on.
"Ransomware was rated highest in concern. Ransomware is perceived as the most likely objective of attack overall across verticals and regions. Ransomware is rated highest by energy and utilities (75 percent) and the lowest by healthcare (62 percent)."
 [Click on image for larger view.] Ransomware Continues To Be a Top Concern (source: AT&T).
[Click on image for larger view.] Ransomware Continues To Be a Top Concern (source: AT&T).
"Within industries, the least worrisome are supply chain attacks, attacks against 5G core (telco), physical attacks, DDoS attacks against the RAN and attacks against MEC, although these are highly represented overall," the report continued. "Since supply chain attacks enable other attacks, supply chain isn't always thought of as a standalone attack vector. If the goal is exfiltration of data at the edge, supply chain attacks often are a conduit to ease that exfiltration.
"Whether perceived risk is viewed by likelihood of frequency and impact or attack vector, respondents across regions and industries express concern to varying degrees. This reality validates the need for discussion and decisions about cybersecurity controls as a core part of edge adoption."
Luckily, the report has a whole section devoted to those cybersecurity controls. AT&T said choosing what controls to employ -- based on a risk assessment -- might be one of the most challenging tasks in cybersecurity.
In this report, the use of secure access service edge (SASE) architectures is prominent, as in many recent cybersecurity reports. This rising star in the security space was coined by research firm Gartner, describing a way to simplify wide-area networking and security by delivering both of those as a cloud service directly to the source of connection instead of the enterprise datacenter, according to Wikipedia.
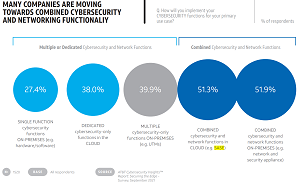
As the AT&T graphic below shows, SASE is part of a move toward combined cybersecurity and networking functionality. This trend was recently explored by Virtualization & Cloud Review in the article "Networking/Security Convergence with SASE Marked in New Report."
 [Click on image for larger view.] Moving to Combined Cybersecurity/Networking Functionality (source: AT&T).
[Click on image for larger view.] Moving to Combined Cybersecurity/Networking Functionality (source: AT&T).
In the new report, AT&T said, "The latest innovation in the controls arena is the secure access service edge (SASE) solution currently on the radar of many organizations across industries. SASE combines network and security capabilities in a cloud architecture, but no single vendor offers a complete SASE solution. Currently, about the same number of respondents are interested in either deploying an on-premises solution that mirrors the security plus network capabilities and/or deploying a similar solution in the cloud (SASE).
"In fact, from the two survey options of combined network and security in the cloud (SASE) and on-premises network plus security, SASE is preferred nearly equally by line of business and IT security stakeholders -- a pointer to a potential lockstep approach. Most customer segments show a preference for SASE except for the smallest firms, which prefer SASE the least. Networking interoperability with cloud security in a multivendor environment can create challenges that will need to be solved as organizations move to SASE."
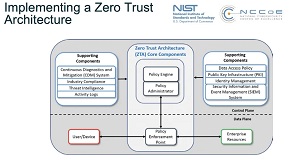
Also figuring prominently in the AT&T report is Zero Trust, another security approach often mentioned with SASE, as explained in the article "What's the Future of Network Security? Zero Trust, SASE & Automation." The Zero Trust model eschews the standard security approach of walling off networks and systems behind a secure perimeter. It's one of the latest security darlings in an industry that has seen the advent of hybrid work models, the proliferation of endpoints and bring-your-own devices, disparate and interconnected systems spanning clouds and enterprise datacenters, and just general complexity all around. Instead of trying to secure perimeters, Zero Trust assumes that such fortress security approaches are destined to fail and that systems have already been penetrated, seeking to lessen the damage that can be caused.
 [Click on image for larger view.] Zero Trust Architecture (source: NIST).
[Click on image for larger view.] Zero Trust Architecture (source: NIST).
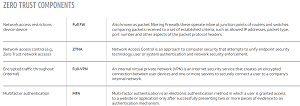
"Zero Trust for networks, a key security consideration within edge networks, encompasses device firewalls, full VPN, and the network side of network access control," the AT&T report said. "This approach extends traditional firewall and VPN capabilities into the more granular device-to-device firewalls, full internal VPN and network segmentation of a Zero Trust approach. Zero Trust is most popular in industrial IoT environments. Both cloud and IIoT networks are more dynamic than other networks and often have shared tenancy, making them ripe for Zero Trust."
 [Click on image for larger view.] Zero Trust Components (source: AT&T).
[Click on image for larger view.] Zero Trust Components (source: AT&T).
Both SASE and Zero Trust were espoused in one of the edge implementation recommendations offered up by AT&T in the report: "Emphasize the importance of security by design throughout all stages of edge network discussions and use case implementation. Leverage legacy controls where they are effective, but keep up with next-generation approaches such as Zero Trust and SASE that are designed for 5G and edge."
Other key takeaways from the report as summarized by AT&T include:
- Edge is driving a distributed architecture in terms of applications, connectivity and networking. Ideally, architecture is resilient -- continuous, automated and seamless. But this doesn't mean rip and replace. A hybrid approach that includes legacy cellular, 5G, wireless and cloud makes sense for the foreseeable future.
- Edge use cases are plentiful and varied throughout industries and geographic regions. Survey findings indicate surprising momentum, despite considerable perceived risk of deploying and securing edge computing. Each industry will have multiple types of edge, and workloads will need to adjust to different types of data flow activity. The edges and workloads call for security strategies that cross locations, platforms and partners.
- Assume that traditional security controls, such as firewalls are still relevant, but in a different, next-generation form. Secure access service edge (SASE) is in the spotlight, and SASE is on the radar of all industries surveyed.
- Edge can bring network and security closer together. Compared with legacy security controls, edge security controls need to provide broader, more centralized visibility across the entire attack surface. Threat intelligence and threat detection and response capabilities provide the necessary macro view.
- Edge cloud-delivered security will be increasingly led by automation and artificial intelligence (AI) analysis, which directs policy and response.
- Data location and security go hand in hand. Consider both in the context of an organization's systems, strategies, compliance requirements and risk tolerance. Consider where data is stored, where data should be stored and how data should be protected at rest and in transit.
- Expect to invest broadly and holistically in cybersecurity controls to secure the entire network and IT systems, of which edge is increasingly a part.
The report is based on a survey of 1,520 security practitioners from the around the world conducted in September 2021. Respondents came from organizations with more than 1,000 employees, except for the public sector and energy and utilities verticals. Respondents had direct knowledge of their organizations' edge network plans or had decision-making responsibilities related to securing the edge as well as direct knowledge of IoT, cloud, edge and MEC and Zero Trust.
About the Author
David Ramel is an editor and writer at Converge 360.