News
Mandiant Sees Ransomware Increasingly Attacking Virtualization Platforms
Threat intelligence specialist Mandiant has noticed ransomware actors have been increasingly attacking virtualization platforms in their efforts to extort organizations for money.
While many similar cybersecurity reports have noted the increase of ransomware in general, new tactics and corporate-like organization among bad actors, the virtualization angle is new to the mix.
"Financially motivated attackers are increasingly targeting virtualization environments with ransomware, and there are strategies that can be implemented to mitigate risk," said Mandiant in announcing M-Trends 2022, the latest edition of its annual report, based on data from 2021. As the report explains, wares from virtualization kingpin VMware are prime targets.
"In 2021, Mandiant observed ransomware attackers using new tactics, techniques and procedures (TTPs) to deploy ransomware rapidly and efficiently throughout business environments," the report says. "The pervasive use of virtualization infrastructure in corporate environments creates a prime target for ransomware attackers. By accessing virtualization platforms, ransomware attackers can rapidly encrypt many virtual machines without needing to directly login or deploy encryptors within each machine. Throughout 2021, Mandiant observed VMWare vSphere and ESXi platforms being targeted by multiple threat actors, including those associated with Hive, Conti, Blackcat, and DarkSide. Several protection strategies can be implemented to mitigate risk."
Specifically, one avenue of attack that's typically uncovered in the actor's reconnaissance phase -- after initial network entry -- is the integration of Active Directory domains with vCenter Server, used to manage virtualization infrastructure.
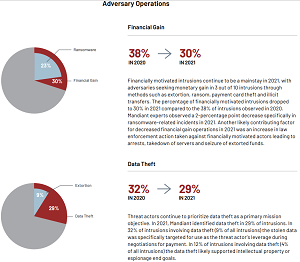 [Click on image for larger view.] Ransomware Figures Prominently in Adversary Operations (source: Mandiant).
[Click on image for larger view.] Ransomware Figures Prominently in Adversary Operations (source: Mandiant).
"Ransomware threat actors focus on this integration to identify specific Active Directory users and groups that may be provided access to login to a vCenter Server," the report explains. "Armed with the knowledge that an organization is utilizing vCenter Server, actors use compromised credentials to login to vCenter Server and discover all the ESXi hosts used in the environment. The ESXi servers are a ripe target for many actors; they need to log directly in to these servers to deploy ransomware, which impacts the availability of all virtualized hosts running on the server. Mandiant observed threat actors turning on the ESXi Shell and enabling direct access via SSH (TCP/22) to the ESXi servers to ensure that ESXi host access remains available. In addition, actors often created new (local) accounts for their use on the ESXi servers and changed the password of the existing ESXi root account to ensure the target organization could not easily regain control of their infrastructure."
As far as mitigating this virtualization attack vector, Mandiant said it is important for organizations to properly secure both the virtualization platform and access to the management interfaces, optimally by enacting multiple layers of controls to lessen the risk of ransomware threat actors being able to directly impact the virtualization infrastructure. "A very effective mitigation is the implementation of proper network segmentation by placing all management of ESXi and vCenter Server on an isolated network or VLAN. When configuring networking on the ESXi hosts, only enable Mkernel network adapters on the isolated management network."
Other highlights of the report as summarized by Mandiant include:
- Linux Malware Uptick: Newly tracked malware families effective on Linux increased to 11 percent in 2021 compared to 8 percent in 2020. Further, observed malware families effective on Linux increased to 18 percent in 2021 from 13 percent in 2020.
- More Threats: We started tracking over 1,100 new threat actors and over 700 new malware families in the past year, and there is no indication that this trend will slow down anytime soon.
- Multiple Threat Actors at Work: Whether working separately or together, more than one distinct threat group was identified in an environment for a quarter of our investigations -- a trend we expect to see increase.
- Mining a Little Deeper: The deployment of cryptocurrency coin miners by one financially-motivated threat group led to the discovery of two nation-state actors in the same environments, highlighting the need for properly scoped investigations.
- Misconfiguration Mitigations: We observed various compromises due to misconfigurations when using on-premises Active Directory with Azure Active Directory to achieve a single integrated identity solution.
"Recent cyber events are a stark reminder that our work as defenders is never done," the company said. "Critical vulnerabilities such as 'Log4Shell' highlight the dangers of the unknown and the complexity of patching. The supply chain is as attractive a target as ever, providing a potential entry point into multiple vendors. And we must remain vigilant about protecting our industrial control systems, especially given that 1 in 7 multifaceted extortion attacks leak critical operational technology information."
About the Author
David Ramel is an editor and writer at Converge 360.