News
Threat Intelligence CISO Touts Zero Trust for Metaverse Security
How Zero Trust fits the bill as a security model for the emerging metaverse despite the architectural sins of our past (the internet).
For all of its uncertainties, Zero Trust is an important security solution for the emerging metaverse that's currently being built in IT shops near you.
Uncertainties exist because the Zero Trust security model, seemingly a new thing, actually dates back to 1994 and is in need of a modernization update in today's world of hybrid clouds, remote work, distributed software supply chains and digital transformations.
The more important issue, however, is that Zero Trust has emerged as a go-to security model for modern systems that are based on a flawed, insecure foundation: today's internet.
Nevertheless, despite those Zero Trust worries and speculation about what the metaverse will actually be, the darling security model is seen by some as a metaverse cybersecurity solution.
Included in that camp is Ian Thornton-Trump, chief information security officer (CISO) at Cyjax, a threat intelligence specialist based in the U.K. He shared his views in a recent half-day online summit presented by Virtualization & Cloud Review titled "Getting Started with Zero Trust Security," now available for on-demand viewing.
 [Click on image for larger view.] Zero Trust Principles (source: Microsoft).
[Click on image for larger view.] Zero Trust Principles (source: Microsoft).
"It's like everyone sees the dollar signs, but they don't see the risk," said Thornton-Trump in discussing metaverse cybersecurity with Virtualization & Cloud Review. His metaverse connection came near the end of his presentation, "Zero Trust 101: Why Zero Trust, Why Now, and Justifying Zero Trust," after he described to the audience of hundreds how Zero Trust is built on the three pillars of visibility, automation and orchestration.
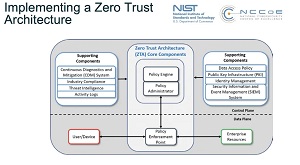 [Click on image for larger view.] Zero Trust Architecture (source: NIST).
[Click on image for larger view.] Zero Trust Architecture (source: NIST).
"Well, I'm not going to go into my presentation on, you know, NFTs and the metaverse and everything like that," he said in winding down his presentation, "but conceptually, I think that the Zero Trust framework is going to be the only thing that will be an enabling level for that metaverse, for Web 3.0, and for all the things that we've built on the shaky foundations, which is the internet itself."
And Thornton-Trump isn't the only one thinking about metaverse security even though it isn't really a thing yet.
Earlier this year, for example, Forbes discussed the metaverse in terms of new attack vectors.
"Even though the final implementation might differ from today's vision, the metaverse will certainly use technologies like augmented reality (AR), virtual reality (VR), the Internet of Things (IoT) and cryptocurrencies," the February article said. "These technologies promise to integrate and bring into alignment the physical world with digital worlds. But they will also open up new channels for cybercriminals to target businesses and individuals."
And just last week, Dean Houari, an exec at Akamai Technolgogies, discussed Zero Trust and the metaverse in an article on the ETCISO site, from an API angle.
"Given what metaverse promises to accomplish, Houari tells us how important Zero Trust is when it comes to building applications and laying the groundwork for the metaverse," the article said. "Zero Trust, he explains, essentially means that we do not trust any communication, 'regardless of whether it's network communication, authentication or someone downloading a file from the internet.' In the metaverse, any communication -- between endpoints or between applications -- will be driven through APIs. Zero Trust will be essential to secure that API communication. So whether it's for authenticating a user or validating an avatar, an API will be used to secure the transaction."
Coincidentally, "validating an avatar" was specifically mentioned by Thornton-Trump when we asked follow-up questions about his Zero Trust/metaverse connection, specifically about what makes Zero Trust a good metaverse security model.
"The 100 percent main thing is to verify continuously that it's your avatar and you're in control of it," Thornton-Trump said.
 "So if your avatar normally logs in from where you are in North Carolina, there better be some sort of security mechanisms that said that five minutes ago, he was logged in from Russia."
"So if your avatar normally logs in from where you are in North Carolina, there better be some sort of security mechanisms that said that five minutes ago, he was logged in from Russia."
Ian Thornton-Trump, Chief Information Security Officer, Cyjax
"So if your avatar normally logs in from where you are in North Carolina, there better be some sort of security mechanisms that said that five minutes ago, he was logged in from Russia. And that's a problem, right? That's the kind of thing where we need to figure out how to prevent account compromises and account takeovers in the virtual world."
Validating an avatar ties into identity considerations, a key aspect of Zero Trust and other security models. Thornton-Trump said that when people ask him what they should initially focus on when implementing Zero Trust, he suggests trying to see if they are 100 percent up to speed on identity management within their organization.
"A lot of enterprises are Multi-Factor Authentication with Single Sign On, which is in my estimation the holy grail of controlling your identity management," he said. "Maybe you've gotten visibility, like you have a grip on onboarding people and giving them the correct access. But unless it's automated, mistakes can happen. If people change rules, a lot of the problem has been inheritable permissions. So they can have one person moved to different departments, and they have keys to everything. And then, of course, if your account is compromised, you lose all that. So visibility of all of your identity information, right. Then automation of -- once that identity is created in like the payroll system or the human resources system -- automating the creation and assignment of these particular groups. And then finally, under orchestration comes the deployment of the app suitable for the person that has those roles within the organization and access to the identity. And so you can see that if you don't have the grip on identities within your organization, I would also suggest that you're going to do -- if you immediately moved to automation and orchestration -- what you really want to do is make sure your visibility is there, across all of them."
