News
Study Finds Human Error Causes Pervasive Kubernetes Security Incidents
A new report on Kubernetes security found pervasive attacks that are hindering innovation, delaying application rollouts and causing other problems, many of which can be traced to human errors.
One statistic in this month's The State of Kubernetes Security for 2022 report from Red Hat is that 93 percent of 300 DevOps, engineering and security professionals who were surveyed reported experiencing at least one security incident in their Kubernetes environments in the past 12 months, sometimes resulting in lost revenue or customers (reported by 31 percent of respondents).
Reasons for that are varied, said Red Hat, listing:
- A lack of security knowledge about containers and Kubernetes
- Inadequate or unfit security tooling
- Central security teams unable to keep up with fast-moving application development teams
"Similar to previous years, security remains one of the biggest concerns around container adoption," Red Hat said in a May 17 post about the report. "New technologies can create unforeseen security challenges when integrated with traditional IT environments, and containers present particular complexities given that their security needs stretch across all aspects of the application lifecycle, from development through deployment and maintenance. The report found that concerns around security threats to containers and a lack of investment in container security is the number-one most common concern with container strategies for 31 percent of respondents."
 [Click on image for larger view.] Biggest Concerns About Containers (source: Red Hat).
[Click on image for larger view.] Biggest Concerns About Containers (source: Red Hat).
Other top concerns include slow pace of progress (listed by 22 percent of respondents) and the ever-present skills gap (20 percent).
One major class of security incidents, data breaches, is said to be self-inflicted.
"A recent study revealed that human error was a major contributing factor in 95 percent of breaches," the report said. "Kubernetes and containers, while powerful, were designed for developer productivity, not necessarily security. Default pod-to-pod network settings, as an example, allow open communication to quickly get a cluster up and running, at the expense of security hardening. Not surprisingly, nearly 53 percent of respondents have experienced a misconfiguration incident in their environments over the last 12 months. 38 percent have discovered a major vulnerability, and 30 percent said they have suffered a runtime security incident. Lastly, 22 percent said they had failed an audit."
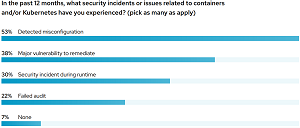 [Click on image for larger view.] Security Incidents (source: Red Hat).
[Click on image for larger view.] Security Incidents (source: Red Hat).
"Organizations are eagerly adopting containers and Kubernetes and investing in the cloud-native ecosystem to foster innovation and growth," Red Hat said. "If they do not make the necessary investments in security strategies and tooling simultaneously, they risk the security of their critical applications and may even need to delay application rollout."
Other highlights of the report as presented by Red Hat include:
- 57 percent worry the most about securing workloads at runtime
- 51 percent require developers to use validated images
- 43 percent consider "DevOps" as the role most responsible for Kubernetes security
- 78 percent have a DevSecOps initiative in either beginning or advanced stages
- 55 percent delayed or slowed down application deployment due to security concern
Red Hat also provided four tips for achieving better security, summarized as:
- Use Kubernetes-native security architectures and controls. Kubernetes-native security uses the rich declarative data and native controls in Kubernetes to deliver several key security benefits. Analyzing the declarative data available in Kubernetes yields better security, with risk-based insights into configuration management, compliance, segmentation, and Kubernetes�specific vulnerabilities.
- Security should start early but extend across the full life cycle, from build/deploy to runtime. Security has long been viewed as a business inhibitor, especially by developers and DevOps teams whose core mandates are to deliver code fast. With containers and Kubernetes, security should become a business accelerator by helping developers build strong security into their assets right from the start.
- Require portability across hybrid environments. With most organizations deploying containers in both on-premise and public cloud environments (sometimes in multiple clouds), security must apply consistently wherever your assets are running. The common foundation is Kubernetes, so make Kubernetes your source of truth, your point of enforcement, and your universal visibility layer so you have consistent security.
- Transform the developer into a security user by building a bridge between DevOps and Security. Given most organizations expect DevOps to run container security platforms, your security tooling must help bridge Security and DevOps. To be effective, the platform must have security controls that make sense in a containerized, Kubernetes-based environment. It should also assess risk appropriately.
Regarding that last point, Red Hat said, "Security has long been viewed as a business inhibitor, especially by developers and DevOps teams whose primary goal is to deliver code fast. With containers and Kubernetes, security should become a business accelerator by helping developers build stronger security controls into their applications right from the start.
"Despite potential security concerns, the benefits of container and Kubernetes adoption continue to outweigh the drawbacks. The key is to look for a container and Kubernetes security platform that incorporates DevOps best practices and internal controls as part of its configuration checks. It should also assess the configuration of Kubernetes itself for its security posture, so developers can focus on feature delivery."
About the Author
David Ramel is an editor and writer at Converge 360.