In-Depth
Microsoft Ignite 2023: Highlights for Security-Conscious IT Pros
Microsoft this month held its largest conference, Ignite, this time with about 4,500 attendees on site, and myself plus another 175,000 or so IT pros and developers connecting online.
I've digested about 20 session recordings so far, and in this article I'll take you through my personal highlights, promising it won't be all about AI and Copilots.
I'll look at the changes coming in the Defender suite of security products, Windows Server v.Next and SharePoint.
Security Everywhere
If it hasn't been clear in the dozen or so articles I've written here over the last few years, Microsoft is serious about the security product/service market. They've now got tools for: collaboration security; endpoint security (all OS platforms); IoT and OT; identity; Software-as-a-Service (SaaS) cloud apps; Platform-as-a-Service (PaaS) and Infrastructure-as-a-Service (IaaS) across all three hyperscale clouds; Threat Intelligence; and a SIEM to tie all of those -- and third-party data sources -- together.
It wouldn't be a Microsoft event if products didn't have a branding name change, and this time was no exception, Microsoft 365 Defender is now Microsoft Defender XDR, which actually makes more sense.
While there's been steady progress on integrating the different Defender products into a single console (security.microsoft.com), the Defender for Cloud product, which does IaaS and PaaS protection for Azure, GCP and AWS, was separate. But as Microsoft and many others have found, attackers happily pivot from one compromised environment inside an organization to another, so cloud workload alerts, signals and asset information from Defender for Cloud will be surfaced in Defender XDR.
Another fundamental change is the move of Sentinel into the Microsoft XDR console, with the new home at defender.microsoft.com. This is rolling out in private preview shortly for orgs that are members of the security Customer Connection Program (CCP). This will not only create a single console for all XDR and SIEM activity (a "unified SOC"), but you'll also be able to do advanced hunting across the data from both locations.
In Defender for Endpoint (MDE) I took note of the plug-in for Windows Subsystem for Linux, plugging an existing hole, especially for developer devices. The reduction of the number or URLs that need to be allow-listed for outgoing connectivity from devices to the cloud service is also welcome and will ease deployments. Not specifically announced at Ignite, but now generally available, is the ability to configure settings for endpoints directly in the security portal, as an alternative to setting them in Intune. This is especially handy when the security team has no access to the Intune portal.
Two other improvements in MDE worth mentioning are automated attack disruption and inbuilt deception. The first one uses signals from all the XDR components to identify human-operated ransomware (HuMOR -- although it's not funny), Business Email Compromise (BEC) or Attacker-in-the-Middle (AitM) exploits and automatically isolate infected devices or disable compromised accounts. This is an increasingly important feature as attackers can take advantage of a malicious link in an email being clicked to start moving laterally as quickly as within five minutes (and complete the entire attack chain in two hours), so even if defenders are monitoring alerts, they may not block the attackers quickly enough.
The second feature uses AI (minimizing the manual effort usually associated with creating and maintaining deception tokens) to generate decoys, fake user accounts and hosts, along with lures such as documents and files to lead attackers to the decoys. Since ordinary user activity should never see or touch these fakes, alerts raised are a high-fidelity signal that an attacker is on the network.
A sobering statistic was that 70 percent of ransomware attacks that Microsoft sees targets SMBs with fewer than 500 staff.
Microsoft Defender Threat Intelligence (MDTI), a service I wrote about here, is now integrated into the security portal through the Intel profiles, Intel explorer and Intel projects blades. As it's definitely priced for enterprise use, it's heartening to see that there's a free experience, including Indicators of Compromise (IoCs) that can be used in Sentinel. There used to be a community edition (also free) of MDTI, and I'm curious to see if the free experience provides more or less than that one did.
