News
SecOps Report: Stressed Pros Shouldn't Just Turn Off 'Noisy' Alerts (or Pay Ransom)
A new report on overstressed security pros finds many just turn off noisy, overwhelming alerts and provides more evidence that paying off ransomware attackers doesn't result in very many positive outcomes.
Those are two takeaways from the third annual "Voice of SecOps" Report from Deep Instinct, a specialist in deep learning-aided cybersecurity offerings, which polled 1,000 respondents across the US, UK, Germany and France to better understand and quantify the causes and impact of stress on the cybersecurity community. It separates results into two categories: C-suite execs and their reports.
Key highlights of the report include:
- More than 90 percent of cybersecurity professionals are stressed in their role
- Nearly half of the respondents (46 percent) have thought about quitting the industry
- Stress levels are increasing across all sectors
- The more senior the cybersecurity role, the more stressful the job
- A significant proportion of professionals concede that stress is negatively impacting their ability to do their job
- There appears to be a widespread adoption of completely counter-productive measures, such as switching off alerts because SecOps teams find them overwhelming
- Paying off the ransomware scammers in the aftermath of an attack results in trouble-free consequences in just 16 percent of cases
"The research confirms what many in the industry have long known -- that stress on Security Operations staff is acute and growing more problematic," the report said. "Long term, this has the potential to have considerable ramification for the cybersecurity readiness of organizations across the globe."
One ramification is simply that many overstressed security pros are just up and quitting, as the report indicated nearly half of respondents admitted to considering leaving the security industry as a result of high stress levels.
"So how are cybersecurity professionals coping with these stresses? For many, the answer is 'not at all well' and many are considering leaving the cybersecurity industry altogether as a result of this stress," the report said. "45 percent of respondents experiencing some stress level claimed that work stress has led them to consider leaving the cybersecurity industry on at least one occasion. (To be clear: that's not just leaving their employer -- that's leaving the cybersecurity industry altogether). At a time when it is a challenge to fill all of the open roles in cybersecurity, estimated to be 465,000 in the US alone, these statistics are very concerning."
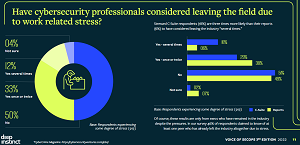 [Click on image for larger view.] Have cybersecurity professionals considered leaving the field due to work related stress? (source: Deep Instinct).
[Click on image for larger view.] Have cybersecurity professionals considered leaving the field due to work related stress? (source: Deep Instinct).
While quitting the field entirely is a drastic step, the constant stress of continually protecting IT systems from attackers also manifests itself in more mundane ways, like deciding to just not deal with the deluge of pesky security alerts, which are often false positives.
"The volume and time-intensive nature of addressing false positive alerts was a critical stressor for respondents," the report said. "74 percent claimed their volume of false positive was steady or rising (to 83 percent in Germany). C-Suite respondents were markedly less likely than their reports to see the significance of the challenge, further underscoring the divide between leaders and their direct reports. 36 percent of C-Suite respondents thought their false positive rate was in decline, but only 19 percent of their reports -- the people largely charged with dealing with them -- reported this was actually the case. Perhaps of greater concern, though, is that when we asked those with steady or rising false positive incidence rates, more than 1 in 4 respondents (26 percent) confessed that they actually 'turn off our alerts because they are too noisy.' "
Ransomware
And then there's ransomware, the bane of many a SecOps pro in the past few years as evidenced by a multitude of crippling, highly publicized major attacks like Kaseya, Colonial Pipeline and others.
Ransomware was identified as a top stressor for CISOs, along with managing security for a remote workforce, and digital transformation and its broad impacts on security posture.
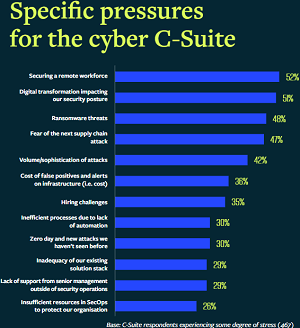 [Click on image for larger view.] Specific pressures for the cyber C-Suite (source: Deep Instinct).
