News
VMware Advises Horizon Users to Patch for Log4j Vulnerabilities
VMware issued an "IMPORTANT" message to users of its Horizon virtual desktop offering, warning them to patch for critical Log4j vulnerabilities.
Log4j is an open source Java logging library widely used in multiple applications that's currently under a long-lasting and widespread attack because of a security vulnerability called "Log4Shell" (CVE-2021-44228) that can enable remote code execution. The FTC explains it here.
VMware's message was distributed on Monday, Jan. 24, three weeks after NHS Digitial published the article "Log4Shell Vulnerabilities in VMware Horizon Targeted to Install Web Shells." The NHS Digital article reads:
An unknown threat group has been observed targeting VMware Horizon servers running versions affected by Log4Shell vulnerabilities in order to establish persistence within affected networks.
The attack likely consists of a reconnaissance phase, where the attacker uses the Java Naming and Directory InterfaceTM (JNDI) via Log4Shell payloads to call back to malicious infrastructure.
Once a weakness has been identified, the attack then uses the Lightweight Directory Access Protocol (LDAP) to retrieve and execute a malicious Java class file that injects a web shell into the VM Blast Secure Gateway service.
The web shell can then be used by an attacker to carry out a number of malicious activities such as deploying additional malicious software, data exfiltration, or deployment of ransomware.
In it's message to Horizon users, VMware said:
Your company is using on-premises VMware Horizon products that are vulnerable to critical Apache Log4j/Log4Shell vulnerabilities unless properly patched or mitigated. Your IT team should take immediate action to address this issue because unpatched Horizon environments are being actively targeted and compromised through the industry-wide Apache Log4j/Log4Shell vulnerabilities. Business disruption, ransomware, theft and extortion are possible outcomes for any unprotected environment.
VMware has provided patches and workarounds that protect your environment from the industry-wide Log4j/Log4Shell exploits. These fixes are available in our security advisory, VMSA-2021-0028, for all internal and external Horizon components, including Horizon Connection Server, Horizon Agent, Horizon Cloud Connector, and VMware Unified Access Gateway.
While the message that was sent to Virtualization & Cloud Review mentioned only Horizon as a target, VMware's related guidance mentions many more products.
The company warned that organizations that haven't patched or used the latest workarounds since Dec. 19, 2021, (after the Apache Log4j maintainers updated their guidance) may already be compromised, providing directions on what to do in that case.
"SaaS customers have had their cloud environments updated to resolve Log4j vulnerabilities and already received maintenance notifications through their service support channels. However, on-premises components that are not managed by VMware should also be assessed and patched as soon as possible," VMware said.
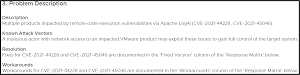 [Click on image for larger view.] Part of VMware's VMSA-2021-0028.9 Advisory (source:VMware).
[Click on image for larger view.] Part of VMware's VMSA-2021-0028.9 Advisory (source:VMware).
The company warned that organizations that haven't patched or used the latest workarounds since Dec. 19, 2021, (after the Apache Log4j maintainers updated their guidance) may already be compromised, providing directions on what to do in that case.
"SaaS customers have had their cloud environments updated to resolve Log4j vulnerabilities and already received maintenance notifications through their service support channels. However, on-premises components that are not managed by VMware should also be assessed and patched as soon as possible," VMware said.
The issue is explored in great detail, including a FAQ, in the post "VMSA-2021-0028: Questions & Answers about Log4j."
About the Author
David Ramel is an editor and writer for Converge360.