News
Should Ransomware Payoffs Be Outlawed?
Generally, cybersecurity experts advise stricken enterprises to not pay off the ransom to get their IT systems and data back. Now, one country is considering making that advice actual law.
Reuters this week reported that Australia will consider making ransomware payouts illegal following last month's massive cyber attack against the country's biggest health insurer, Medibank Private Ltd., along with a series of other breaches.
Australia's Home Affairs Minister Clare O'Neil disclosed the news in a TV interview with broadcaster ABC. Reuters reported: "Asked on ABC television on Sunday whether the government planned to look at outlawing ransom payments to cyber criminals, O'Neil said 'that's correct.' "
" 'We will do that in the context of ... cyber strategy,' " she said.
Along with that, following the spate of cyber attacks, Australia on Nov. 12 announced a "Joint standing operation against cyber criminal syndicates."
"The international counter-ransomware task force will drive international cooperation and joint efforts to tackle ransomware including through information and intelligence exchanges, sharing best practice policy and legal authority frameworks, and collaboration between law enforcement and cyber authorities to conduct counter-ransomware activities," the government announcement said.
Regarding those best practices mentioned by the government, experts -- and law enforcement agencies -- generally advise organizations to not pay off ransomware.
For example, a May ransomware trends report from Veeam demonstrated the limits of ransomware insurance and payoffs, as detailed in the Virtualization & Cloud Review article, "Survey Shows Limits of Ransomware Insurance, Payoffs."
Specifically, the company's 2022 Ransomware Trends Report found that many victimized organizations paid ransoms and recovered their data. However, nearly as many either recovered their data without paying the ransom or paid the ransom and still didn't recover their data.
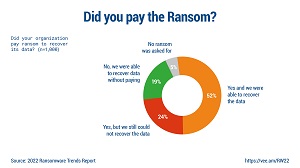 [Click on image for larger view.] Did You Pay the Ransom? (source: Veeam).
[Click on image for larger view.] Did You Pay the Ransom? (source: Veeam).
Furthermore, the Veeam report said: "One of the more notable statistics in the survey is that half (52 percent) of those with encrypted data paid the ransom and were successful in recovery. However, one in four organizations paid the ransom but were still unable to recover their data, while nearly as many were able to recover without paying a ransom."
And, just one month after that report, a survey from Cybereason reaffirmed general industry advice to not pay off the attackers, but noted that many do so when it becomes "a matter of life or death."
Those observations come with the survey-based report titled "Ransomware: The True Cost to Business Study 2022."
"The study also once again finds that 'it doesn't pay-to-pay' a ransom demand, as 80 percent of organizations that paid were hit by ransomware a second time, with 68 percent saying the second attack came in less than a month and 67 percent reporting that threat actors demanded a higher ransom amount," said Cybereason in a June 7 blog post.
Furthermore, among organizations who opted to pay a ransom demand in order to regain access to their encrypted systems, 54 percent said that some or all of the encrypted data was corrupted during the recovery process. That signified a 17 percent year-over-year increase compared with last year's report when that number was 46 percent.
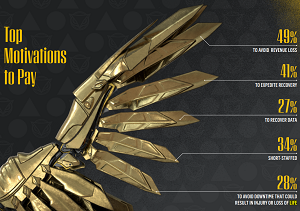 [Click on image for larger view.] Top Motivations to Pay (source: Cybereason).
[Click on image for larger view.] Top Motivations to Pay (source: Cybereason).
"These findings underscore why it does not pay to pay ransomware attackers, and that organizations should focus on detection and prevention strategies to end ransomware attacks at the earliest stages before critical systems and data are put in jeopardy," Cybereason said.
More on that report can be found in the article "Ransomware Payouts Can Be 'A Matter of Life or Death' but 'Don't Pay' Generally Advised."
Another reason not to secure insurance and pay ransomware is the hassle of actually doing so. Enterprises typically secure cyber insurance to protect against ransomware attacks, but policies usually have the provision that victimized organizations need to make the payments themselves upfront before the insurer makes a reimbursement -- provided, of course, that all the many stipulations in the "fine print" are met and all the i's are dotted and t's crossed.
Unsurprisingly, like all insurance companies, cyber insurers will do everything possible under the sun to find a way not to pay up. Insurers start up front, demanding that organizations follow specific practices regarding security, reporting and more. They require your systems be audited and pass every last metric. If something changes in an organization's IT environment and it is then found to be out of compliance after an attack, it's likely no reimbursement will be made.
Dave Kawula, managing principal consultant at TriCon Elite Consulting, is familiar with reimbursement scenarios. He shared his expertise with an audience of hundreds who attended an online summit presented last year by Virtualization & Cloud Review. To summarize, he said that while organizations can collect on ransomware insurance, the experience can get ugly.
"The good news is, most cyber insurance policy vendors that I've worked with have actually paid out in the event that it needs to happen," he said.
 [Click on image for larger view.] The High-Level Checklist
[Click on image for larger view.] The High-Level Checklist
"There is a whole process for this," Kawula continued. "I'm not gonna lie, it's not really pretty. I could say it was really awful, because cyber insurance vendors are so hammered with claims that it's taking a long time for them to react. But typically, they'll have their own SecOps, security operations teams and cyber threat analysis experts that will come in and help your organization."
More on that can be found in the article, "Collecting on Ransomware Cyber Insurance: 'It Was Really Awful.' "
Looking to other sources, Forbes in July published an article on "Why Experts Disagree On Whether Businesses Should Pay Ransomware Demands," which stated, "Despite the risks associated with paying ransomware demands, there are some who do not automatically rule it out."
Research firm Gartner was noncommittal on the subject in last year's article, "When it Comes to Ransomware, Should Your Company Pay?"
"In many cases, it is easier and cheaper to pay the ransom than to recover from backup," Gartner said. "But supporting the attackers' business model will only lead to more ransomware. Law enforcement agencies recommend not paying, because doing so encourages continued criminal activity. In some cases, paying the ransom could even be illegal, because it provides funding for criminal activity."
Indeed, it was reported by the Hunton security blog in May that "North Carolina Becomes First State to Prohibit Public Entities from Paying Ransoms," which is also under consideration by other states. Ransomware payoff limitations have even been mulled by the U.S. Congress. Now, Australia will consider a ban, of which the details are yet unknown. For example, with the only news about that initiative coming from a snippet from a TV interview, it's unknown if the country will (or can) consider extending any ban to private organizations.
Palo Alto Networks in June said average ransom payments were up 71 percent this year, approaching $1 million.
About the Author
David Ramel is an editor and writer at Converge 360.