[Click on image for larger view.] Specific pressures for the cyber C-Suite (source: Deep Instinct).
It was also No. 2 on the list of key threat fears.
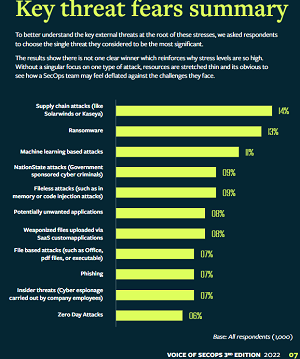 [Click on image for larger view.]Key threat fears summary (source: Deep Instinct).
[Click on image for larger view.]Key threat fears summary (source: Deep Instinct).
The study also reaffirmed findings from similar reports that found paying off ransomware attackers doesn't necessarily "pay off" for the victimized organization.
"When ransoms have been paid, things rarely went 'back to normal' -- in fact, only 16 percent of respondents had no further issues after paying a ransom post-attack," Deep Instinct said. As the following graphic shows, 38 percent of respondents said they paid attackers. Of the 38 percent who did pay, many still ended up with exposed and unrestored data or experienced another attack.
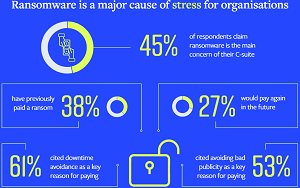 [Click on image for larger view.]Ransomware is a major cause of stress for organizations (source: Deep Instinct).
[Click on image for larger view.]Ransomware is a major cause of stress for organizations (source: Deep Instinct).
Those findings generally jive with a survey-based report titled "Ransomware: The True Cost to Business Study 2022" published by Cybereason, as detailed in last week's Virtualization & Cloud Review article "Ransomware Payouts Can Be 'A Matter of Life or Death' but 'Don't Pay' Generally Advised."
"The study also once again finds that 'it doesn't pay-to-pay' a ransom demand, as 80 percent of organizations that paid were hit by ransomware a second time, with 68 percent saying the second attack came in less than a month and 67 percent reporting that threat actors demanded a higher ransom amount," said Cybereason in a June 7 blog post.
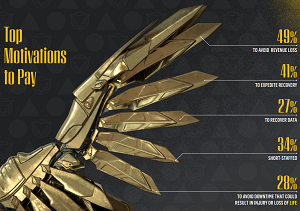 [Click on image for larger view.] Top Motivations to Pay (source: Cybereason).
[Click on image for larger view.] Top Motivations to Pay (source: Cybereason).
What's more, another recent report by data protection specialist Veeam titled "2022 Ransomware Trends Report" found that many victimized organizations paid ransoms and recovered their data. However, nearly as many either recovered their data without paying the ransom or paid the ransom and still didn't recover their data. More about that report is available in the article "Survey Shows Limits of Ransomware Insurance, Payoffs."
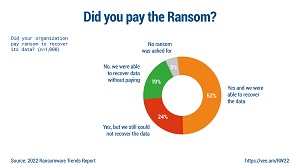 [Click on image for larger view.] Did You Pay the Ransom? (source: Veeam).
[Click on image for larger view.] Did You Pay the Ransom? (source: Veeam).
"Cybersecurity professionals are under growing pressure to defend their organizations against increasingly creative threat actors and stress levels are rising relentlessly," Deep Instinct said in conclusion. "Unsurprisingly, the more senior the position, the more stressed the executive. And these executives are stressed because of the increased complexity of the modern workforce and workplace combined with the more advanced (and potentially pain-inducing) threat landscape. It appears that being a senior cybersecurity leader has never been more challenging than today."
The deep learning cybersecurity specialist suggested that the industry needs a solution that offers AI-driven prevention and other functionality to reduce false positives and alleviate staffing issues.
About the Author
David Ramel is an editor and writer at Converge 360.