 [Click on image for larger view.] Intel Explorer in the Security Portal
[Click on image for larger view.] Intel Explorer in the Security Portal
Windows Server v.Next
As an IT pro whose world revolved around Windows Server for decades (installed my first server, Windows NT 3.51, in the mid-90s), it's been disheartening to see the focus of Microsoft shift so squarely to the cloud, and more recently onto Azure Stack HCI. This new flavor has been receiving all the attention and new features over the last few years, and as it's licensed by subscription, on a per-core basis, it's not really the same Server that I used to love. This might be about to change.
A single session (delivered by two older gentlemen, a telling sign) showed some of what's coming in the next version of Windows Server, now called v.Next, but I'd guess it'll be 2025 (last one was 2022, the one before that 2019). And there's quite a few things to be excited about.
Hotpatching is something Microsoft uses in Azure extensively, applying patches to a running OS without having to reboot the host. So far, it's only been available for customers through the "Windows Server Azure Edition" -- server Core flavor. The new version offers this for bare metal, virtual and cloud-hosted (including non-Azure) installations for both Core and Server with a Desktop. The trick is they need to be Arc enabled, but at this point that gives you so many other benefits that the monthly fee is definitely worth it. An example they gave was the Xbox online team taking about three weeks to roll out monthly patches across their 1,000 servers pre Hotpatching, and now completing the same process in less than 48 hours.
Another feature, SMB over the Quic protocol, was only available in the Azure edition of Server and will now be coming to all flavors. Essentially this allows you to securely connect to file shares from outside the corporate network, without requiring a VPN, from Windows clients, as well as Android and presumably Macs eventually.
The proliferation of NVMe storage devices in modern servers (and in Azure) has prompted Microsoft to redesign the interface to it -- providing a 70 percent speed increase. They're also working on a custom NVMe driver that provides 90 percent speed increase for storage in its preview form today. There's also support for NVMe over Fabric (remote storage/SAN) with a new initiator.
Active Directory will get performance increases, moving to a 32K page size for the database, NUMA support on Domain Controllers for larger servers, and security enhancements. These include using TLS 1.3 for LDAP connections, SHA-256 and -384 in Kerberos, brute force throttling and more.
The file system deduplication built into the Resilient File System (ReFS) has so far been optimized for cold storage such as virtual hard disk template files, for one example. The new version is better for open files that are in use, such as virtual disks for running virtual machines (VMs).
Clustering will provide dynamic processor compatibility, particularly useful where you add additional hosts to an existing Hyper-V cluster, but the generation of CPUs that your existing hosts run is no longer available. It'll automatically analyze all the CPUs and mask out features that are only available on the newer hosts, ensuring that you can Live Migrate and failover VMs to any host.
Currently we can "pipe" a whole GPU into a VM using Discrete Device Assignment (DDA). This doesn't work with failover clustering or Live Migration however, and also limits scalability as that GPU "disappears" from the host OS. Borrowing from its Azure Stack HCI brother, v.Next will let you do GPU partitioning so you can divide up a GPU across say four VMs. This also works with clustering and Live Migration (as long as there's GPU capacity available on the new host).
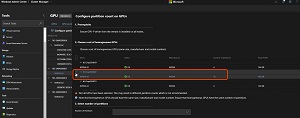 [Click on image for larger view.] Partitioning an NVIDIA A2 GPU in Windows Admin Center (source: Microsoft).
[Click on image for larger view.] Partitioning an NVIDIA A2 GPU in Windows Admin Center (source: Microsoft).
Oh, and the cutest thing -- based on customer feedback -- is the inclusion of Wi-Fi and Bluetooth interfaces in Windows Server, particularly handy for smaller servers placed in edge scenarios, for example, where wired ethernet may not be available.
SharePoint Premium
I've been disappointed with the licensing direction Microsoft has been taking over the last few years, adding features to existing products (Intune and Teams come to mind), offering them in preview to make people excited and then bundling them into an add-on package for an extra licensing fee. So when I heard that SharePoint Premium was coming I thought, "here we go again." However, it's actually more of a rename of the existing technology known as Syntex, which uses AI to analyze, organize and govern your document repositories. There are three major buckets to Premium: content experiences, content processing and content governance.
