In-Depth
Why Integrated Security Tools Are Crucial for Cybersecurity Defense
Over the last couple of years, I've written several articles here about different security tools from Microsoft. I've looked at Entra Permissions Management, Defender for Business (for SMBs), Defender for Identity, Microsoft Sentinel, eliminating bad passwords and Defender for Cloud Apps along with others.
This mimics my own journey as an IT consultant and trainer over the last five years. Asked to deliver training (in New Zealand and Singapore -- both wonderful countries to visit) on security-related Microsoft technologies starting in 2018, I had to quickly upskill. In parallel my clients were either asking for, or I was seeing, that they needed to up their security game considerably.
So now, toward the end of 2022, I have three clients on Microsoft Sentinel and one on the full Microsoft 365 E5 Security stack (with another in the works), MFA enabled for all admin accounts and for most users, and I'm not only supporting their traditional IT needs, but I'm also their one-man Security Operations Center (SOC).
In this article I'll talk about the MITRE ATT&CK framework, the cybersecurity kill chain, modern security threats and why an integrated suite of security tools is crucial for defense today.
The State of Play
You can always tell how mature a business vertical in the world is by how quickly it changes and how many new startups pop up regularly. IT overall is still a young industry (late teens?) with growing pains and as you know, it changes very quickly. But cybersecurity (as a subset of IT) is still probably pre-teens as it's changing even faster and has more startups that you can throw a VC round at.
Simultaneously, businesses are more vulnerable and major hacks are weekly (daily?) news. This morning I found out that the second-largest telco in Australia has lost potentially 9.8 million user account details, including physical addresses and driver's license details, most likely including my own.
So, if big businesses can't protect themselves, what chance do medium and small ones have? Well, as it turns out, they actually have quite a good chance, because they can be more agile, but they need awareness and understanding to get there.
ATT&CK -- A Common Language
The MITRE not-for-profit business provides many different services, across many different areas but specifically for cybersecurity they offer the free ATT&CK framework. There are matrices for Enterprise, Windows, macOS, Linux, Cloud, Network and Containers, Android, iOS and ICS systems. The most famous one is the Enterprise Matrix, which represents the different phases a cyber attack ("kill chain") might take, from Reconnaissance to Exfiltration. Each phase has numerous techniques, and sub-techniques to help you understand the different types of vulnerabilities and tactics that attackers will use.
 [Click on image for larger view.] MITRE ATT&CK Enterprise Matrix
[Click on image for larger view.] MITRE ATT&CK Enterprise Matrix
I learned about the ATT&CK framework in an excellent, free course by AttackIQ at their free AttackIQ Academy. The matrix is a great way to convey to non-technical people, including executives that a "hack" isn't just a single event that happens, it's a series of steps, and while it's important to not think of this is a list that an attacker will always follow, there are definitely choke points where you can make your defenses stronger and slow down or thwart the attackers.
The matrix also shows up in security products. Microsoft Sentinel, for instance, will categorize analytics rules, which looks for signs of attacks in log data, with the different tactics detected.
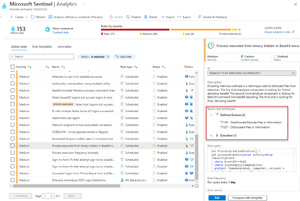 [Click on image for larger view.] Microsoft Sentinel Rule Tactics and Techniques
[Click on image for larger view.] Microsoft Sentinel Rule Tactics and Techniques
This then lets you use a workbook (=visualization dashboard) in Sentinel to ascertain which Tactics, Techniques and Procedures (TTPs) your rules cover -- and more importantly, which ones they don't. Here you can see the coverage in one of my client's Sentinel deployments.