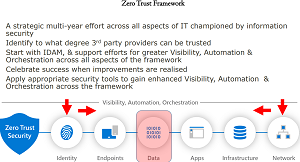 [Click on image for larger view.] The Zero Trust Framework (source: Ian Thornton-Trump).
[Click on image for larger view.] The Zero Trust Framework (source: Ian Thornton-Trump).
He offered more insights in the context of the three foundational pillars: visibility/automation/orchestration.
"We're moving beyond trust, to verify, to verify all the time," he said. "And when you see anomalous behavior [visibility], that's where we get to the automation piece of controlling what is going on in your metaverse experience. In order to prevent a very bad thing from happening to -- or, for corporation-speak, a negative outcome from your experience. And then finally, the orchestration pieces of this is how can we facilitate ... will you be able to deposit your paycheck in the physical world and automatically move a portion of that money into your metaverse so that you have currency to spend in your metaverse? How are we going to orchestrate transactions so that fraud and fraudulent behavior and those type of things are easily identified and suppressed?"
Putting on his prognostication hat, Thornton-Trump offered some views on the future, predicting a five-year event horizon for the metaverse becoming as much a part of our daily lives as email is now.
"But the actual security of a virtual environment is is a big, big task. Because fundamentally the network that the metaverse is going to run on is insecure. So we have to figure out how to build this environment where a lot of commerce is going to take place, a lot of transactions between people are going to take place. And we need to prevent criminal actors from getting there first."
"I have a feeling that it's going to be widely embraced by companies," he said. "I feel like there is going to be a host of challenges. But the actual security of a virtual environment is is a big, big task. Because fundamentally the network that the metaverse is going to run on is insecure. So we have to figure out how to build this environment where a lot of commerce is going to take place, a lot of transactions between people are going to take place. And we need to prevent criminal actors from getting there first. And we're going to have to figure out how to maintain the integrity, the security and the data protections within that space.
"And to be fair, we're doing a pretty lousy job of it right now in the real world/cyberworld/kind of the cyber part of the real world. Because in that universe, we're gonna build it on something called NFT technology, which is part of the Ethereum blockchain. And we've already seen successful cyber attacks mounted on various different aspects of the blockchain. But it comes back to fraud, and it comes back to criminal operators working in the Web 2.0 world and all of the difficulties that we're having from a regulatory perspective, but also just in tracking down those criminals and undoing the harm that they that they've done. So when we think about this virtual world that we're going to create, our challenges are, not only will we be working and operating on the original intranet protocols that are proved to be vulnerable, but we are also going to be in a scenario where the technologies that we have deployed are stop-gaps for the failures that we made during architecture in web 2.0.
"So this Zero Trust framework is actually more relevant now than ever been before. Because we have to undo the sins of the past so that we're not destined to repeat them in this new virtual world space that we're working in."
"So this Zero Trust framework is actually more relevant now than ever been before. Because we have to undo the sins of the past so that we're not destined to repeat them in this new virtual world space that we're working in. And so what does that really mean? Well, in my mind the three pillars of visibility, followed by automation, followed by orchestration, and all the underlying pieces underneath that require those things will have to be fundamentally designed into the metaverse platforms and the metaverse experiences for folks."
The bulk of Thornton-Trump's presentation saw him explaining how the three foundational pillars of Zero Trust work across the various layers of the security model, including identity, endpoints, data, apps, infrastructure and the network.
He also discussed in detail the associated tech, tactics, training and procedures (T3P):
- Content Delivery Network & Web Application Firewall Protection
- Security information and event management & Load Balancer Configuration
- Multi-Factor access controls for environments, repos and signing key management
- Software bill of materials, Integrity monitoring & vulnerability scanning
- Secure the dev environment as you would production
- Eliminate or reduce prod data in dev environment
- Disaster Recovery, Business Continuity Plan, Static Code Analysis, Dynamic Code Analysis, Open web Application Security Project Testing
- Internet Protocol Security, Virtual Private Networking & Multiprotocol Label Switching
"We need to make sure that the integrity of that metaverse system is at such a level that we can hold people accountable," Thornton-Trump told Virtualization & Cloud Review" in conclusion. "And the biggest thing in, I would say cybersecurity today, is that we're having difficulty holding organizations accountable for data breach. Unless it's so egregious and so over the line and so obvious that it's beyond reasonable doubt. So the metaverse, we're going to have to put enough cybersecurity controls using Zero Trust in order to go to move from the balance of probabilities, which is tortious levels of evidentiary requirements, into legal levels, which is beyond reasonable doubt. We have to create a beyond-reasonable-doubt metaverse or it's going to be a free-for-all for cyber crime."
While Thornton-Trump's presentation -- one of three in last week's summit -- is available for on-demand viewing, attending such events live brings the benefit of being able to ask questions of expert presenters (not to mention the chance to win a great prize). With that in mind, here's the schedule of upcoming summits: