News
Federal Security Agency Orders Emergency VMware Patching
The Cybersecurity and Infrastructure Security Agency (CISA) issued a May 18 emergency directive to all Federal Civilian Executive Branch agencies to mitigate vulnerabilities found in a slate of VMware offerings.
Affected software includes:
- VMware Workspace ONE Access (Access)
- VMware Identity Manager (vIDM)
- VMware vRealize Automation (vRA)
- VMware Cloud Foundation
- vRealize Suite Lifecycle Manager
"These vulnerabilities pose an unacceptable risk to federal network security," said CISA Director Jen Easterly in a news release. "CISA has issued this Emergency Directive to ensure that federal civilian agencies take urgent action to protect their networks. We also strongly urge every organization -- large and small -- to follow the federal government's lead and take similar steps to safeguard their networks."
CISA Emergency Directive 22-03 orders agencies to mitigate the vulnerabilities by 5 p.m. EDT, May 23, 2022.
"CISA has determined that these vulnerabilities pose an unacceptable risk to Federal Civilian Executive Branch (FCEB) agencies and require emergency action," the directive said, based on the confirmed exploitation of two vulnerabilities by threat actors in the wild and the likelihood of future exploitation of two other vulnerabilities. The emergency directive cited the prevalence of the affected software in the federal enterprise, along with the high potential for a compromise of agency information systems.
If exploited, various vulnerabilities could permit attackers to execute remote code on a system without authentication and elevate privileges, specifically by: triggering a server-side template injection that may result in remote code execution; escalating privileges to "root"; and obtaining administrative access without the need to authenticate.
Agencies must enumerate all instances of impacted products and then either deploy security updates as detailed in VMware's VMSA-2022-0014 advisory issued on May 18 for VMware Workspace ONE Access, Identity Manager and vRealize Automation, or remove the enumerated instances until updates can be applied.
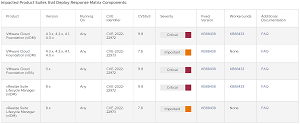 [Click on image for larger view.] Impacted Product Suites that Deploy Response Matrix Components (source: VMware).
[Click on image for larger view.] Impacted Product Suites that Deploy Response Matrix Components (source: VMware).
Then, agencies must report status of all instances by 12 p.m. EDT Tuesday, May 24, 2022.
CISA said:
These required actions apply to agency assets in any information system, including an information system used or operated by another entity on behalf of an agency, that collects, processes, stores, transmits, disseminates, or otherwise maintains agency information.
For federal information systems hosted in third-party environments each agency is responsible for maintaining an inventory of its information systems hosted in those environments (FedRAMP Authorized or otherwise) and obtaining status updates pertaining to, and to ensure compliance with, this Directive. Agencies should work through the FedRAMP program office to obtain these updates for FedRAMP Authorized cloud service providers and work directly with service providers that are not FedRAMP Authorized.
For its part, the agency also said:
- CISA will continue to work with our partners to monitor for active exploitation associated with these vulnerabilities and will notify agencies and provide additional guidance, as appropriate.
- CISA will provide technical assistance to agencies who are without internal capabilities sufficient to comply with this Directive.
- By June 30, 2022, CISA will provide a report to the Secretary of Homeland Security, the National Cyber Director, the Director of the Office of Management and Budget, and the Federal Chief Information Security Officer identifying cross-agency status and outstanding issues.
About the Author
David Ramel is an editor and writer at Converge 360.