In the first bucket is a new integrated file viewer that supports more than 400 file types, letting you ink digitally, or add comments/mentions to any file. There's also a new Business Documents app for Teams, which tracks contracts and other high-value docs, and a new AI rules deviation engine to flag changes to contract text, for example. The ability to digitally sign documents with Microsoft's own SharePoint eSignature is cool; they're also integrating Adobe Sign and DocuSign if you'd rather use them.
There's also Document Portal, an externally accessible site, which lets external users (with consumer accounts if you allow that) collaborate on documents or access contracts and so on, and sign them.
Most organizations have a sprawling estate of SharePoint online sites, making governance of sharing permissions hard. The new Data Access Governance (DAG) looks at sharing policies, Teams-connected sites and sensitivity labels, and suggests improvements. You can also run site access review, which is similar to an existing feature in Entra ID where group owners can be asked to verify that members should still have access, in this case checking in with site owners and asking them to review user access.
There's also Microsoft 365 Archive (now in public preview), which lets you manage the lifecycle of sites, archiving them when they've no longer needed while they still remain available for regulatory compliance or other access through eDiscovery.
Microsoft 365 Backup will be coming to a paid preview soon, and will go GA in the first half of 2024. This is from the company that has been saying for the last decade that "you don't really need backup of your M365 data, we'll keep it safe," finally admitting that data resiliency isn't the same thing as data backup. Whilst this feature has the support of third-party backup vendors, note that Teams chat backup and granular file-level recovery are not part of this first version.
The enhancements in OneDrive for Business (OD4B) are probably going to the ones that most readers will notice in their own lives, with a new Home page (available not only in OneDrive but also in Teams and Outlook), a Meetings view (where did that recording go?) and a People view (I don't remember the name of the file, but I know who shared it with me). And, of course, Copilot is coming to OD4B as well. There's a new migration feature to move OD4B sites between tenants, collaboration insights to see who's sharing what with whom to keep data leakage risks down, and for consumer OneDrive you'll be able to search through photos using natural language.
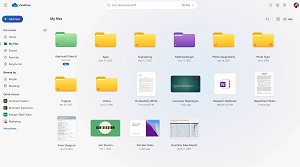 [Click on image for larger view.] The New OneDrive for Business Home Page (source: Microsoft).
[Click on image for larger view.] The New OneDrive for Business Home Page (source: Microsoft).
Other Noteworthy Mentions
Among the few announcements that don't fit into the categories above are the Maia and Cobalt processors, the first one being an "AI Accelerator chip" to run cloud-based training and inferencing, whereas Cobalt is an ARM chip optimized for performance, power efficiency and cost-effectiveness for general purpose (provided they can run on ARM architecture) workloads. In general Microsoft has open sourced their server designs used in Azure for many years, and now they're designing the processors themselves for the best optimization of performance per watt. Oh, and they're liquid cooled by a sidekick in the wider-than-normal server rack.
Something less future looking is Azure Boost, a true "child of the cloud era" technology. This offloads storage and networking traffic from the host OS and the hypervisor to purpose-built software (on a secure Linux core) and hardware -- the Azure Boost card. Note that this performance will be available for new VM SKUs going forward, but this preview has a limited set of sizes in which it's available now. You can resize an existing VM to one of the supported sizes.
Of course, this Ignite was also the birth of Microsoft as an AI company, with AI announcements and Copilot sessions galore. My focus is on Microsoft Security Copilot, which really does look like a game-changer, but I suspect the cost will be a barrier once that's revealed. It's one of the first private previews (Early Adopters Program) that Microsoft is charging for, so that's one clue. I'm looking forward to seeing and hearing more about it and eventually getting my hands on it myself.
Conclusion
There were a lot more noteworthy announcements that caught my eye, particularly in the Purview space as data governance will be key for successful Microsoft 365 Copilot deployments for example, but I'm out of space.
For those wanting to learn more about Microsoft's big IT pro/developer event, 617 sessions are available for replay here, and the Ignite Book of News is here.