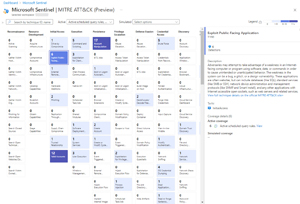 [Click on image for larger view.] MITRE ATT&CK Analytics Rule Coverage in Sentinel
[Click on image for larger view.] MITRE ATT&CK Analytics Rule Coverage in Sentinel
MITRE also tracks known groups and their TTP usage, which can be useful for attribution. It's a natural instinct to want to know who's "after you," but just be aware that it's not that important compared to making sure they're evicted and minimizing the damage.
Too Many Screens, Not Enough Eyes
Gartner recently said that 75 percent of organizations are pursuing security vendor consolidation in 2022 (compared to 29 percent in 2020), but they're not doing this primarily to drive down cost, rather to improve their security posture.
I think this is due to the simple fact that adding more security services and products doesn't necessarily make you more secure, even if a product is market leading and protects against a specific threat type. It takes time to build up expertise in each product and it takes experience to configure it correctly, and even if you do those two, the product probably doesn't integrate easily with the rest of your defenses. This last point is the crux -- attackers move too fast for defenders to manually correlate alerts in different systems: "This tool told me that this malicious links was clicked, and the email hygiene service now let me know that they'd let through these emails thinking they were OK, and the endpoint protection tool just alerted me to a malicious script running on this endpoint, and the Domain Controller tells me a weird looking Kerberos ticket was created." This is the whole point of eXtended Detection and Response (XDR), the concept of extending Endpoint Detection and Response (EDR) to different protection areas in an integrated way. There are several XDR tools on the market, either presenting as an integrated suite or as a glue between different systems to make them act as if they're integrated.
The Defender Family
A large business with a security team and budget can spend the time and effort to pick the best products for their particular threat model and integrate them and continuously improve the detections. I don't have that luxury, but I've come to know the Microsoft Defender family of product, and as mentioned earlier, this is an already-integrated suite that works for my clients.
Let's pick one client that has E5 licensing (actually, A5 since this is a K-12 school) they get:
- Defender for Endpoint P2
- Defender for Office 365 P2
- Defender for Cloud Apps
- Defender for Identity
And I've also deployed Microsoft Sentinel for them. They've got two physical Windows 2019 servers, running Hyper-V with five VMs in total, two Domain Controllers, file/print server, LOB server and Windows Server Update Services server. The servers are in separate buildings and the VMs are replicated from one to the other for DR. They use Microsoft 365 for office and collaboration, Adobe Creative Cloud for creative tools and several other cloud and on-premises applications.
There are approximately 100 laptops running Windows 10, plus 40 iPads. All of them, plus the servers, are running Defender for Endpoint, which is a complete EDR and anti-malware solution. Incoming emails are first filtered by Exchange Online Protection (EOP), which all Office 365 tenants are protected by, followed by attachment detonation in Defender for Office 365 (MDO) to ensure that malicious attachments aren't delivered. Links in emails and Teams are also scanned by MDO before a user is allowed to go to the site.
Defender for Identity (MDI) uses an agent installed on each of the Domain Controllers to look for suspicious actions or network traffic, related to Active Directory.
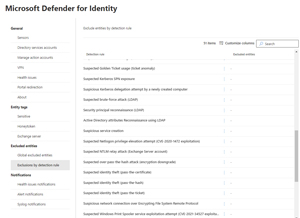 [Click on image for larger view.] Defender for Identity Detection List
[Click on image for larger view.] Defender for Identity Detection List
Defender for Cloud Apps (MDA) discovers their SaaS app usage (in this case using the Defender for Endpoint agent on each device) and compares it against a database of more than 31,000 apps to give you a list of high/medium risk app usage. MDA also lets you set up policies to control access to applications and data -- including during a session in SharePoint, for example -- plus it lets you control OAuth app usage and much more.
