News
Feds Warn Log4Shell Exploits Still Hitting VMware Horizon, UAG Systems
VMware's many and varied cybersecurity troubles just won't go away.
The Cybersecurity and Infrastructure Security Agency (CISA) this week updated last month's advisory about threat actors continuing to exploit Log4Shell vulnerabilities in VMware Horizon and Unified Access Gateway (UAG) systems.
The update includes indicators of compromise (IOCs) -- data or evidence indicating potential system intrusions -- provided in a new malware analysis report.
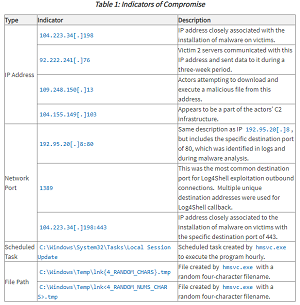 [Click on image for larger view.] Indicators of Compromise (source: CISA).
[Click on image for larger view.] Indicators of Compromise (source: CISA).
It adds information to the June 23 alert titled "Malicious Cyber Actors Continue to Exploit Log4Shell in VMware Horizon Systems," reporting on Log4Shell vulnerabilities that began to surface late last year.
Log4j is an open source Java logging library widely used in multiple applications that's currently under a long-lasting and widespread attack because of a security vulnerability called "Log4Shell" (CVE-2021-44228) that can enable remote code execution. The FTC explains it here.
After it hit VMware and other organizations hard last December, VMware provided fixes and issued an "IMPORTANT" message to users of its Horizon virtual desktop offering, warning them to patch for critical Log4Shell vulnerabilities.
This week's new malware analysis report that provides additional IOCs describes a submitted malware file: "This file is a malicious loader that contains an embedded executable. This embedded executable is a Remote Access Tool (RAT) that provides a vast array of Command and Control (C2) capabilities. These C2 capabilities include the ability to remotely monitor a system's desktop, gain reverse shell access, exfiltrate data, and upload and execute additional payloads. The malware can also function as a proxy, allowing a remote operator to pivot to other systems."
It adds to last month's alert that warned, "If updates or workarounds were not promptly applied following VMware's release of updates for Log4Shell in December 2021, treat those VMware Horizon systems as compromised."
And that's not the only cybersecurity battle that VMware has been fighting lately. In May, for example, CISA issued an emergency patching directive to all Federal Civilian Executive Branch agencies to mitigate vulnerabilities found in a slate of VMware offerings including:
- VMware Workspace ONE Access (Access)
- VMware Identity Manager (vIDM)
- VMware vRealize Automation (vRA)
- VMware Cloud Foundation
- vRealize Suite Lifecycle Manager
This week's new malware analysis report lists the following best practices recommendations to strengthen the security posture of an organization's systems:
- Maintain up-to-date antivirus signatures and engines.
- Keep operating system patches up-to-date
.
- Disable File and Printer sharing services. If these services are required, use strong passwords or Active Directory authentication.
- Restrict users' ability (permissions) to install and run unwanted software applications. Do not add users to the local administrators group unless required.
- Enforce a strong password policy and implement regular password changes.
- Exercise caution when opening e-mail attachments even if the attachment is expected and the sender appears to be known.
- Enable a personal firewall on agency workstations, configured to deny unsolicited connection requests.
- Disable unnecessary services on agency workstations and servers.
- Scan for and remove suspicious e-mail attachments; ensure the scanned attachment is its "true file type" (i.e., the extension matches the file header).
- Monitor users' web browsing habits; restrict access to sites with unfavorable content.
- Exercise caution when using removable media (e.g., USB thumb drives, external drives, CDs, etc.).
- Scan all software downloaded from the Internet prior to executing.
- Maintain situational awareness of the latest threats and implement appropriate Access Control Lists (ACLs).
VMware itself has published copious guidance and information on the Log4Shell vulnerabilities, including the post "VMSA-2021-0028: Questions & Answers about Log4j."
About the Author
David Ramel is an editor and writer at Converge 360.