News
After Vendor Hype, Forrester Publishes Its Own Definition of 'Zero Trust'
Decrying "hype" and a "highly subjective, self-serving perspective" shaping of the term Zero Trust by security vendors, the analyst firm that first coined the term, Forrester Research, has published its own definition.
Many sources say Zero Trust originated from former Forrester analyst John Kindervag, though Wikipedia says he "(re)popularized" the term that was actually coined in 1994 by by Stephen Paul Marsh for a doctoral thesis.
Whatever the case, Forrester has been attributed by many as the originator of the security model in its modern context.
And now the firm is taking back the definition of the term from vendors, who basically provided their own definitions because Zero Trust research and guidance was mostly only available behind the Forrester paywall, accessible only to clients.
Forrester analysts David Holmes and Jess Burn offered up the new definition -- out in front of the paywall -- in a Jan. 24 blog post titled "The Definition Of Modern Zero Trust." The post notes a dichotomy in which Zero Trust is seen as both a de facto cybersecurity approach while also being called "just a marketing ploy."
"Part of the problem, according to John Kindervag, former Forrester analyst and author of the original Zero Trust research, was that the trilogy of Zero Trust papers remained largely behind the Forrester paywall," the analysts said. "For over a decade, only Forrester clients and every security vendor in the world had access. The hype train left the station, with those vendors shaping the Zero Trust narrative from their highly subjective, self-serving perspective. Nonclients and the greater cybersecurity community only saw Zero Trust through the the stained-glass windows of vendor marketing.
"Forrester's research advanced the Zero Trust concept from network-focused to an integrated, dynamic ecosystem of security capabilities and technologies with the introduction of Zero Trust Extended (ZTX). But analysts are not necessarily marketers (despite our vociferous opinions on the practice), and the research lacked a clear, concise, shareable definition our clients and the larger community could use as a stake in the ground."
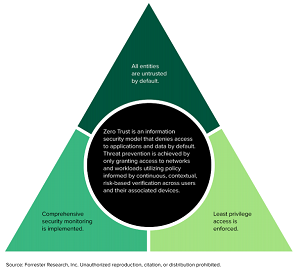 [Click on image for larger view.] Zero Trust (source: Forrester Research).
[Click on image for larger view.] Zero Trust (source: Forrester Research).
That stake says Zero Trust is:
Zero Trust is an information security model that denies access to applications and data by default. Threat prevention is achieved by only granting access to networks and workloads utilizing policy informed by continuous, contextual, risk-based verification across users and their associated devices. Zero Trust advocates these three core principles: All entities are untrusted by default; least privilege access is enforced; and comprehensive security monitoring is implemented.
In bullet points, that equates to:
- Default deny
- Access by policy only
- For data, workloads, users, devices
- Least privilege access
- Security monitoring
- Risk-based verification
Forrester said its definition is close to that of NIST (National Institute of Standards and Technology).
The Forrester analysts also describe what isn't Zero Trust and offer this in conclusion: "One more time for those in the back: Zero Trust is an information security model, one that can be worked toward but without an ultimate end state."
For comparison with vendor definitions, here's the first three paid results for an internet search of "Zero Trust is" (note that these aren't offered as official definitions from anyone -- they're just the results of an internet search):
ExtraHop: Zero trust articulates a vision for highly effective and flexible security in a de-perimeterized world where devices within the corporate network are no longer to be blindly trusted. Instead, users and devices are dynamically and continuously authenticated and verified, with access to resources restricted according to "least privilege" principles. Networks are segmented to further limit potential wrongdoing (lateral movement) and support granular access policies. Zero trust is all about following the mantra of "never trust, always verify," which means assuming a breach has already occurred. Typical technologies used to support projects include identity and access management (IAM), end-to-end encryption and micro-segmentation.
Akami: Zero Trust is a network security model based on a strict identity verification process. The framework dictates that only authenticated and authorized users and devices can access applications and data. At the same time, it protects those applications and users from advanced threats on the internet.
CrowdStrike: Zero Trust is a security framework requiring all users, whether in or outside the organization's network, to be authenticated, authorized, and continuously validated for security configuration and posture before being granted or keeping access to applications and data. Zero Trust assumes that there is no traditional network edge; networks can be local, in the cloud, or a combination or hybrid with resources anywhere as well as workers in any location.
About the Author
David Ramel is an editor and writer at Converge 360.