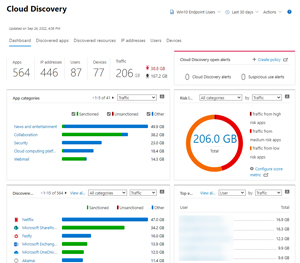 [Click on image for larger view.] Defender for Cloud Apps Discovery Dashboard
[Click on image for larger view.] Defender for Cloud Apps Discovery Dashboard
But the main strength is that all of this is surfaced in a single console, the Microsoft 365 Defender portal. Incidents and alerts from all of these security solutions are surfaced in a single place, and I can use Kusto Query Language (KQL) to hunt across the data from all of them in one place.
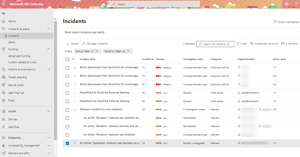 [Click on image for larger view.] Incidents in Microsoft 365 Defender
[Click on image for larger view.] Incidents in Microsoft 365 Defender
Here you can see a sample query finding AV detections across all devices in the last 30 days, and the various database tables on the left for Apps & identities, Email, Devices and so on.
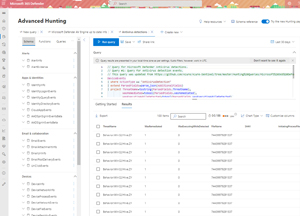 [Click on image for larger view.] Advanced Hunting in Microsoft 365 Defender
[Click on image for larger view.] Advanced Hunting in Microsoft 365 Defender
This integrated solution, with visibility across endpoints, servers, email and Teams collaboration, SharePoint/OneDrive for Business is a great solution, but what about non-Microsoft services? That brings us to the final puzzle piece: Sentinel.
A Single Pane of Glass for All Security Investigations
Microsoft Sentinel is a SaaS Security Information and Event Management (SIEM) solution that ingests data from many security solutions into a single data store and then lets you alert on potentially risky issues using Analytics rules. It also visualizes activity and data using workbooks, lets you hunt across all the data (using KQL again) and helps you by automating tasks to lighten the load on the SOC analyst. This last bit is called Security Orchestration, Automation and Response (SOAR).
It's also very easy to connect all of Microsoft 365 Defender into Sentinel and the data flows both ways, so if you close an incident in Sentinel, it's automatically closed in M365D and vice-versa.
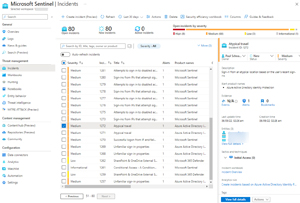 [Click on image for larger view.] Microsoft Sentinel Incidents List
[Click on image for larger view.] Microsoft Sentinel Incidents List
I do most of my investigations in Sentinel, using this graph-based approach that lets me identify each of the individual entities and their relationship while also letting me add additional information to the incident or run playbooks to present geographical information for an IP address or show whether Virus Total knows that a file is malicious.
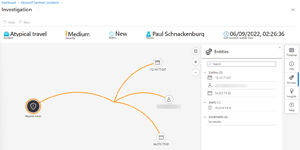 [Click on image for larger view.] Investigation in Sentinel
[Click on image for larger view.] Investigation in Sentinel
Finally, being a one-man SOC, I'm not going to sit and stare at the Sentinel portal, waiting for something bad to happen. Instead, I rely on another playbook (built on Azure Logic Apps) to send me an email whenever a new incident is generated. I can quickly triage incoming emails, and if something looks suspicious, I can click the link in the email to go do directly to the specific incident in Sentinel for further investigation.
Incidentally, knowing how to use KQL is fast becoming a required IT skill, just like PowerShell once was. Here's one good starting point, Must Learn KQL by Rod Trent.
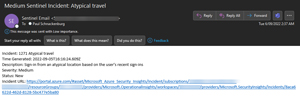 [Click on image for larger view.] Sentinel Email Alert
[Click on image for larger view.] Sentinel Email Alert
Conclusion
This was a whirlwind overview of how I've improved security visibility and investigation abilities for my clients, using Microsoft 365 Defender and Microsoft Sentinel. If you have any questions, feel free to contact me at @paulschnack.